How you can be the next Edward Snowden
Not every one needs a more secure web browser to better hide their identity from the prying eyes of the NSA. But some people need as much security as they can get. Do you have inside information on corporate and/or political corruption you would like to get to Glenn Greenwald without getting discovered? Are you the leader of a protest group who would like to set up a secure communications system with other protesters? Do you have a medical condition that you want to research online without your insurance company finding out about it? Do you simply value your freedom and privacy and not want to be tracked by the NSA? Here is how you can set up a secure communication network by combining an encrypted email service with an encrypted web browser with visits to encrypted websites.

Get a Free Proton Mail Encrypted Email Account and access it with TOR
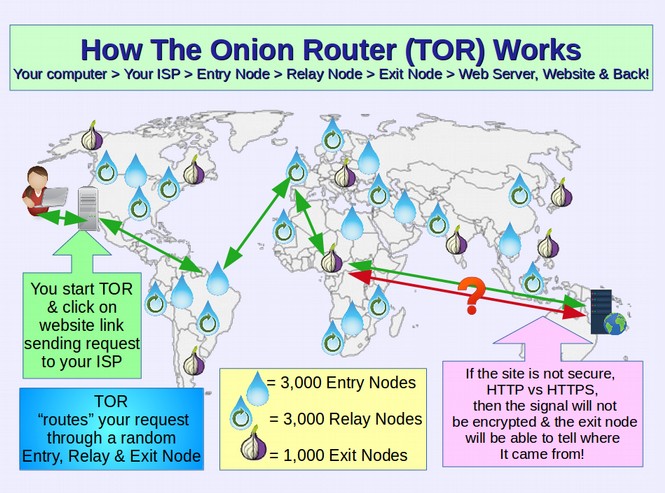
The free fully encrypted email service, Proton Mail has now reached 2 million users. On January 19, 2017, Proton Mail announced that they would provide even greater protection for their users by allowing them to access the login portal for Proton Mail via the TOR browser – thus hiding the IP address and location of the person accessing their Proton Mail account. This comes at a time when the TOR web browser is getting progressively easier to set up and use. The TOR browser is similar to the Google Chrome or Firefox web browser with the additional benefit of routing the path taken between your Home connection to the Internet (and your Home IP address) to the IP address of the website you are visiting by running it through a series of random IP addresses called the TOR network. All someone such as the NSA sees when viewing web traffic is the IP address of the TOR Exit node but not your IP address or the IP address of the website you are visiting.
There are currently about 1000 TOR exit nodes which makes it quite difficult, but not completely impossible for the NSA to monitor you in real time. The NSA would rather you did not use TOR. Proton Mail says they are taking this step to allow their users to take “active measures to defend against State sponsored censorship.” Users of the Tor Browser can now access their Proton Mail account anonymously at the following fully encrypted webpage: https://protonirockerxow.onion
Note that you can also visit this web page using any other web browser such as Google Chromium or Firefox. But visiting this page using a normal web browser will expose your home IP address to NSA server logs. We will therefore explain how to set up the TOR web browser for your Home computer. However, you should be aware that there is a downside to setting up a TOR browser. Sadly, all users of TOR are considered terrorists in the crazy eyes of the NSA. The NSA calls this “going dark.” You will be automatically subjected to increased surveillance simply for using the TOR browser.
There is a new, simple and free alternative started in 2016 which does not use TOR but which does somewhat hide your IP address. This is to download and use a web browser called Opera. Then click on a couple of buttons to set up its free VPS service (instructions are on the Opera website and are very easy).
In a matter of minutes, you can route your web access through Opera servers in several locations throughout the world. I have Opera set up to show Canada as the location of my IP address. The downside of routing your web traffic through the Opera network is that it will slow down access to web pages you visit. Instead of taking one second for a web page to load, it may take 3 to 10 seconds depending on the amount of content on the page. There are also paid services that route your web traffic through thousands of exit nodes. However, there is a downside to VPN’s in that the VPN provider can see all of your traffic and even monitor it. So choose your VPN wisely.
Those most likely to use TOR, Opera and/or a commercial VPN include whistle blowers such as Edward Snowden trying to access reporters such as Glenn Greenwald at the Intercept News Website. Again, there are many other groups of honest people who need privacy such as patients wanting to access their doctor, clients wanting to access their attorney or members of political and social groups wanting to access controversial political or social group websites. It is for these people that we provide these instructions. The more people who have the courage to set up the TOR browser, the harder it will be for the NSA to track whistle blowers and political change advocates. High traffic on the dark web will also make it harder for the NSA to take down TOR and/or Proton Mail – both of which have been attacked by the NSA.
December 2017 TOR Gets a Major Update
Tor protects your online location and IP address by encrypting your traffic in at least three layers and bouncing it through a chain of three volunteer computers chosen randomly from about six thousand “Tor nodes” around the world. Tor routes all its traffic over Tor random servers so you are browsing the web anonymously: The sites you visit see you as coming from a random point on the Internet and cannot trace your real IP address. A problem is that the final computer routing your traffic in this three-hop system, known as an “exit node,” can see your activity of connecting to a website, even if it doesn’t know where that activity comes from. The NSA, CIA and even some malicious hackers run their own exit nodes for exactly that surveillance purpose. This is why Tor users should be aware that they are only truly protected when visiting HTTPS protected websites only visit which ensures that the information that passes between the browser and the site remains encrypted. However, the NSA and others got around the random routing problem by setting up TOR nodes and then routing the traffic back through the same TOR node.
This shortcoming was addressed in December 2017 with a new version of Tor that makes sure that a node cannot loop the traffic back through itself. This is why you always want to download Tor from their website and make sure you are always getting the latest version of TOR. https://blog.torproject.org/new-stable-tor-releases-security-fixes-0319-03013-02914-02817-02516
How to set up and use the TOR browser
Currently about 3 million people use TOR which is a projected funded by the Electronic Freedom Foundation. If you would like to join them, first, go to the TOR project home page. https://www.torproject.org/ Then click on the TOR Download page. https://www.torproject.org/download/download-easy.html.en
While you can download the TOR browser for Windows or Apple, there is really no point in doing this because both operating systems have open back doors. So before using TOR, you really need to convert your computer to a Linux computer. Here are instructions on how to do this: https://learnlinuxandlibreoffice.org/
Assuming you have a modern Linux computer, click on the Linux 64 bit option. It is a large 70 MB file so it may take a while to download. Move the TOR folder from your Downloads folder to your Desktop. The folder name is:
tor-browser-linux64-7.0.11_en-US.tar.xz Click on the TAR folder to open it.
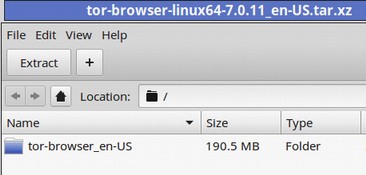
Click on Extract to extract it. Then click on Show Files. Then click Tor Setup to open Tor. This will start TOR. After a minute the following screen will appear.

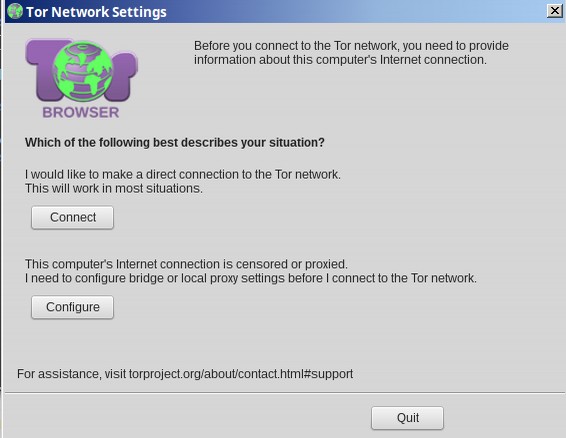
If you really need a secure connection, click on Configure to set up a TOR bridge. For now, just click on Connect. After about 1 minute of loading, the following screen will appear:
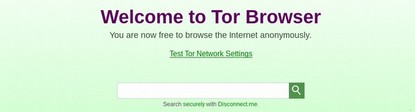
Click on Test TOR Network Settings
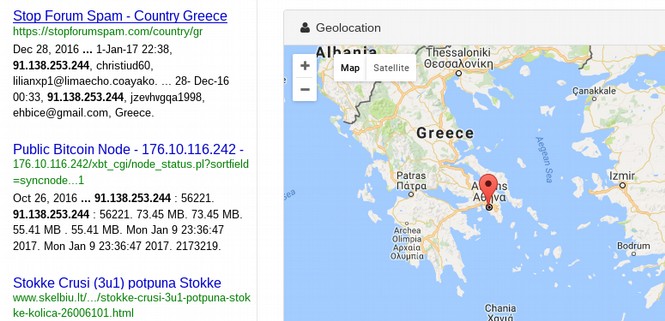
To research the TOR exit node IP address ,which will be different every time you start up TOR, click on the blue Atlas: It indicated this IP address is unnamed. It is also a TOR relay. Open a new browser tab and type in IP Lookup. There will be a Duck Duck Go search.
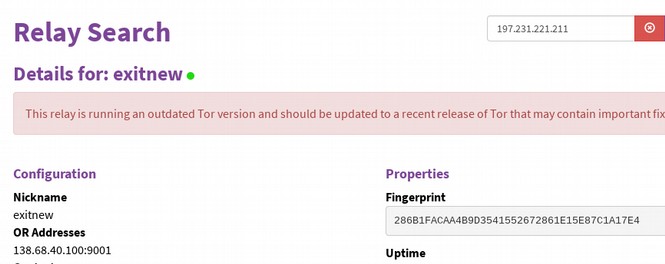
This is a known TOR exit node with no known location. Like most TOR exit nodes, it will likely be taken down soon because it has been reported to several services as a spam IP source. Clicking on the IP name on TOR will let you know if the Node is using the most current version of TOR:
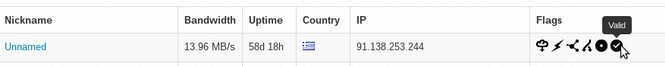
If you get a red warning like the above, it means that the Exit Node does not have the current version of TOR. If you really need safety, you may want to restart TOR and get a better exit node. You can learn more about this Exit Node IP address by clicking on Blacklist Check.
To learn more about this IP, go to https://www.threatminer.org

It turns out that this server is perhaps located in Athens Greece and is a bitcoin node in addition to being a TOR node.
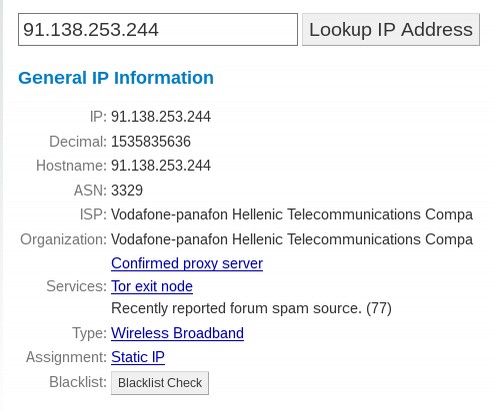
There are five pages of articles written about this IP address. These guys have been part of TOR since 2013. Here are a couple of other TOR exit node IP addresses along with some research about each:
197.231.221.211:443 This is ran by a company called Cyberdyne in Liberia that supposedly hosts 1 website but has ten registered IP addresses – usually indicating 10 servers.
138.68.40.100:9001 This exit node was ran by Digital Ocean in the US. It was only started in 2012 by a couple of guys but is now the second largest hosting company in the world.
Do a web search using TOR
Do a search on a controversial topic like the NSA. Look in the upper left corner of the browser. You will see that you are not only protected by the TOR network, but also by a program called No Scripts which prevents malicious scripts from being downloaded to your computer.
The upper right corner of your browser indicates that you are also automatically protected by HTTPS everywhere which gives priority to fully encrypted websites. Click on the menu to see you are also protected by several other TOR tools.
The browser itself is a modified version of Firefox. and includes several security plug-ins as well as security tweaks such as not caching any website data. Tor Project recommends installing the browser on a USB drive for more anonymity and portability. The USB drive needs to have 80MB free space. Close the browser window. To restart TOR, simply click on the Tor folder to open it. The green onion button to the left of the address bar is the Tor button. Click on the down arrow to the right of the green onion to see your Tor network settings and the circuit you're using.
In order for the NSA to find you, they would need to first download the server log for 31.31.74.69 which is in the Czech Republic. This would tell them that our connection was routed through a server in Germany. Then they would need to search the logs of two servers in Germany. Then they would find your IP address.
This is a lot of work which is why the NSA is likely to just give up and go after an easier target. But if the NSA wanted to, they could “break TOR” and track you down. We are just making it harder on them. If you want a more difficult circuit, just click on “new Tor Circuit for this Site.” Click on Privacy and Security Settings:
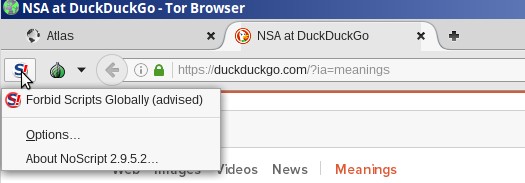
By default, TOR is set for the lowest level of security – blocking Flash and cookies while allowing most traffic to pass through. However, you can raise it to a higher level of security if you want to reduce the chances of someone sending you an attack. Above you can see that Medium Low forces video to be “click to play.” Some JavaScript functions are also blocked. Medium high also blocks font rendering (which is used in some attacks) and JavaScript is disabled completely. I really like this setting because JavaScript is basically an open back door to your computer while you are online. The highest level of security blocks some types of images. Some images carry malware in their properties settings.
Next click on TOR network settings:
Here you can change the way you access the Internet if you are in a special situation. Finally, you should read the TOR guidelines for secure web browsing. They explain that you should not use BitTorrent or install additional browser add-ons or open documents or media while online. The recommendation to only visit secure HTTPS sites is optionally enforced by a plug-in called HTTPS Everywhere. Even if you follow these recommendations, though, someone could detect the simple fact that you're using Tor, unless you set it up to use a Tor bridge relay. Many TOR bridges are not listed in the Tor directory. So the NSA would have more trouble finding them.
While browsing the web through Tor, you may find you need to use CAPTCHA to access some sites – especially sites that use Cloudflare – a projected that was partially funded by the CIA and is not really secure. Millions of sites use Cloudflare because they offer a free HTTPS service. This service claims to be encrypted – but it is not encrypted while passing through the the Cloudflare servers. Hopefully, these websites will eventually switch to a more secure free HTPPS certificate called Let’s Encrypt. In the meantime, you may want to skip using the Cloudflare promoted CAPTCHA and move on to more secure websites. Now let’s see how the Proton Mail log in page looks while using TOR.
Users of the Tor Browser can now access their Proton Mail account anonymously at the following fully encrypted webpage: https://protonirockerxow.onion
Open a new tab and enter the above URL.
Search for other TOR Onion Sites (AKA the Dark Web)
There are a bunch of Directories for learning about websites using the TOR onion.
The above link is only one of many. Tor hidden sites have URLs that end in .onion, preceded by 16 alphanumeric characters. There's even a Tor Links Directory page on the regular Web that's a directory of these Hidden directories.
Avoid Compromised Exit Nodes
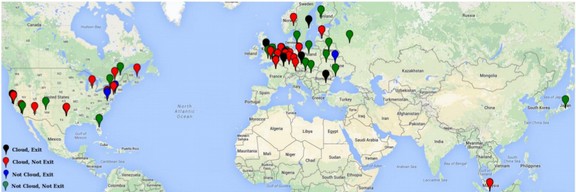
One research found that more than 100 out of the 1000 Tor Exit Nodes appeared to be spying on the Tor traffic. Here is a map of the compromised exit nodes he found:
We can study TOR exit node servers because TOR publishes a list of these servers. Here is a link to this list: https://check.torproject.org/exit-addresses
The NSA does not like TOR because it makes hacking harder for the NSA. The NSA has been known to attack the TOR project in the past. In fact, according to documents leaked by Edward Snowden, the NSA uses three or more cyber weapons to attack the TOR project and has referred to the TOR project as one of their biggest obstacles in their drive for “Total Awareness.” These weapons are called Quantum, Foxacid and XkeyScore. Here is an article that discusses these attacks calling TOR a “high priority target of the NSA”: https://www.schneier.com/blog/archives/2013/10/how_the_nsa_att.html
Recently a company called Cloudflare (which was started with funds from Google and the CIA) did a study of all the TOR exit nodes and found that over 60% of them were compromised and flagged for spamming. At some point, these exit nodes will be blacklisted – which is exactly what the NSA wants.
We have done our own detailed analysis of hundreds of TOR Exit Node IP addresses using ThreatMiner, Zenmap and other assessment tools. This research led us to the conclusion that about 20% of all exit nodes may be fake businesses that are fronts for the CIA, NSA, FBI or DNS. These are the greatest threat to your security but are expensive for the Deep State to run and maintain.
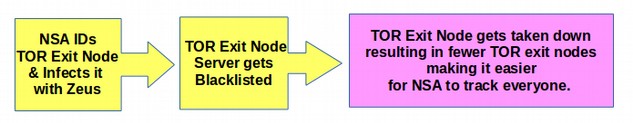
In addition, about 30% of all TOR exit nodes have been seriously compromised. They typically have “spam warnings” meaning they are in danger of being blacklisted and taken down. Some researchers have mistakenly assumed that these spammed web servers are due to people using TOR to anonymously distribute spam across the Internet. While this may account for some of the compromised sites, there is a relatively easy way for any server administrator to limit spamming such as throttling and monitoring or otherwise regulating the amount and type of emails coming from the server. We therefore believe that the majority of compromised sites have been successful attacked and infected by the NSA. Here is a diagram of how this happens.

Since we are certain that the NSA is repeatedly attacking TOR Exit Nodes – often with several hundred attacks every day – the good news is that about half of all Exit Node servers have been able to successfully defend themselves against these ongoing attacks. Therefore, what is needed is for the poorly managed TOR exit nodes to learn and adopt the practices being implemented by the well managed TOR exit nodes. This will likely require taking the compromised servers offline, wiping them clean, replacing UEFI with Coreboot and reformatting the hard drives with a secure version of Linux. It would also help immensely if organizations that need and benefit from TOR, including news organizations and attorneys, would take it upon themselves to volunteer to set up their own TOR exit nodes. It is essential that these nodes be set up on servers that are located outside of the US – as any server inside of the US can be taken down without notice or hearing under current draconian and idiotic US laws.
For more on our research into the NSA hacking of TOR Exit Nodes, see our special 85 page report called Hack Everything available for free download at turningpointnews.org.
So if the Exit Node has been hacked by the NSA or is owned or controlled by the NSA, what can we do?
The first step in our opinion is to use an exit node that is not located in the US – as all US servers are under the threat of compromise by the NSA and the vast majority of NSA owned TOR exit nodes are located in the US. The second step is to make sure the website you are visiting is fully encrypted with HTTPS. Now that HTTPS is free for all websites, thanks to a program called Let’s Encrypt, there is really no excuse for a website to not be fully encrypted. The good news is that the percentage of fully encrypted websites is now at nearly 80% and is increasing every year. Look for this green emblem in the URL bar:

Third, if you really want to hide your home computer, do not use it for visiting websites that are likely to be monitored by the NSA. Instead, create a TAILS Live USB and use TAILS to run some public computer in a different town. You can also use a computer at some public library with a fake ID. Fourth, never download files over TOR as these can be used to trace you.
There are many other more secure file sharing options. Fifth, if you have money and time, you should definitely set up your own server and offer to be a TOR exit node. The only way we will be able to save our freedom to communicate is if more people stand up to the NSA and take action to make their illegal invasion of our privacy a little harder.
More TOR Options.. TAILS, Ricochet, Onion Share and Retroshare
If you really want web security, you should consider using a TOR based operating system called TAILS - an acronym for The Amnesiac Incognito Live System. You can run TAILS off of a USB drive, which once removed, leaves no trace on the computer that ran it, making it virtually impossible to install malware on the user's machine. But as an added bonus, it also routes all data over Tor, adding an extra layer of security.
You should also consider using a next-generation tool called Ricochet that cuts servers out of the picture altogether. Instead, it turns your computer into an onion service, so that you can connect directly through Tor without any servers in the middle. For sharing large files, consider using TOR Onion Share (available from the Mint Software Center). This tool allows anyone to turn their computer into an onion service that anyone can connect to directly to download files, just as they might from a website—but without leaving any trace of their identity.
Another email alternative that cuts middleman servers completely out of the loop is a free open source program called Retroshare. Sadly, the link to this site is not secure: http://retroshare.net/index.html
Retroshare is a completely decentralized Internet. Retroshare allows you to create a network of computers (called nodes). Every user has its own node. The exact location (the IP-address) of nodes is only known to neighbor nodes. You invite a person to become a neighbor by exchanging your Retroshare certificates with that person.
Retroshare provides encrypted connections between you and your friends to create a network of computers. It also features various tools such as forums, channels, asynchronous messaging,... Retroshare is designed to provide maximum security and anonymity to its users beyond direct friends. You can make free and secure calls with the VoIP plugin. Catch up face to face with a video call. Send encrypted messages to other members of your network. Share files with your friends or with the whole network. Retroshare can be used over the TOR network so that not even your friends can see your IP.
The only downside to Retroshare is that you will have to convince your own network of friends to use it. Alternately you can join a trusted network of friends that is already using it. To download and try Retroshare, open a terminal and copy/paste the following:
sudo add-apt-repository ppa:retroshare/stable
Then copy paste the following:
sudo apt-get update
sudo apt-get install retroshare
Conclusion
Edward Snowden used Linux and TOR to connect with Glenn Greenwald. He did not have Proton Mail to fully encrypt his emails so he had to use a paid service. One mistake Snowden made was to use an Email service with servers in the US. This allowed the NSA to take possession of the server. I am sure in the future Ed will use servers located outside of the US. It is now possible for you to become the next Edward Snowden. All you need to do is set up a Linux computer, get a free Proton Mail account and set up the TOR browser – with or without a USB stick. The truth is these are only the initial steps in our search for privacy and security. Security is not any single action or any single tool. It is an ongoing process.
What’s Next?
In or final chapter, we will take a closer look at how you can learn more about Linux and the Linux community.

