Have you ever wondered why the Microsoft Windows operating system is so much more susceptible to viruses and hacker attacks than Linux? Why does the Windows operating system need hundreds of “updates” every month? Why is it that Microsoft makes such a lousy operating system even though it has tens of thousands of programmers? Why it is that Windows has such an insane structure? Why does Windows come with two web browsers built into its core – neither of which can be turned off? Why are we so confident that Windows 10 will not be able to address the most important flaws of Windows 8?
|
Quote
|
“I just got a new computer which came with Windows pre-installed on it. I have one question... How can I get rid of Windows?” |
The fatal flaw is the Microsoft Monopoly Business Model
To answer these questions, we need to understand that the structure of the Microsoft way of doing things is totally different from the Linux way. I understand the Microsoft way because, from 1985 to 2004, I had hundreds of Microsoft students attend my courses at Bellevue College. I spent thousands of hours talking with Microsoft employees. I knew more about what went on at Microsoft than most of their employees. Some of my students were responsible for coming up with creative ways to stop pirates from making bootleg copies of Windows. Imagine that was your job. What would you do? How would you stop the pirates?
The answer is that it is impossible to stop pirates from copying Windows because it is a digital program which is easily copied. All you can do is add complex keys and other gimmicks which prevent pirated versions of Windows from working. But for every gimmick Windows comes up with, pirates come up with a counter gimmick. So all the gimmicks really do is add more bloated code to the already bloated code of Windows. This is a huge reason why Windows is so much more bloated than Linux. Linux does not care if you copy their operating system – in fact they encourage it. But Microsoft does care about copies. So Microsoft uses a series of gimmicks to throw monkey wrenches in the path of the pirates.
The First Major Gimmick... Internet Explorer: the open back door
The pirating problem got much worse for Microsoft in the 1990s as the Internet itself was used to spread pirated copies of Windows as well as information on how to attack Windows. In 1996, Microsoft came out with Internet Explorer – which was their first attempt at a web browser. The first three versions were separate programs which ran as normal programs outside of the Windows core. In fact, the first three versions of Internet Explorer were actually “borrowed” from Netscape. But a strange thing happened with Internet Explorer 4 when it was added to Windows 98. Suddenly, instead of being a separate program, Internet Explorer 4 was inside the core of Windows – and has been ever since.
|
Question
|
Internet Explorer 1, 2 and 3 were separate programs added to the Windows operating system. Internet Explorer 4 was placed inside of the Windows operating system.... WHY? And why does Windows 10 now have 2 MS Windows browsers inside the operating system(s) - neither of which can be removed? |
Think about this. Why would anyone in their right mind tie the web browser code directly to the operating system code? Linux doesn’t do this. There is no doubt that tying these two things together makes the programming for each much more difficult – and slows down both the browser and the operating system. With all of these drawbacks, Microsoft must have had a very good reason for putting Internet Explorer 4 in the Windows core. Some mistakenly thought that Microsoft was trying to monopolize the browser business. But this was not the case at all. At the time, browsers were being given away for free. There was and still is very little money to be made by monopolizing the browser business.
The initial motivation for Microsoft to link Internet Explorer to Windows was because they wanted to maintain the Windows monopoly. The only way to do this was by adding Internet Explorer integration to the Windows core. Allow us to explain how this whole process works. It is important to know because this is the “Windows open back door” which we refer to throughout this entire book.
Evidence that Microsoft put an open back door in your computer
If you start with the understanding that the most important thing for Microsoft is money – which means protecting the Windows monopoly, then this need for an open back door to constantly call home to Microsoft starts to make sense. This open back door allows Microsoft to tell if you did not pay for your copy:
Fact #1: You cannot uninstall Internet Explorer from Windows
This is true of Windows XP, Windows Vista, Windows 7, Windows 8 and Windows 10. You can “turn Internet Explorer off” from the Windows feature list – which hides Internet Explorer but does not remove it.
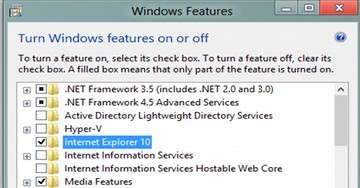
Many users (and especially programmers) have recognized that the most vulnerable part of any Windows operating system is Internet Explorer. Because most of them hate Internet Explorer and won’t use it, there is a natural tendency to try to get rid of it. But if you actually succeeded in getting rid of it, you would crash Windows. This is because Windows puts Internet Explorer in its core.
Fact #2: Microsoft Updates come in through Internet Explorer
Have you ever wondered what all the updates are about? Microsoft calls them security updates. But many of these updates are not at all about protecting your computer. They are about protecting the Microsoft Windows monopoly. The idea is to constantly keep changing your Windows settings (creating a moving target) to prevent pirated copies of Windows from fully functioning. Without these constant updates, there would be no Microsoft Windows monopoly.
Fact #3: Each version of the Windows operating system is tied to a particular type of Internet Explorer
One of the many problems of trying to continue to run Windows XP is that it will not work on any version of Internet Explorer past Internet Explorer 8. Why is this? Some have claimed that Microsoft is doing this deliberately to try to force Windows XP users to upgrade to Windows 10. This could be. But there is a more fundamental reason. The reason Internet Explorer can not be updated on Windows XP is because the functions of Windows and the functions of Internet Explorer are tied together at the hip. This is why Windows XP can run the latest versions of Mozilla Firefox and Google Chrome web browsers but cannot run the latest versions of Internet Explorer. Microsoft is stuck. Tying their operating system to their web browser is simply the only way they can stop pirates and maintain their monopoly.

Windows keeps getting worse over time!
Windows 10 uses a version of Internet Explorer called Edge
There are some very strange things about Edge. For example, Edge cannot save a web page as an HTML document even though web pages are HTML documents! But Edge comes with Internet Explorer inside of it and Internet Explorer can save web pages as HTML documents. To see this, open the Edge browser. Then click on the menu on the far right side of the Edge browser to open it. You will see this menu:
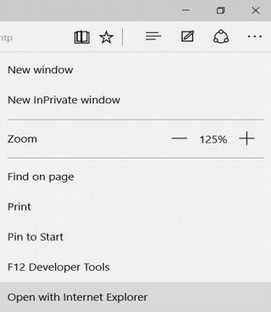
Click Open with Internet Explorer (the last option in the image above) and suddenly, even though the web page will be the same, you can save it as an HTML document! This proves that Windows 10 is still using two web browsers. Thus, even with Windows 10 we are dealing with two completely separate operating systems with two completely separate versions of Internet Explorer!
Why Windows can not get rid of Browser Hijackers
Here is why it is dangerous to build the web browser inside the core of the Windows operating system… The web browser can become infected - but it cannot be removed. Here is an example: A Browser Hijacker is a malicious program that changes the home page or search settings of your web browser. Some hijackers will enter your computer through your browser simply because you visited an infected website. The hijacker can then modify Windows shortcuts without your knowledge to automatically load a particular website when you start your browser.
“Just had my Firefox infected with this hijacker. Funny thing is I am running Linux Mint and they want me to call Windows Support! That's too funny! I just did a simple clean install of Firefox and wiped the hijacker right out. A note to Windows users: This browser hijack would take over an entire windows computer. As I am running Linux, the infection could not get outside of Firefox therefore my system is safe. Glad the Linux environment does not support .exe files!”
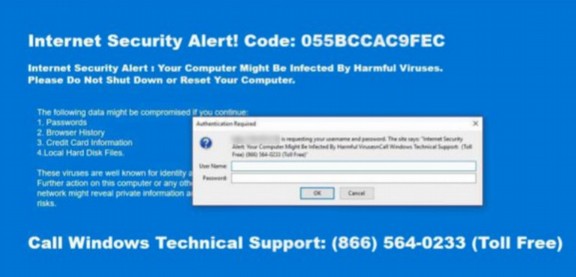
Windows 10 requires you to use their insecure web browser to change your password
With Windows 10, you cannot perform many functions – including resetting your password, unless you are online. This is one of the most sinister and least known “features” of Windows 10. We covered this in our first chapter. But ask yourself... why should Microsoft care about what your password is? And why would they want to store your password on their database? With Windows XP and Windows 7, you had complete control over your user account and your password for your computer. You could just click on Change your Password. Then type in your current and new password. There was no need to be online to change your password with Windows XP or Windows 7 and Microsoft did not care what your password was. After all, it is your computer, isn’t it?
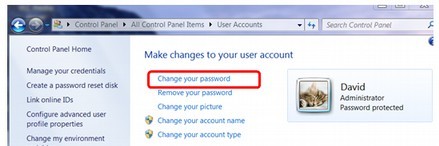
However, with Windows 10, you must be online to change your password. Even to get to the password screen requires following many steps. First, you need to start Internet Explorer. Then click on Settings. Then click on a link called Change PC settings. This takes you to the new Metro Control Panel. Then you click on Users. This takes you to the Metro User Account screen:
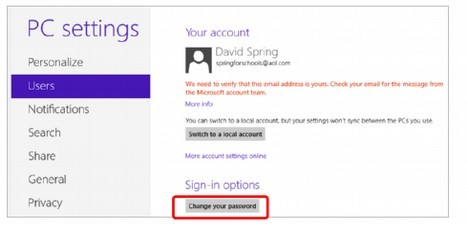
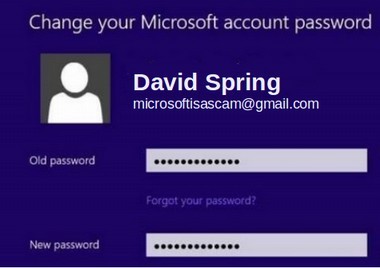
Note that your account with Windows 10 is now tied to your email address. Next, click on Change your Password. If you are not online, you will see this warning:

However, if you are online when you try to reset your password with Windows 10, you are taken to the following password reset screen:
Three warning signs your Windows 10 Computer has been hacked:
Despite all the Microsoft gimmicks designed, all these gimmicks have done is add more ways that hackers can attack your computer. Therefore, as a public service, we are providing three surefire signs that your Windows computer has been hacked. First, if you notice the Microsoft now fails to authorize programs it used to find acceptable, you may have a problem:
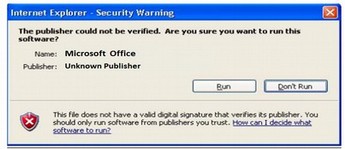
Second, if there seems to be an abnormally high number of security updates on Patch Tuesday, you may have a problem:
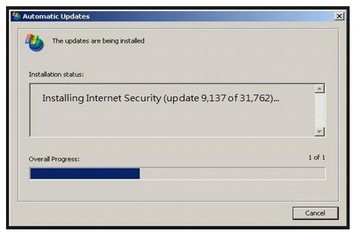
Third, if you see additional users who you do not recognize on your Windows 8 log in screen, it is very likely that Microsoft security has been compromised.
A suspicious Windows Login screen:
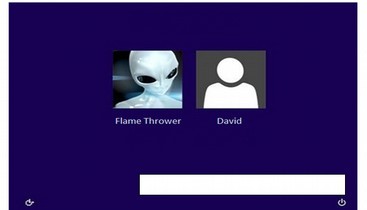
If any of these three things start happening to your Windows 10 computer, please reboot using a more secure operating system – like Linux Mint!
What’s Next?
As bad as the Windows Insecure Open Back Door is, there is now something even worse – the Microsoft Kill Switch – which we will cover in the next section.

