I have written several reports explaining how ransomware attacks Windows servers and urging users interested in security to switch to Linux in order to avoid future ransomware attacks. See for example this link: https://learnlinuxandlibreoffice.org/news/hidden-dangers-of-ryuk-ransomware
I was therefore surprised and extremely skeptical of articles claiming that that a ransomware called Lilu had infected thousands of Linux servers. The first of these articles appeared at 3:30 am on September 6 2019 and described ransomware attacks dating back to July 2019. Here is a link to this article: https://www.zdnet.com/article/thousands-of-servers-infected-with-new-lilocked-lilu-ransomware/
The evidence provided to back up their claim was this image showing some files locked by Lilu Ransomware:
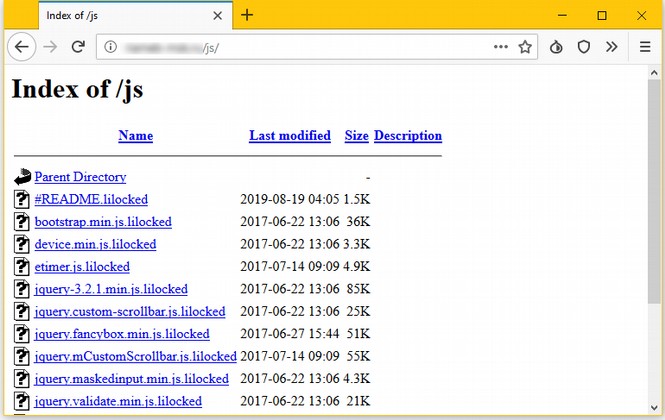
Note that the domain name of this folder has been hidden from view making it impossible for us to verify if these files were actually on a Linux server. The article goes on to note that “Lilocked doesn't encrypt system files, but only a small subset of file extensions, such as HTML, JS, CSS, PHP, INI, and various image file formats. This means infected servers continue to run normally.”
This limitation raises the obvious question of whether the core of the Linux server itself has been compromised or whether merely applications connected to the core have been hacked.
There are many very insecure website building applications such as Wordpress and many insecure web mail applications such as Exim that have been repeatedly hacked over the years. Both Wordpress and Exim have suffered from dozens of major security problems that have nothing to do with the security of the Linux operating system which is at the core of all Linux servers. All of the file formats mentioned in the article are files used on Wordpress websites and files that can be transmitted via Exim email programs.
The article then goes on to claim that “more than 6,700 servers have been encrypted by Lilocked.” Here is the image offered as proof of this claim:
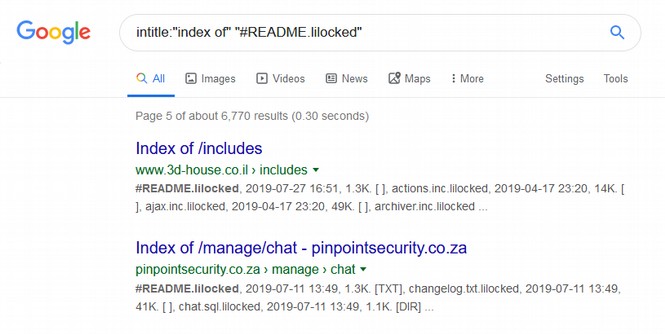
Note that no where in the search is there any mention of the word Linux. So what we are really seeing is infected website files. These files are likely on Linux servers since nearly all web servers are now Linux servers. But they could also be on Windows servers since some people living in the stone ages are still using Windows servers.
On September 17 2019, I ran a Google search using this same search term: intitle:”index of” “#README.lilocked”
I got the following 6,070 results:
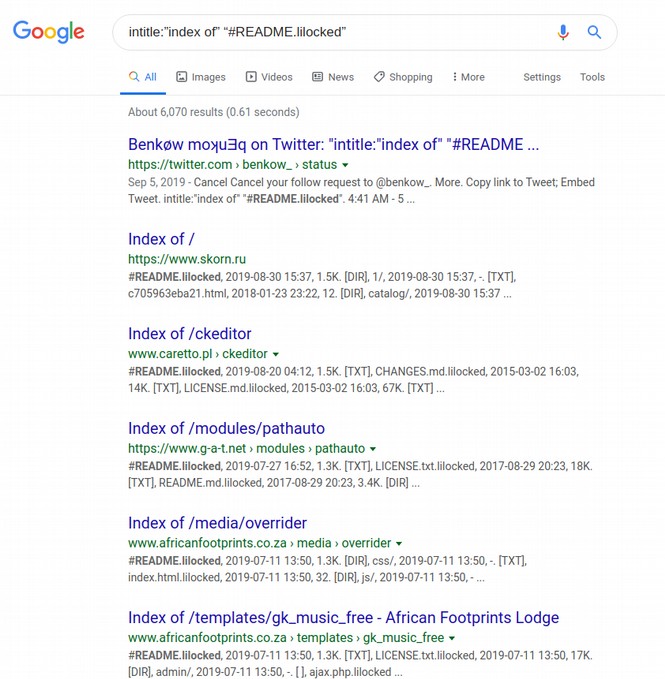
I think clicked on some of these links. The first link to a site on a Russian server was not secure. The second link was to a ck editor on a website hosted on a Linux Debian server. The third link went to a site on a Ubuntu server.
Looking at the URLs, it was clear that nearly all of the 6000 infected website files were in Russia. But many of the results were of files from the same website. Lots of the files were from the African Footprints Lodge website. Here is an example of three in a row:
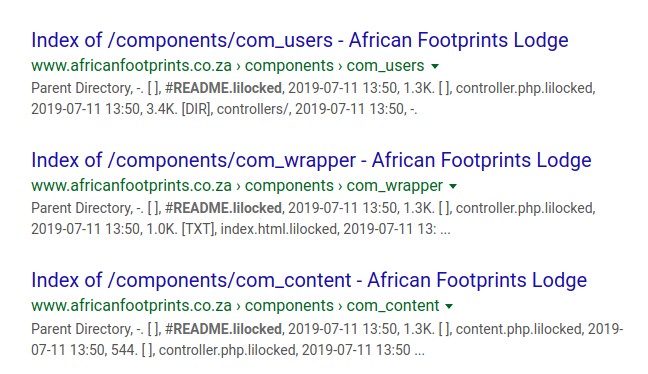
Here are 6 more African Footprint Lodge website hacked files:
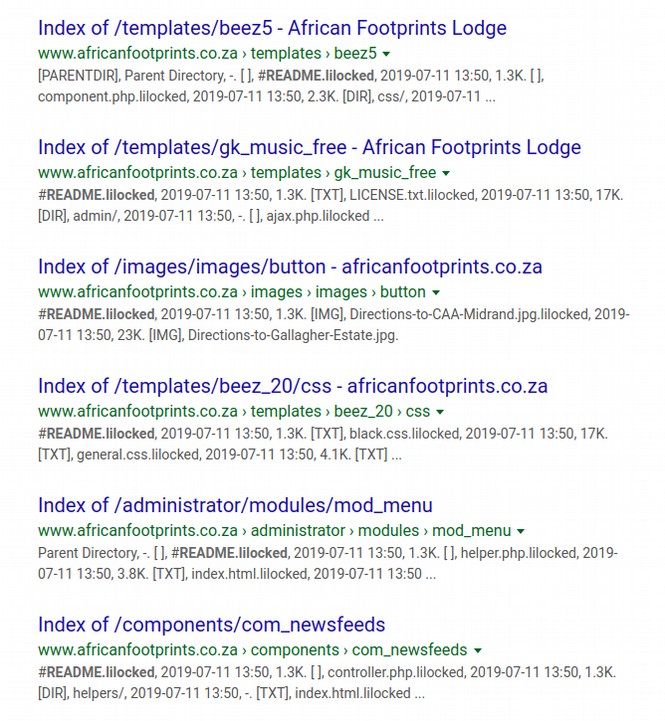
So instead of 6000 websites on 6000 servers being infected, it looks more like 6000 files on less than 1000 websites were infected. And many of these websites could have been on the same server – meaning that perhaps only a couple dozen out of the worlds 10 million Linux servers had infected files – and none of the files were actually in the core of any Linux servers.
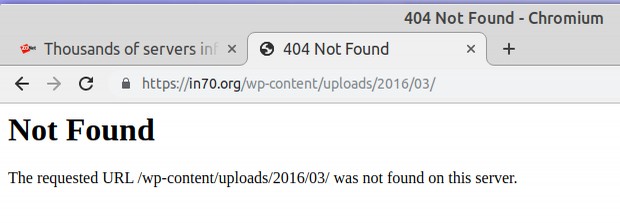
Many of the files were Wordpress files. Here is an example: https://in70.org/wp-content/uploads/2016/03/
Go to the link and you will find that this file is not even located on the server:
Here is another hacked Wordpress website file in Israel (this page has been translated from some non-English language). The actual hacked page is down so we were redirected to their broken link page which curiously still works:
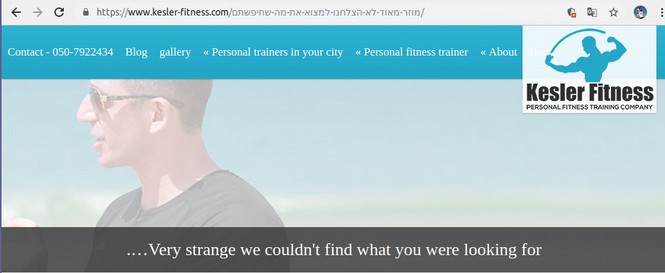
Even more amazing is the fact that the Home page of this website still works. Right click on the source code of the home page and you will find it is a Wordpress website. So why would the Ransomware hackers lock up some of the files on this website but fail to lock up the Home page? No hacker looking for some bitcoins to feed their family and pay their rent would ever do this.
Many of the files were not even websites. They were email sender files. Here is an example. https://zenles.ru/mail_sender/
The Zdnet article then mentions an obscure post on an even more obscure Russian forum. Here is a quote from the article: “The way the Lilocked gang breaches servers and encrypts their content is currently unknown. A thread on a Russian-speaking forum puts forward the theory that crooks might be targeting systems running outdated Exim (email) software. It also mentions that “the ransomware managed to get root access to servers by unknown means.”
Here is the link to the obscure post (translated into English with Google Translator): https://searchengines.guru/showthread.php?t=1021112
The forum is about Server Administration. The post is titled Hacking Centos 6/7. Centos is a version of Linux. The post was made on August 29, 2019. The poster states that a hacker broke into their Linux server and gained root access.
A second person responded saying: “Someone exim did not update.”
A third person disagreed saying: No, not Exim. He then linked to this post from July 30 2019: https://searchengines.guru/showthread.php?t=1019767
This post began with this sentence:
“Recently there was a critical vulnerability in Exim - now a critical vulnerability in dovecot - both allow you to remotely execute any code without authorization.”
But another person disagreed claiming: “On those servers that were infected before the vulnerability, Dovecot exim was updated!”
A third person noted that there has been more than one Exim security problem in the past few months and included a link to this page which cited a new Exim problem just patched at the end of August 2019: https://www.securitylab.ru/vulnerability/500668.php
In short, the claims made in the Zdnet article were vastly over-blown and completely unsupported. If anything, there was a problem with a particular Web server Email application called Exim. Exim is the default email program used on Linux Debian servers. But as I showed above, at least some of the servers that had locked files were Linux Ubuntu servers. Ubuntu uses a different and more secure email sender called Postfix. While Exim has a long history of security problems, Postfix is very secure. Here are some facts. In just the past 2 years, Exim has suffered 5 minor and 14 major security problems.
https://www.cvedetails.com/vulnerability-list/vendor_id-10919/product_id-19563/Exim-Exim.html
By comparison, Postfix has suffered only one minor security problem and not a single major security problem. https://www.cvedetails.com/vulnerability-list/vendor_id-8450/Postfix.html
During this same time, Windows Exchange Server has suffered from 14 minor security problems and 17 major security problems. https://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-194/Microsoft-Exchange-Server.html
In addition, Microsoft Outlook used with Microsoft Exchange Servers has suffered from 14 minor security problems and 15 major security problems. https://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-113/Microsoft-Outlook.html
In addition, Exim is the default email sender for Cpanel which is used on many servers. But Postfix is the default email sender on Webmin which is a free open source version of Cpanel. It is therefore unlikely that a person using a Ubuntu server would switch from Postfix to Exim and it is therefore unlikely that the Lilu Ransomware has anything to do with the security problems of Exim. One therefore really needs to wonder why the Zdnet article was quoting the misguided theory of some obscure person on a Russian forum??? This theory is obviously wrong on many levels.
The Obviously False Linux Ransomware Claim Spreads Like Wildfire
No other evidence was provided in the Zdnet article. Nevertheless, within hours this false story spread like wildfire to supposedly respected security and technology websites all across the Internet. A Google search I did on September 17 2019 revealed 33,400 results many with the exact same title:
Many of these articles were exact copies of the Zdnet article. Thus far, not a single so-called “security expert” has bothered either to look into the evidence provided much less challenge or disagree with this silly claim.
Instead, make even more extreme claims, noting that there are millions of Linux servers running outdated, un-patched and insecure versions of Exim software. This is a fact. But given how many holes have been found in the Exim software, the problem is not with the Linux servers, it is with the Exim software. In my humble opinion, the design of Exim is not secure and the design of Postfix is more secure.
The solution to this Exim problem is to demand that Cpanel support support Postfix and to ask Debian to also switch from Exim to Postfix (something Ubuntu has already done for very obvious reasons). This is the benefit of the diversity of free open source software. If one program has problems, there is quite often a more secure alternative that can be installed with just the click of a button. This is a problem that has been going on for years. But it can be fixed in a matter of minutes.
The only solutions to Lilu ransomware offered by the main stream security experts? Make sure you back up your files and use a strong password. Several articles explained how to remove this terrible ransomware from your Linux server.
Sadly, in every case, the instructions given were actually the steps to remove Lilu ransomware from Windows servers. Here is one of these identical articles: https://www.2-spyware.com/remove-lilocked-ransomware.html
Step 1 on all of these articles is to reboot your Windows 7, 8 or 10 computer into Safe Mode. Of course, there is nothing at all safe about using a Windows computer. Just read my article on the Hidden Dangers of Ryuk Ransomware and you will learn what is really happening in the wonderful world of Windows Ransomware.
As always, I look forward to your questions and comments.
Regards,
David Spring M. Ed.
Springforschools at gmail dot com