While 99% of us were going through the ordeal of trying to work with either the Microsoft horizontal monopoly or the Apple vertical monopoly, there has been a third option growing in the weeds. Free open source tools, such as Linux, began in the early 1990s when some very forward thinking computer programmers insisted on freedom from the rigid patent structure imposed by commercial outfits like Microsoft and Apple. The free software movement began in 1984 when Richard Stallman left MIT and founded GNU in order to create free software programs. GNU is an acronym for “Gnu is Not Unix.” Richard Stallman stated that GNU is a “technical means to a social end.” The social end was freeing knowledge from the clutches of private corporate monopolies – much like Thomas Jefferson advocated for our public schools as being an essential foundation of our Democracy.

Richard was also following the example of Henry Ford, who challenged the patents that were used in 1911 to monopolize the development of the automobile. After overcoming this patent restraint on innovation, the automobile was able to develop rapidly. Richard Stallman argued that the same freedom from patent restrictions would lead to innovation in the software industry which would benefit everyone. Richard argued that scientific advances were best accomplished in a process of openness and cooperation rather than corporate secrecy. Richard’s goal was to bring a free software operating platform into existence. Stallman wanted computer users to be free to study the source code of the software they use, free to share the software with other people, free to modify the behavior of the software, and free to publish their modified versions of the software. In 1989, GNU published the first General Public License (GPL) under which software is legally shared freely.
Linus Torvalds Provides the Missing Link
One thing missing from the GNU project was a stable “kernel” or core which is at the heart of the operating system. The kernel can be thought of as the foundation of a house. GNU made all the components of the house, such as the walls and the roof and the plumbing and electrical devices. But the foundation they built it on – a kernel called HURD – was too complex and too unstable. In 1991, a simple, stable kernel was created by Linus Torvalds. The kernel was called Linux since it was based in part on the Unix operating system. The Unix operating system was a private system owed by AT&T which for many years had allowed folks to use their program for free, but in 1979 AT&T decided to start charging to use their UNIX program. Most programmers paid the fee. But some, including Linus Torvalds, decided to create their own operating system.
|
Quote
|
I believe Open Source is the right thing to do the same way I believe science is better than alchemy. Like science, Open Source allows people to build on a solid base of previous knowledge, without some silly hiding... you can never do as well in a closed environment as you can with open scientific methods. |
The proper name for the Linux operating system is GNU/Linux. However, as this is difficult to say and remember, most people simply refer to it as Linux and refer to the project which supports much of what goes into it as the GNU project.
|
Quote
|
We worked very hard on creating a name that would appeal to the majority of people, and it certainly paid off: thousands of people are using Linux just to be able to say “I've got Linux. What a cool name. Linux Torvalds, 1993 |

Richard Stallman protests that calling GNU/Linux just Linux fails to recognize the role that GNU plays in building the entire operating system. However, in this book we will use the simple term Linux as our goal is to spread the use of this operating system and a simple term is more likely to spread usage than a complex term.
BSD, another free open source operating system is developed – and also paid for by the public
While Linux was the world’s first free open source operating system, it was soon joined by another free operating system called BSD which stands for the Berkeley Software Distribution. This project started in the 1980s with a nearly finished free open source operating system released in June 1991. It was also based in part on the Unix operating system and therefore was a cousin of the Linux operating system. However, lawsuits by similar commercial operating systems, held up release of BSD until 1994 when a court decision held that over 99% of the BSD system did not violate any patents. There are currently several versions of the BSD free operating system.
What is important to understand about both the Linux and BSD operating systems is that both of them were initially funded primarily by public tax payer dollars. The BSD project was at the University of California at Berkeley. Nearly all the funding therefore came from taxes paid by the citizens of the State of California with some help from the US federal tax payers. Linux Torvalds also points out that the only reason he was able to devote several years to creating the Linux operating system was that the citizens of Finland paid for his college education. In Finland, citizens can attend college for only $500 per year. Linus spent 8 years getting his Master’s Degree (and working on the operating system). So we really should thank the citizens of Finland for the fact that we all can now benefit from the world’s safest operating system.
Microsoft and Apple take advantage of free open source operating systems
While Microsoft and Apple have both accused each other of violating each others patents, the irony is that they have both used free open source components to improve their own operating systems. The Apple operating systems in particular is based almost entirely on the BSD operating system. Thus, Apple is a close cousin of the Unix and Linux operating system. Because BSD and Linux are shared over the Internet, both projects had a strong interest in developing the Internet networking portion of their free operating systems. As the importance of the Internet grew in the 1990s, Microsoft adopted most of this free open source networking code into its own commercial operating system. Therefore, regardless of the operating system you are currently using, you are already using some free open source code.
There are many other examples of technological development paid for by the public. The entire Internet was built by public universities with public taxpayer dollars. The wireless Wi-Fi system was also created using public taxpayer dollars. Even current development of open source programs is done largely by programmers at public universities who want to share code with programmers at other public universities. The only question is why any of us should continue to pay for products which were all created by our tax dollars. When products are created by the public, they ought to remain free and in the public domain. There is clearly something wrong with the current system: the public pays the costs of technology development but private monopolies take the profits.
Open Source Initiative versus the Free Software Foundation
Despite the fact that the GNU/Linux operating system was free and was the safest and most versatile operating system in the world, adoption and refinement of the GNU/Linux operating system grew slowly. The first complete version, Linux 1.0, was not released until 1994. Ironically, there is a drawback to the word “free.” Businesses and the general public tend to think of the word “free” as in no cost or “cheap” or “not very good.” Richard Stallman tried valiantly to clarify that the term “free” meant free as in “freedom” and that freedom from patent restrictions is important. But businesses and the public failed to recognize that their freedom was being taken away by the Microsoft and Apple monopolies. Unfortunately, many business owners thought that free open source programs meant a communist attack which threatened their belief in capitalism.
To encourage wider adoption of the Linux operating system, a group split off from the Free Software Foundation in the mid-1990s and formed the Open Source Initiative. Instead of emphasizing the fact that the software was free, they pointed out the benefits of the software being open source – meaning that the source code was free of patent restrictions and could be freely shared. This change in focus led to businesses such as Google, Amazon and Facebook adopting version of the Linux open source operating system. These groups then devoted some funds back to the further development of open source operating systems. However, the emphasis on this new open source transparent code (rather than freedom) led to a split between Richard Stallman and Linus Torvalds – a difference of opinion which still exists today.
Two Desktop Interfaces… The First Fork in the Road
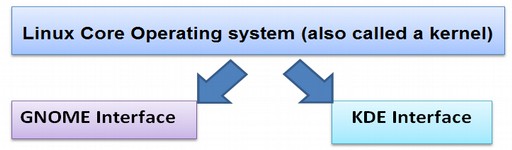
One problem with the Linux operating system in 1992 was that you had to know computer programming to use it. Therefore several groups began working on open source Graphic User Interfaces or GUIs so that a person could simply click on a series of buttons with a mouse rather than typing a bunch of computer programming with a key board – thus making Linux more user friendly. The interface appears on a computer screen which is also called a desktop. At some point, this interface became called a “Desktop Environment” or DE.
The first open source desktop interface, called KDE for K Desktop Environment, was started in 1996. However, because some parts of KDE were not open source, a second and fully open source operating system, called GNOME, was started in 1997. GNOME stands for GNU Object Modeling Environment. This was the first major fork in the road for the Linux operating system. Even today, there are still Linux Systems based on GNOME and others based on KDE. A branch off of the Linux tree is called a fork:
Linux takes over the Web Server Market
Because any computer programmer can do whatever they want with Linux, there quickly became many forks of Linux. Most of these forks were special branches intended to run servers. Servers are special computers that host websites and control traffic on the Internet. The main reason most servers use the Linux operating system is that it is safe and dependable. Unlike a personal computer, which is usually on only a few hours a day, web servers are typically on 24 hours a day. You therefore need an operating system that does not crash regardless of what it is confronted with. You also need an operating system which is safe from viruses and hacker attacks. Because servers are built and run by experienced computer programmers, most of them chose to use Linux. But they also forked Linux into highly specialized versions which are not that appropriate for the average person to use to run their own personal computer.
GNOME 1 and 2 Shells
The GNOME project developed a free open source graphic user interface which is used to display the free open source Linux operating system on a normal personal computer. Gnome 2 was started in about 2002 to improve the appearance and structure of Gnome 1. These incredibly smart people were interested in long term cutting edge innovation more than short term quarterly profits. For years, Linux had been a tool used mainly by Geeks and computer programmers who would build their own computers from scratch. It is actually easier than you might think to throw together a few computer components and create a low cost high powered computer. Because they wanted freedom, they would also install their own operating systems – which were nearly all offshoots of Linux. But to use these early Linux operating systems, you pretty much had to be good with computer programming. While some of the computer could be controlled using the GNOME interface, many functions still required entering computer commands into a portion of the GNOME interface called the “terminal.” Think of terminal as in deadly illness. Requiring any computer programming at all eliminates 99% of us who will never learn computer programming. I personally know several computer programming languages and have taught computer programming. So I am not really talking about myself. I am talking about my students. It takes real focus and dedication to get good at computer programming and most people simply do not have the time or interest to really learn it.
Distributions – also known as Distros
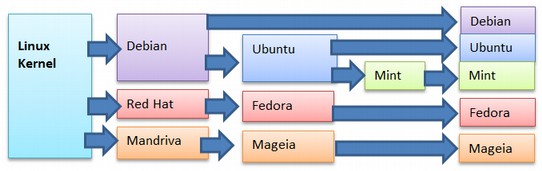
Distributions are packages of free open source programs that are built on top of the Linux foundation. The package includes a word processing program, an image processing program and any of thousands of other possible programs. Some distributions use the Gnome Shell, some use the KDE shell and/or several different shells. When you download a Linux operating system, what you are really downloading is one of the many distributions of Linux. The oldest of these distributions is Debian – which began in 1993 using a very early version of the Linux operating system. Fedora was introduced a couple of years later. This distribution is sponsored by a commercial Linux based company called Red Hat which has revenue of over one billion dollars per year. Below is a 2017 November list of the five most popular distributions (or open source software packages) based on number of page hits per day according to distrowatch.com:
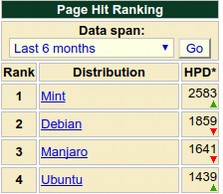
Linux Mint is the first Linux distribution to average over 2,500 page hits per day. It has been the leading Linux distribution for the past two years. Ubuntu is a fork of Debian that was started in 2004 to offer a consistent release and update cycle. It was the most popular distribution until about 2011 when it was replaced by Mint. Mint is a fork of Ubuntu that was started in 2006 to offer users a more Windows-like operating system.
Linux Distributions Family Tree
Linux Ubuntu
Ubuntu was started in 2004 by a South African businessman named Mark Shuttleworth. His company is called Canonical and his goal was to create a more user friendly operating system. He chose the “Debian” version of Linux as his base and added more friendly user interfaces over time. Like Debian, Ubuntu is based on the Gnome shell.
While Ubuntu and Mint are technically called “distributions” or “distros”, they can also be thought of as “skins” with Linux as the brain. Ubuntu released a version called Warty Warthog in 2004. This was the first widespread public adoption of an operating system other than MS Windows and Apple Mac. The main benefit of Ubuntu back in 2005 was that it was free. It was therefore used in cheap computers in schools and in poor countries, which often could not afford hundreds of dollars per student every year for Windows based operating systems and related software. Sadly, Ubuntu was not very stable and it crashed a lot. It was also not very easy to use. Many of the functions are hidden and the file structure is not very logical. Worst of all, to really use it, you still had to learn a series of computer programming commands to operate their “terminal.” This meant that Ubuntu was not a good choice for most beginners. But the worst aspect of Ubuntu is its blatant promotion of a mega corporation - Amazon. In October 2012, Ubuntu released version 12.10 which, for the first time, featured a link to Amazon.com in its main menu. Below is the Linux Ubuntu Start Screen:
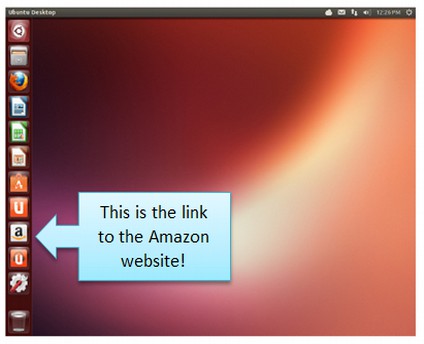
It is easy to delete this link. But what angered many Ubuntu users is that Ubuntu now collects data on user desktop activity and forwards it to Amazon. Many Ubuntu users are now bombarded by ads from Amazon after using the Ubuntu Search Box (which is now linked to Amazon).

Richard Stallman has described the integration of Ubuntu with Amazon as “spyware.” See the following 6 minute Youtube video for a fuller explanation of Richard Stallman’s concerns about the Amazon/Ubuntu invasion of your privacy:
http://www.youtube.com/watch?v=CP8CNp-vksc
One of the advantages of free software is that users historically have been able to protect themselves from malicious features. To recover our right to privacy, we have to either convince the Ubuntu developers to stop spying on us - or we need to move away from Ubuntu towards a project like Linux Mint which does not spy on us. I should add that even if Ubuntu stopped spying on us, I would still recommend Linux Mint because it has a much better file manager. Also Ubuntu has a problem in that, like Windows 8, many important commands are hidden from view. You can navigate the Dash with your mouse, but it is incredibly complicated for beginners, hiding a lot of your apps under expandable menus and small icons. That means browsing for apps is a pretty bad experience when you are using Ubuntu.
The Linux Mint Project starts in 2006
In 2006, a group of programmers, led by Clem Lefebvre, split off from Ubuntu and began the Linux Mint project. The Mint interface and file structure are much more like the Windows interface and file structure. This was a huge improvement over Ubuntu – but nowhere near as mature as Windows XP, which had a 10-year lead over Linux Mint. Just as Rome was not built in a day, it took several years for the Linux Mint team to create a stable reliable product. Development, appearance and user friendliness accelerated in 2009 with the introduction of the Ubuntu Software Manager. This new tool, used by both Ubuntu and Mint, would eventually put open source operating systems ahead of commercial operating systems which lack this feature. Their latest version, Linux Mint 18 Cinnamon, featuring Libre Office 5, is in many ways substantially better than Windows 10. We will review these benefits in the next section on Linux Mint. Even ignoring the fact that Mint is free, it is better than Windows – and can work with either Windows based programs – or with thousands of free open source programs, such as Libre Office, which easily converts Microsoft Office documents.
Linux Mint comes in four different flavors or versions.

In addition, Linux Mint is available in two more versions. These are the KDE project’s version of Linux and the XFCE version of Linux:

For many years, I had recommended Mint Mate over Mint Cinnamon because Mate was less cutting edge and therefore more stable. However, Cinnamon has improved greatly in the past six years and is now very stable. It also offers many features not available on any other Linux distribution. I therefore now recommend Mint Cinnamon for any computer that has at least 2 GB of RAM. Mint XFCE is not very good because its file manager is limited. However, Mint KDE is interesting in that it is similar to Mint Mate. If this sounds confusing, it is. One of the drawbacks of Open Source is that anyone is free to do whatever they want. So there are lots of options and you will need to get use to a diversity of options and opinions if you want the benefits of open source programs.
Understanding Linux Diversity
One of the perceived drawbacks of Linux is complexity. Linux comes in many different flavors which are called distributions (or distros for short). This is actually a good thing since there is strength in diversity and because diversity helps promote innovation. There are also many versions of Windows and Mac Operating Systems. But with Windows and Mac, the main purpose of their version changes seems to be to force their customers to pay them for the update to the new version – which is often worse than the old version. With Linux, diversity is more related to meeting different needs – not to create more profits.
Below are just a few of the many branches off of the Linux tree:
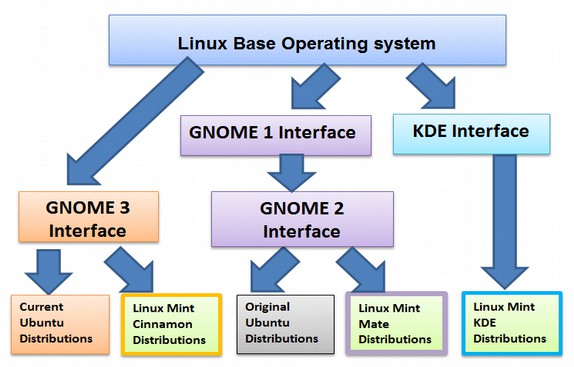
A key difference between the various Linux options is the Graphic User Interface. Other differences include the File Manager (each has a different one) and the other free programs that come packaged with each option. We will handle this complexity by recommending what is currently the simplest, most stable and most powerful interface – Linux Mint Cinnamon.
Its screens look quite similar to Windows 7 and Windows XP screens – so if you have been using Windows 7 or XP, you will feel right at home. In my opinion, Linux Mint Cinnamon is currently the best and most stable operating system in the world. It uses a very easy file manager called Nemo.
Reasons to Choose Linux Mint Cinnamon
What is important to understand about Linux operating systems is that there is really no need to upgrade or get updates unless you really want to. Some folks have expressed concerns about the rapid release cycles with open source programs such as Linux Mint Cinnamon. New versions are released about every six months. Novices fear it will be difficult keeping up with all the updates and new versions. However, unlike Windows, which leaves the back door open to hacker attacks, Linux does not leave the back door open. Thus, there is no need for a monthly “update” and there is no need for an annual “upgrade” just to have a safe and secure operating system.

Linux Mint Cinnamon Desktop with Start Menu open
The only reason to upgrade is if you want some new features. Because a lot of people want the most recent version, Linux Mint Cinnamon offers a way to back up and copy all of your data whenever you want to update to a newer version. While free open source operating systems like Linux Mint are still less than 3% of all current personal computer users, the trend is clearly going in their direction.
Free Software
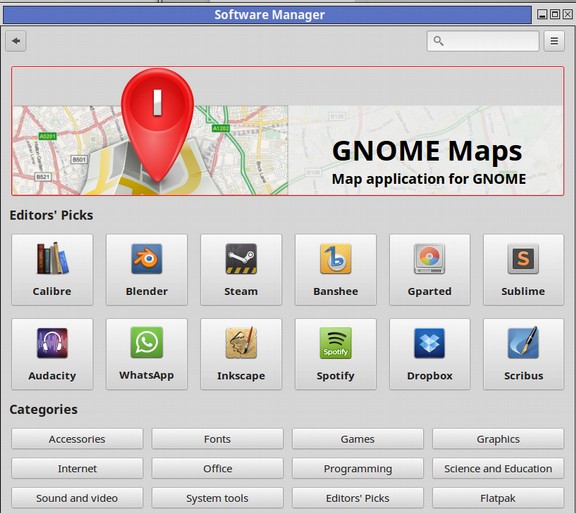
Another huge advantage of Linux Mint is there free Software Center which allows us to download any of hundreds of programs with just the click of a button:
Linux Mint Community Forum
A final reason to choose Linux Mint over other Linux distributions is the Linux Mint Forum. Because Linux Mint was developed specifically for those who were used to the Windows operating system - but wanted to move away from Microsoft, the Mint Community Forum is run by people who are kind, understanding and aware of the challenges that a Linux novice faces in making the jump from Windows to Linux.
Spend some time reading the questions and answers on this forum and you will quickly see that Linux Mint is not merely an operating system. It is a community. Feel free to ask them any questions you have about Linux or Linux Mint. Here is a link to the Linux Mint Community Forum. https://forums.linuxmint.com/

Linux Mint Cinnamon is Easy to Learn
In our books and courses, we recommend Linux Mint Cinnamon mainly because it looks and works much like the Windows XP and Windows 7 operating systems. It is thus a very easy way for Windows refugees to learn and use Linux. Mint also has an excellent community of supporters who answer questions asked by “nu bees” on the Linux Mint forum. We also recommend Mint because it can be easily customized into a powerful tool for writing books, courses and websites.
Tipping Points and the Structure of Scientific Revolutions
In the book, The Structure of Scientific Revolutions, Thomas Kuhn explains that revolutions do not happen gradually. People are highly resistant to change. They cling to existing beliefs until something drastic, a triggering event, forces them to consider something new. That triggering event may be the Double Whammy of Microsoft ending support for Windows XP and at the same time trying to force users to adopt the fundamentally flawed Windows 10 operating system. Once 10% of the people become aware that there is a better option – which is also free – and an option where they can continue to safely use their current computers and current Word documents, change can spread like wildfire to the rest of the population.