For the past two years, ever since the release of dozens of NSA created Windows hacking tools in 2017, there have been an ever increasing wave of ransomware attacks against Windows computers. During this time, I have written several articles explaining in detail how hackers use hidden back doors in the Windows operating system to take over and lock up Windows computers. I ended each of these articles by urging folks to protect their data by replacing the poorly designed Windows operating system with the free and much more secure Linux operating system as this is really the only way to protect your computer, your data and your business from a ransomware attack.
It is surprising that despite these ever increasing Windows Ransomware attacks, the value of Microsoft stock has continued to increase to the point where Microsoft is now a trillion dollar corporation. I understand that Microsoft spends billions of dollars on marketing and promoting itself. But one would think that eventually the truth would come out that Windows is not a secure operating system. However, instead of exposing the truth about Windows Security Flaws, the corporate media is engaged in a relentless campaign of making a series of false accusations against Linux claiming that Linux also suffers from security problems. Just a week ago, I published an article debunking the false claim that Lilu Ransomware had hacked thousands of Linux Servers. Here is a link to this article: https://learnlinuxandlibreoffice.org/news/did-lilu-ransomware-really-infect-linux-servers
In this article, we will review two additional and equally false claims made against Linux – namely that Linux can be hacked by Skidmap Malware and/or by Evil Gnome malware. Both of these claims are made with no evidence to back them up. Yet both claims, like the Lilu Malware claim were published on thousands of news websites as if they were God Given Facts.
When we read articles on the Internet, we need to become more aware that we are literally being bombarded by a nuclear firestorm of lies. These lies are designed to brainwash and manipulate us into supporting multinational corporations that are not at all interested in protecting us. Instead, the writers of these false articles are hired to protect corporations like Microsoft and maximize their quarterly profits by producing a wave of propaganda. We this in mind, let’s first look at the Skidmap Malware claim.
Skidmap… Malware so hidden that it does not even exist!
Here is a clever image created by one tech security website trying to link Linux to Skidmap Malware:

The Skidmap hoax apparently began on September 16 2019 published by a website called Trend Micro. Before we get into the details of the claim, let’s look at who is making the claim (I call this part “Following the Money”).
Trend Micro is a company started in 1988 to provide Microsoft computers with anti-virus protect. In other words, the more insecure the Windows operating system is, the more money Trend Micro makes. They have a financial interest in publishing negative information about Linux because Linux is so secure that you do not need any antivirus software.
Trend Micro is a Microsoft “Gold Partner.” None of the so-called news articles that repeated the Skidmap hoax note either of these facts. But I think it is relevant when it comes to assessing their credibility.
Now for the actual allegations. The headline for all of these articles is some version of the following: “Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency Mining”
This sounds very high tech. The reader is likely to know that Cryptocurrency Mining is Bit Coin Mining. You likely have heard that hackers can and do take over Windows computers all the time and use them for Bitcoin mining. So if hackers can do this to Windows computers, it seems at least plausible that hackers could also take over Linux computers and use them for bitcoin mining. This only sounds plausible because most readers have no idea that there are huge differences between the security of Linux computers versus the lack of security of Windows computers.
Note that the title also includes the word rootkit. Most people have no idea what the word rootkit even means. It turns out that even Trend Micro has no idea of what the word rootkit means. Here is their definition (from a different article on the same Trend Micro website):
“A rootkit is a program that installs and executes code on a computer without end user consent or knowledge. It uses stealth to maintain a persistent and undetectable presence.. Rootkits are installed on systems via social engineering... or simply by browsing a malicious website.”
Wow. All you have to do is accidentally visit the wrong website and your computer is toast. I guess you better buy that wonderful Micro Trends anti-virus snake oil if you do not want your computer to be fried.
Actually, their definition of a rootkit is partially correct. You can wind up with a malware on your computer if it is a Windows computer because Windows has wide open back doors that allow hackers in whenever you go online. But the malware is not likely to be a rootkit if you are running a Linux computer. In fact, the malware is not likely to infect your computer at all. This is because while Windows computers allow programs to be installed without a root password, all Linux computers require you to enter a Root password before any additional program can be installed.
Here is what Rootkit really means: The word Root in Rootkit stands for the Root User or the User who can install additional programs. Windows computers allow root access without a password. Linux computers require a password to get root access. See the difference?
There are rootkits that can be installed on Linux computers. But they cannot be downloaded just by visiting a malicious website. I have written a detailed article about this which you can read here if you are interested:
https://learnlinuxandlibreoffice.org/news/the-fight-for-a-secure-linux-bios
Here is an image from this article that explains the difference between a virus and a rootkit.
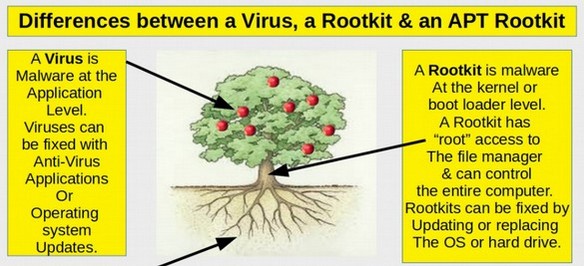
Note that a rootkit has to have root access. It is root access that gives a rootkit persistence. So exactly how does Skidmap gain root access to a Linux computer? According to Trend Micro:
“Initial infection occurs in a Linux process called crontab, a standard process that periodically schedules timed jobs in Unix-like systems.”
What?? You have never heard of crontab? Then let’s learn a little about it. Crontab is a process that can help you schedule automatic backups and automatic updates if you are too busy or too lazy or too forgetful to do those the old fashioned manual way. To see what crontabs are currently running on your Linux computer, assuming you have one, you can open a terminal and run: sudo crontab -l
You will then be asked to enter your root password just to even look at what crontab tasks are running.
By default, there aren’t any crontab jobs on any Linux computer. In fact, you would need to authorize the addition of any tasks by entering your root user password.
This is an example of the difference between Windows and Linux. Windows puts Microsoft in control of your updates through automatic updates remotely controlled by Microsoft (and whatever hackers also know about this backdoor and use it to remotely control your computer - while Linux puts you in control of your updates and all other changes on your computer. Hopefully, you can see now why the Trend Micro claim is complete and utter nonsense.
What about Evil Gnome?
Here is another clever image on one of the corporate run fake news websites trying to link Linux to Evil Gnome. Note that they use the word Linux TWICE in an effort to drive their point home:

In the past few days, a group called GB Hackers published an article claiming: “Researchers discovered a new Linux malware called “Evil Gnome” with previously unseen functionalities that capable of creating a backdoor and spying the Linux desktop users. Based on the evidence and the operational similarities, the implant possibly distributed by Gamaredon Group, a Russian based threat group that has been active since at least 2013.”
Well, since Evil Gnome was discovered by “researchers” then it must be something real and dangerous. They must have evidence, right?
Let’s look at their evidence: “Infection Process… Initially, Evil Gnome delivers a self-extracting archive shell script created with makeself, a small shell script that generates a self-extractable compressed tar archive from a directory.”
What? Shell script? You mean to say you have never heard of a shell script? A shell script is a small program you can run on a Linux computer. But here is the catch. To run a shell script in Linux, you have to enter your root password. But let’s pretend that somehow the hackers made it past this minor difficulty. Is there any more evidence about where this attack is coming from? Here is a quote from the GB Hackers article:
“Indicators of Compromise: Gamaredon Group:
185.158.115.44
185.158.115.154”
Well, providing two IP addresses used as a command and control center by the hackers is certainly evidence. Let’s do an IP lookup to see where these IP address servers are supposedly located.
It turns out that 185.158.115.44 is a server located in Moscow and owned by IP Server LLC. Ditto for 185.158.115.154. No need to look any further. These clearly must be very smart Russian hackers who have figured out some way to get into the 10 million Linux servers in the world even without the root password.
But just for the sake of curiosity, (and because I have spent many years researching hundreds of similar fake Russian servers), let’s dig a little deeper. Here is the website associated with IP Server LLC:
The website certainly looks like a normal shared hosting company. Here is a quote from the website:
“IpServer provides rental services for physical and virtual servers with a wide selection of locations.”
In fact, IP Server LLC has hundreds of servers in more than 20 locations including Russia, France and Finland with two new locations in the US (Oregon and Virginia).
They claim to have been in business for more than 11 years. But something does not seem right. They only have two named servers and these only have a couple dozen websites on them.
Normally, we would expect close to a thousand websites on each of dozens of named servers. Think GoDaddy for example. GoDaddy has hundreds of servers and every one of them has a thousand websites on therm. But every server costs more than one thousand dollars and requires a lot of maintenance.
So if the servers for IP Server LLC only has a couple of dozen websites on them, then where is all of the money coming from to run all of these offices all over the world and pay for these thousands of servers?
To answer this question, let’s use the Wayback machine to look at the real history of their website. Here is the URL: https://web.archive.org/web/2018*/ipserver.su
In 2009, they had a very rough website skeleton based on the Drupal framework and claimed to have servers in Russia and the US and many other countries. The website did not change until 2012 when it finally became more presentable and added the current logo. In 2013, the website also added an “About Company” page indicated that the company was located in the British Virgin Islands. Here is a screen shot of that page:
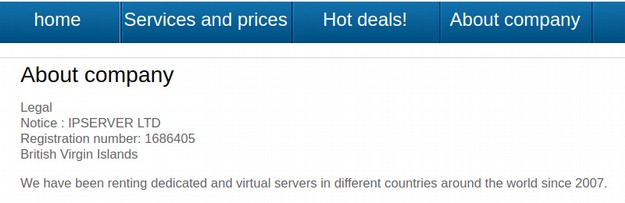
It was not until 2017 that they apparently moved their headquarters to Moscow. Based on the above, and based on years of past research into fake Russian shell corporations, here is what really happened:
These are not Russian hackers. They do have a Command and Control Center. But it is not located in Moscow. Instead, it is located in Virginia and is run by NSA hackers that are pretending to be Russian hackers.
That’s right. This entire scam is being funded by literally billions of your hard earned tax payer dollars. This is how you can get a company with thousands of servers in 20 locations around the world without any need to make any kind of profit.
The NSA hacking group is also known as the Equation Group. The Equation Group “Persistence Division” did in fact start their operation in 2007. The following image is from a 2007 NSA Slideshow supplied by Snowden and made public by the Intercept on January 24 2019. The NSA and its Sub-contractors have at least 100,000 hackers. Many of these are in TAO or Tailored Access Operations. This is slide 7 which describes the mission of the Persistence Division (mis-spelled) which is part of TAO. Note the emphasis on working with their “community partners” aka Microsoft and Intel.
https://theintercept.com/document/2019/01/24/tailored-access-operations-2007/

In February 2015 Kaspersky releases 44 page report on NSA Equation Group summarizing their hacking tools over the past 10 years.
https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/08064459/Equation_group_questions_and_answers.pdf
90% of the servers used by Equation were shut down in 2014, which could indicate a reaction to the huge trove of leaks from Edward Snowden about the NSA in 2013. The biggest mistake made by the Equation group was its failure to renew up to 20 of its 300 Command & Control servers. Kaspersky quickly registered these domains and over the last 10 months used them to sinkhole (redirect) communications with Equation-infected machines.
2017 March 31 Wikileaks publishes Marble Framework NSA hacking computers and mislead victims of NSA hacking attacks by leaving “Russian Finger Prints.”
Wikileaks published 676 additional NSA Vault 7 Hacking Tools. Significantly, these Vault 7 hacking tools included tools for misleading victims and researchers into thinking that NSA hacks were Russian or Chinese when in fact the attacks were written by and coming from the NSA. The framework utilizes pre and post-build execution steps to apply obfuscation to the tool.”
https://wikileaks.org/ciav7p1/cms/page_14588467.html
To learn more about them, please read the 50 page article I wrote about them and their history (an article which includes more examples of fake Russian websites and other NSA Shell corporations).
https://learnlinuxandlibreoffice.org/news/the-fight-for-a-secure-linux-bios
Conclusion
The NSA uses Linux to protect their computer security. But they do not want you to use Linux to protect your computer because then it would be harder for the NSA to spy on you. They realize that the threat of Windows Ransomware has gotten a lot of people thinking about switching from Windows to Linux. So the NSA has launched this propaganda campaign claiming that Linux is just as bad as Windows.
To be clear, I am not saying that it is impossible to hack a Linux computer. Certainly, the NSA is capable of targeting an individual Linux computer or Linux server network and using any of a variety of ways to obtain the root user password. But even if this did happen, there would be some evidence of the hack in the Linux user logs and or Linux server logs. And this evidence would expose both the location of the attack on the server and the location of the hackers at least in terms of their IP address and also the exact time of the initial attack. So claims that there is simply no way to deal with hackers are false.
What is true is that someone does not want the general public to be switching from Windows to Linux computers. So they have put out numerous stories that are widely published by the obedient corporate run media to try to convince you that Linux computers are just as insecure and subject to hacking as Windows computers.
The way to protect yourself from theses fake stories is to do more research. Do not blindly accept claims made by the corporate media. Learn how to use IP lookup. Learn how to use the Archive dot org Wayback machine. Most important, learn how to use Linux.
As always, I look forward to your questions and comments.
Regards,
David Spring M. Ed.
Springforschools at gmail dot com