In the previous section, we provided a massive amount of evidence that your real enemy is not some 14 year old kid trying to hack your computer, but rather it is the most powerful government in the history of the world. This Deep State is using tools most of us could not even imagine. One researcher, Jacob Applebaum, who was given full access to the Snowden documents, described the NSA problem as being “worse than your worst nightmare.”

If you really want to know about what we are up against, watch this 60 minute talk by Jacob Applebaum. https://www.youtube.com/watch?v=b0w36GAyZIA
Should You Use an Antivirus Program on Linux?
There is currently a debate in the Linux community about whether we need to use an Antivirus program on Linux computers. Some claim that AV programs actually reduce security because they require elevated privileges to scan your documents and then “phone home” to report the results to AV companies who issue patches for the viruses. But this claim is only partially true. Not all AV programs “phone home.” And while it is true that your Linux computer is generally protected from AV programs, there are some exceptions.
I will give you two examples. First, I have helped students transfer their files from their former Windows computer to their new Linux computer. When we scan their files in Linux, we often find that the files they have imported from Windows include several hidden malware files. While these files may not execute on a Linux computer, it is still a good idea to get rid of them. Linux allows us to see these hidden files and to delete them.
Second, scanning has also uncovered the fact that some innocent appearing files downloaded from the Internet in fact have malware buried deep inside of them. One recent example was a series of images that had malware script buried inside of the metadata properties section of the images. These images can be cleaned up by using a program to wipe the metadata. But if the NSA can bury malware in an image, then just about anything is possible. So I think as long as we are careful about the kind of Antivirus program we use, then the pluses of the AV program can outweigh the drawbacks. With this in mind, we will download and use a program called Clam to scan our files for problems.
Install and Use Clam Antivirus Malware Scanner
I have tested more than a dozen AV programs. A lot of them do have security problems. But there is one that is safe and easy to use. It is called Clam. There are several versions of this program and several extra tools available. We will use the Mint Software Center to install a version with a Graphical User Interface. It is called ClamTK.
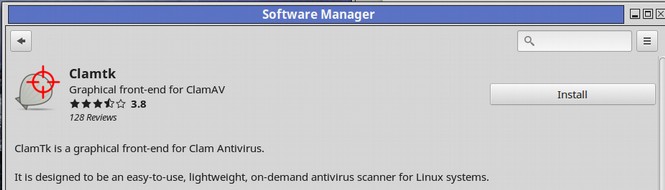
The software center downloads a really old version of ClamTK called 5.20. We can check for the latest version at this site: https://dave-theunsub.github.io/clamtk/
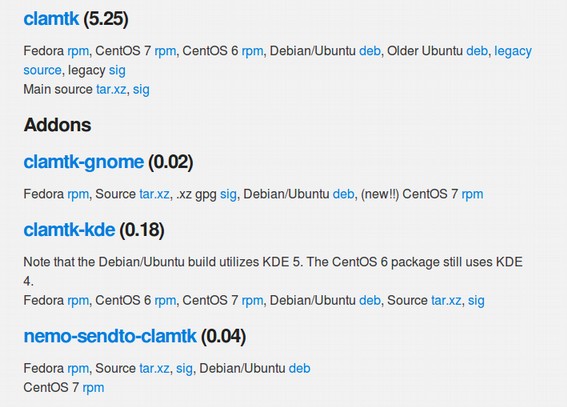
Click on the Debian/Ubuntu DEB file to download version 5.25. Now go back to the Mint Software Center and search for ClamTK again. The software center installed four programs - checked in green:
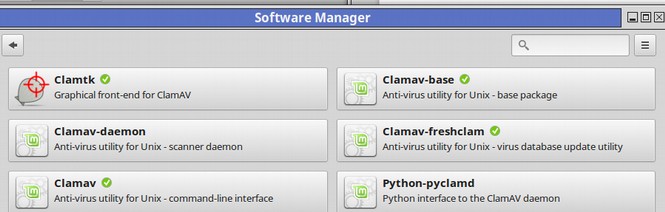
Now click on ClamTK and uninstall the main program only. Then go back a page. Three Clam programs were left after uninstalling the main ClamTK program. They are checked in green. Now transfer the latest DEB version of ClamTK from your Downloads folder to your apps folder. Right click on it and click Install with the DEB installer. Then open ClamTK from the Mint Menu:
We now have the latest version of ClamTK plus three important plugins installed. Here is the start screen:
Click on the green icon to confirm you now have the latest version. Then click on the Settings icon. Check Scan directories recursively. Scan directories recursively means to include the sub directories or internal folders and files.
Also check Scan files bigger than 20 MB and scan hidden files beginning with a dot. Then click Scan a directory. If you have a lot of files and folders this could take about 10 minutes per GB or 60 minutes for a 6 GB folder.
The Clam program scanned a total of 50,000 files in under one hour. There was only one possible threat detected. When done, the location of the potential threat is displayed:
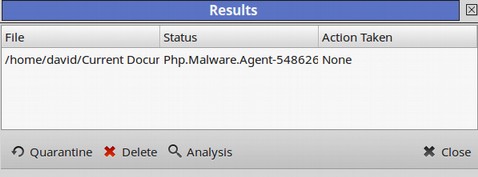
Click the item to select it. Then click Analysis. Clicking on the folder will bring up its location in our file manager:
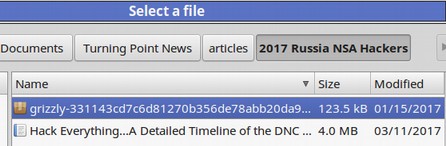
This is an NSA folder I have downloaded from a hacker site and been studying. Perhaps there is something in here I should be careful about. We will not delete this folder for now as I am still working on it. But it is nice to know that it might be dangerous. The ClamAV virus database is updated at least every four hours and currently contains nearly 4 million virus signatures. The “Whitelist” option provides the ability to skip specific directories during scan time. For example, you may wish to skip directories containing music or videos.
What is so Bad about using an AV program in Linux?
Independent tests confirm that Clam is able to find about 75% of all viruses. Since it is easy to use and can find a single bad file in 50,000 files, why would we not want to use Clam? Here is a site called Easy Linux Tips that makes a strong case against using Anti-virus programs on Linux: https://sites.google.com/site/easylinuxtipsproject/security
Here is a quote from this site: “Antivirus software itself is currently being attacked more and more, because it has by definition high permissions on the system and is often inadequately protected against hacking. This makes AV software an ideal target for hackers. See this article about research from 2014.”
This article referred to a study conducted by a person named Joxean Koret. In 2014, Koret gave a slide presentation at a conference called syscan360. Koret claimed that some AV websites are not encrypted. What was ironic about this claim is that Koret’s own website is not encrypted. http://joxeankoret.com/index.html
Instead, it is an insecure Weebly website. Koret also has an insecure Wordpress blog that is not encrypted. Koret must be busy. His latest blog post was March 2015 and he posts to his wordpress blog about once per year. http://joxeankoret.com/blog/
Even the scan360 website is not properly encrypted:
https://www.syscan360.org/
The primary sponsor of the syscan conference is Microsoft.

Since the terms Microsoft and security are mutually exclusive, this is clearly not really a conference about security. Koret is a “specialist in reverse-engineering, vulnerability research, and malware analysis.” Reverse engineering is exactly what the NSA does. To make matters worse, Koret cowrote a book with a Microsoft person who is also an expert in reverse engineering.
The company Koret works for is even more suspect. There website research page lists some articles – but these were published about 10 years ago. Meanwhile, the they have a job openings page filled with job openings that are just like NSA job openings. https://www.coseinc.com/en/index.php?rt=recruitment
Thus COSEINC appears to be little more than a fake company and a front for the NSA. I have previously written about dozens of such fake NSA companies – which are companies with lots of employees but no visible source of income. Here is a link to Koret’s syscan presentation in 2014.
This same slideshow is available here: https://www.slideshare.net/JoxeanKoret
In the 2014 presentation, Koret claims that most AV programs are not secure. In particular, he claims that Clam AV (the program we just used) use to suffer from an Infinite Loop vulnerability. The problem is that an infinite loop is not a security vulnerability, it is simply a coding error that was easily fixed. Ironically, how Koret found the security problems in the other programs was by scanning them with ClamAV! Some of these programs did have remotely exploitable vulnerabilities. But these are completely different from a coding problem. Koret went on to claim that Kapersky was also insecure. This claim was also misleading. He then claimed AV programmers do not know what they are doing:

In short, I would not regard Koret as a reliable source of information. What is important to understand is that security is not so much a tool we install on a computer but a process of doing research. It is important in this age of NSA deception to not blindly believe anyone. Instead, we need to research whether or not a person’s claims have any validity and who might be paying a person to make these claims.
Should you use a firewall on Linux Mint?
There is also a debate about whether we should use a firewall in Linux Mint. While a firewall is already installed, it is off by default and needs to be turned on. Some rightly claim that it does not need to be turned on because Linux does not use open ports for listening and “calling home” to Microsoft. An attacker can not do anything without a listening service that keeps a port open. However, if you use public wifi, then you should use a firewall. To enable the Mint Firewall, open the Mint Menu and click on Firewall Configuration. By default, the Mint Firewall is off. Click the Status to On. Then click File Quit.
Download Security Programs from the Mint Software Center
Even if we have secure computers, many Linux users also have websites that need protection and would like a better ability to monitor attacks coming from the Internet. The Mint Software Center offers two tools that can help with this process. The first is called Zenmap which is an easy way to input and output data from a tool called Nmap. Here is what the Zenmap screen looks like:
There are many tutorials on the Internet on how to use Nmap and Zenmap.
What’s Next?
In the next section, we will add a more secure encrypted email service called ProtonMail. Then we will add a more secure web browser called TOR.

