We have provided a great deal of evidence that Linux computers, even without taking any security precautions are much safer than Windows computers. Recently, the University of Calgary suffered a ransomware attack and was forced to pay $20,000 Canadian (about $18,000 US dollars) to a hacker to regain access to files stored in 600 of their University computers. Unless the University changes their ways, there is nothing to keep them from getting hacked again and having their computers locked up again as it is likely that the hackers left a persistent calling card embedded in the University completely insecure computer system . Now you may be saying what does this have to do with me? I am using a Linux computer and all the recent ransomeware attacks were directed at Windows computers. But this is my point. Folks think that all they have to do is install Linux on their computer and set up a secure backup system and they are fully protected and do not need to worry about security. Nothing could be further from the truth. In this section, we will review some of the Advanced Persistent Threats (APTs) to Linux computers. Then in the next section, we will review some steps you can take to see if your computer has been attacked (the answer is yes) and steps you can take to improve your Linux security.
This chapter is not just about Linux Mint Security but about computer security in general. Switching from Windows to Linux is a good first step in securing your documents and data, but it is not the only step. Adding secure backups for documents and programs is a good second step but there are still more issues to be aware of in protecting our computer as well as our programs and documents. Earlier we explained how Linux uses a series of keys or security firewalls to protect the core of our computer. The Acer C910 (and all other Chromebooks) takes security even further by switching from the remotely controlled and thus insecure UEFI start up program to the much safer and faster Coreboot program. But we are still at risk if we continue taking dangerous behaviors on the Internet.
Understand Who is Attacking You and Why
I have spent more than 20 years studying the NSA and CIA (aka the Deep State) and the threat they pose to computer security. I am certain that even most Linux users greatly underestimate the power of the Dark Side and the diabolical ways of the Deep State. Researching what the Deep State is up to is an essential part of computer security. If you are not paying attention to the Deep State, then you are not paying attention to those who are bent on accessing and taking down your computer. It is kind of like being in a war in which only one side realizes that there is a war going on. The Deep State wants power and control over us. They do not want us to have a secure computer.
Beginning in 2010, Kaspersky Labs (one of the world’s leading security research labs) started publishing a series of papers about a new generation of computer viruses called Advanced Persistent Threats (ATPs). These included Stuxnet, Duqu, Flame, Gauss, Regin and the Equation Group. Their reports confirmed that these new viruses were related and developed by an un-named very large government. Reading these reports made it obvious that the NSA and CIA were out to gain control over every computer in the world by infecting every Windows computer with NSA/CIA implants.
In June 2013, Edward Snowden released thousands of NSA documents confirming that both Windows and Apple were NSA Prism Partners. Snowden protected himself by using a Linux computer. But he also took several other important security steps some of which we will look at it in this chapter.
In 2015 and 2016, the DNC Windows servers were hacked – leading to the election of Donald Trump. The problem was not merely that the DNC was using Windows servers – meaning a teenager could have attacked their server. Instead, members of the DNC were tricked into allowing hackers access to their computers. The DNC servers were also likely attacked from the inside. For more on this attack, read our January 2017 85 page report called Hack Everything. https://turningpointnews.org/hack-everything-special-report

Our research indicated that the DNC servers were likely attacked by the NSA in addition to other groups as part of the NSA program to literally hack everything. Our research also described for the first time a network of hundreds and perhaps even thousands of NSA/CIA servers both inside of and outside of the USA run by apparently real, but actually fake, businesses which the NSA/CIA uses to have infected Windows computers “call home” to the NSA/CIA. Our report also concluded that the NSA used fake signatures to mislead people into thinking that NSA attack programs were Russian attack programs.
Two months after my report, on March 7, 2017, WikiLeaks published a trove of original NSA/CIA documents that WikiLeaks labeled “Vault 7.” These documents confirmed that the NSA/CIA did in fact try to mislead researchers into thinking that NSA/CIA attacks were Russian attacks. https://wikileaks.org/ciav7p1/
These Wikileaks Vault 7 documents also confirmed that the NSA/CIA have at least 20 backdoors into Windows computer and at least 10 backdoors into Apple computers. These same documents confirmed that as of 2016, the NSA/CIA had no way into a Linux computer – unless they could convince Linux computer owners to grant them access. This chapter is about learning the tricks used to fool us and the steps you can take to avoid granting anyone other than yourself root access to your computer. This will require learning at least something about hacking tools and the Deep State. Don’t worry. We are only going to touch the surface with a quick overview.
On August 31, 2017, Wikileaks published even more NSA/CIA Vault 7 documents, this time about a program called Angelfire, which also targets the Windows operating system and focuses on controlling the boot system.
On November 7, 2017, Wikileaks published what it called Vault 8 which included the source code and logs for an NSA/CIA program called Hive which is basically the system used by the NSA to have your hacked computer “call home” to the NSA/CIA servers once it has been hacked. https://wikileaks.org/vault8/#Hive
Here is a quote from the Vault 8 release: “Each Hive implant anonymously registers at least one cover domain (e.g. “perfectly-boring-looking-domain.com”) for its own use. The server running the domain website is rented from commercial hosting providers as a VPS (virtual private server) and its software is customized according to CIA specifications. These servers are the public-facing side of the CIA back-end infrastructure and act as a relay for HTTP(S) traffic over a VPN connection to a “hidden” CIA server called 'Blot'.”
“Digital certificates for the authentication of implants are generated by the CIA impersonating existing entities. The three examples included in the source code build a fake certificate for the anti-virus company Kaspersky Laboratory, Moscow pretending to be signed by Thawte Premium Server CA, Cape Town. In this way, if the target organization looks at the network traffic coming out of its network, it is likely to misattribute the CIA exfiltration of data to uninvolved entities whose identities have been impersonated.”
Here is a Snowden released image showing the NSA network has over 700 servers around the world.
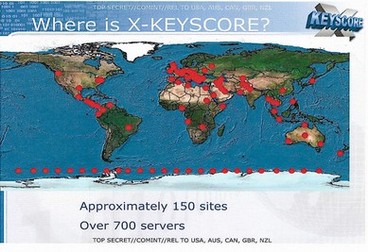
Xkeyscore is used through over 700 servers at 150 sites around the world.
http://www.theguardian.com/world/interactive/2013/jul/31/nsa-xkeyscore-program-full-presentation
Vault 8 confirmed not only the conclusions in my January 2017 report but also my long held belief that the NSA/CIA were waging a war against Kaspersky. The Deep State claims that Kaspersky is a tool of the Russian government but has provided no evidence to support this claim. In fact, there is a great deal of evidence that Kaspersky is completely independent from the Russian government. This is important because the highly detailed Kaspersky reports over the past 7 years have been one of my best resources for understanding the NSA/CIA hacking programs. It is natural that the NSA/CIA would want to destroy one of the few groups in the world that was exposing what the NSA/CIA Deep State was up to.
On September 13, 2017, the US Department of Homeland Security issued an order directing all US agencies to stop using Kaspersky anti-virus programs claiming, without any evidence, that Kaspersky was connected to the Russian government and was a security risk. https://www.dhs.gov/news/2017/09/13/dhs-statement-issuance-binding-operational-directive-17-01
|
Quote
|
“Kaspersky Lab has never helped, nor will help, any government in the world with its cyberespionage or offensive cyber efforts. Ask yourself one thing: ‘if these recent allegations are true, where’s the evidence?” |
On October 24, 2017, Kaspersky released a report explaining how they had obtained access to the NSA program known as the Equation Group. Since early 2014, Kaspersky had been investigating a network of NSA attacks on hundreds of computers in more than 40 countries. Kaspersky called these attacks the “Equation Group” and noted in a February 2015 report that the code used by the Equation Group was similar to previous NSA attack codes used by an NSA program called Stuxnet. In February 2015, they published a report linking them all together. Kaspersky publishes a report on the “Death Star of the Malware Galaxy” which it called the Equation Group (which we know is the NSA). The relationship of Stuxnet to other NSA cyber weapons was confirmed in this detailed analysis.
https://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/
https://securelist.com/files/2015/02/Equation_group_questions_and_answers.pdf

The Kaspersky researchers described a group they called the Equation group which was infecting computers and websites all over the planet. The report noted that the techniques being used were linked to techniques and malware programs previously developed and used by the NSA including the Flame and Stuxnet viruses which the US used to attack Iranian computers.
Here is their diagram of the relationships between the various Equation Group cyber weapons. Note that Stuxnet, Flame and Gauss are all directly related:
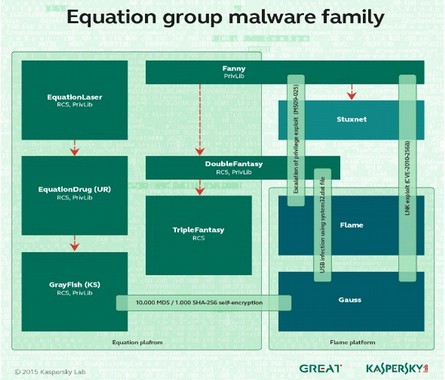
Here is a quote from their 44 page report: “All the malware we have collected so far is designed to work on Microsoft’s Windows operating system. The malware callbacks are consistent with the DOUBLEFANTASY schema, which normally injects into the system browser (for instance, Internet Explorer on Windows)… The Equation group uses a vast infrastructure that includes more than 300 domains and more than 100 servers.”
On September 11, 2014, an NSA employee illegally brought home NSA Equation Group documents. He then placed these documents on an insecure Windows computer on which he had installed Kaspersky software. He then disabled the Kaspersky AV program in order to install an insecure “pirated” copy of Microsoft Office. To activate the pirated copy of MS Office, the NSA employee used a pirated “key” program. Unfortunately, the pirated key program had a virus on it that installed a malicious backdoor on his computer. In order to clean this backdoor off of his computer, the NSA employee then enabled the Kaspersky program again which detected the malicious backdoor. Then NSA employee then scanned his computer several times with the Kaspersky AV program in an effort to delete the virus. However, because he had previously set the AV program to send reports any “virus” to Kaspersky, the virus was sent to Kaspersky. Apparently, the NSA Equation group documents got caught up “in the mix” and were also sent to Kaspersky. The version of Kaspersky software used by the NSA employee was the “home version.” When Kaspersky realized that they had been sent top secret NSA documents, they immediately deleted the files.
Significantly, after Kaspersky issued their landmark report on the Equation Group in February 2015, several other similar Equation Group files were sent to them by the same process from the same IP range (same general location) as the 2014 NSA “accidental” document release. This is a quote from the Kaspersky report:
“These seem to have been configured as “honeypots”, each computer being loaded with various Equation-related samples.”
A honey pot is where one sets up a cyber trap hoping to frame someone else for doing something bad when really they were simply being trapped. In short, Kaspersky was saying the NSA had been trying to frame them – but that Kaspersky had not fallen for the bait.
Who is telling the truth here… the NSA/CIA Deep State or Kaspersky? Think about this.
Why was an NSA Agent using a Russian anti-virus program in the first place?
Why was an NSA Agent bringing home top secret Equation Group documents?
Why was an NSA agent – who is supposedly a security expert and member of one of the NSA top spy groups - using an insecure Microsoft computer instead of a secure Linux computer at his home?
|
Key Point
|
Why was this highly paid NSA agent who likely is paid more than $100,000 per year, downloading a pirated copy of Microsoft Office – a program he could use online for free or download for a few hundred dollars? |
Why did this NSA agent use a pirated key program to activate MS Office when this pirated key program had been known to contain viruses more than one year before he used it?
Why did this NSA agent deactivate Kaspersky to run the pirated key program? Actually, we know the answer to this question – Kaspersky was set to block this known malware program from running. So the only way the pirated key would run was by first disabling Kaspersky. Then after apparently deliberately infecting his computer, the NSA agent turned Kaspersky back on and set the program to send the NSA software to Kaspersky.
The claim by the mainstream media now is that perhaps this guy was dumb. But this guy was a ten-year veteran of the NSA top spy program. So he was anything but dumb. Instead, it is far more likely that he was part of a very carefully planned plot to frame Kaspersky.
On December 2, 2017, the name of this NSA hacker was finally revealed as he was supposedly charged for taking home top secret documents from the NSA. Here is a quote from a Security Week article:
“A member of the US National Security Agency's elite hacking team has been charged with illegally removing top secret materials, in an embarrassing breach for the crucial electronic espionage body. The Justice Department said Friday that Nghia Hoang Pho, 67, a 10-year veteran of the NSA's Tailored Access Operations unit, which broke into computer systems, agreed to plead guilty to a single charge of removing and retaining top-secret documents from the agency.” http://www.securityweek.com/elite-us-government-hacker-charged-taking-secret-information
Do you really believe that a ten-year veteran of the NSA’s top hacking team is really going to use a known infected key to activate a bootleg copy of Microsoft Office on his home computer – right after loading an illegal copy of top secret Equation Group documents to this same computer – and then set the Kaspersky AV program to automatically send the Equation Group documents to Kaspersky – and be so dumb that he failed to understand what he was doing?
Unfortunately, but perhaps not surprisingly, the US and UK governments are willing to believe this ridiculous story. In December 2017, the UK Spy Agency (which is directly linked to the NSA/CIA) issued a warning for UK businesses to stop using Kaspersky Antivirus programs. https://www.ncsc.gov.uk/information/letter-permanent-secretaries-regarding-issue-supply-chain-risk-cloud-based-products
Again, absolutely no evidence was offered to support any of their claims – other than the fact that Kaspersky had been caught red handed with a copy of a top secret Equation Group document – which had been sent to them directly by an NSA agent – six months after Kaspersky already had the Equation Group documents sent to them by computers in 40 different countries.
Why the NSA Framed Kaspersky
Here is a quote about how Kaspersky has been the number one obstacle for NSA spyware programs:
|
Quote
|
“Kaspersky appears to be the sharpest thorn in the side of government hackers. In the past few years, the company has proven to be a prolific hunter of state-sponsored malware, playing a role in the discovery and/or analysis of various pieces of malware reportedly linked to government hackers, including the superviruses Flame, which Kaspersky flagged in 2012; Gauss, also detected in 2012; Stuxnet, discovered by another company in 2010. In February 2015, the Russian firm announced its biggest find yet: the “Equation Group,” an organization that has deployed espionage tools widely believed to have been created by the NSA and hidden on hard drives from leading brands, according to Kaspersky. In a report, the company called it “the most advanced threat actor we have seen” and “probably one of the most sophisticated cyber attack groups in the world.” |
If you want security, it is important to know who your friends are and who is trying to attack you. Who is making the malware and who is trying to protect your from malware. It has been clear for years that the maker of the malware has been the NSA. Kaspersky has been protecting us from NSA malware. Sadly, in 2017, things got a lot worse – and will likely be even more difficult in 2018.
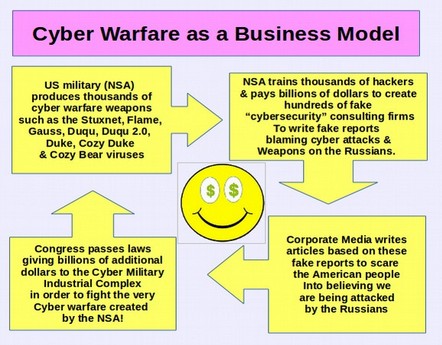
Hackers Heaven
On Friday, May 12, 2017, the Wanna Cry Ransomware virus began infecting hundreds of thousands of Windows computers in more than 150 countries. The cyber weapon mainly affects businesses that use local area networks. Once one computer is infected, all the computers on the network are taken over. Businesses from hospitals to banking ATM machines were shut down. The virus encrypts all the data on your computer and demands a payment of $300 if you want your computer back. Here is an image of the screen that appears after the hackers have taken over your computer:
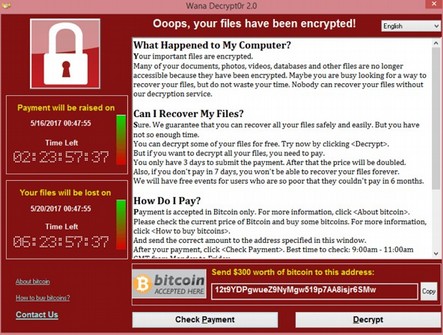
The Wanna Cry virus uses two cyber weapons called Eternal Blue and Double Pulsar. Thanks to the Wikileaks Vault 7 release on March 7, 2017, we know that both of these cyber weapons were developed by the NSA. These cyber weapons were developed by the NSA along with hundreds of other cyber weapons using tax payer dollars. But instead of protecting us, these offensive weapons are being used against us. https://wikileaks.org/ciav7p1/
In August 2016, a group called the Shadow Brokers was able to download a huge number of NSA Cyber Weapons. These weapons have now been released into the wild - meaning just about any computer hacker is now able to set up their own version of the NSA to attack Windows computers. According to one security expert, “It’s a business model that works and you don’t need a lot of investment to actually get a decent return. You can buy ransomware kits on the dark web, you can buy all the tool sets you need to undertake your own ransomware campaign quite easily.”
http://heavy.com/tech/2017/05/wannacry-wannacrypt-decryptor-virus-attacks-microsoft-nsa/
Also thanks to Wikileaks, we know that these cyber weapons take advantage of the open back door in the Windows operating system to infect and take over Windows computers through the Windows Web Browser (which is the open back door). Many security “experts” have described this as a “file sharing” problem. But it is actually much bigger than that. On March 14, 2017, Microsoft issued a “patch” which they claimed solved the Eternal Blue problem. But the patch is merely a band-aid that places some restrictions on file sharing but does not address the underlying problem – which is the open back door in the Windows computer operating system.

Predictably, on May 15, 2017, a stronger mutation of the WannaCry virus began attacking computers. Europol, the European police agency warned, “The hackers have already evolved the malware, and will probably continue to do so.” According to Zero Hedge, “at least a dozen other NSA tools are currently being discussed and worked on as the basis of potential new cyber weapons on hacking forums on the dark web.”
On May 16, 2017, Shadow Brokers issued a statement claiming to have many more hacking tools they will be releasing in the coming months. Here is a quote: “TheShadowBrokers Monthly Data Dump could be being web browser, router, handset exploits and tools, select items from newer Ops Disks, including newer exploits for Windows 10, compromised network data from more SWIFT providers and Central banks.”
Who is behind the Wanna Cry virus? It could be anyone from a 14-year-old kid with a new laptop to the Italian mob. Cyber blackmailers just need an Internet connection and a laptop plus a little knowledge of how to access the cyber weapons now being given away for free on the Dark Web.
According to a German security expert: “Just because the attacked affected 200,000 computers and 100 countries, there doesn't have to be a large-scale structure behind it. The weapon - the software - is that powerful.”
After a worldwide attack with a cryptoworm called “WannaCry” in May, another attack with a strain of ransomware called “Petya” started in June 2017. Malware has come a long way in the last ten years. According to analysts with IT-security software firm G Data, the number of new malware specimen is likely to reach more than 7.4 million this year alone. According to data provided by IT-security institute AV-Test, ransomware (such as “WannaCry” and “Petya") confirms that the potential for widespread computer damage is growing every year.
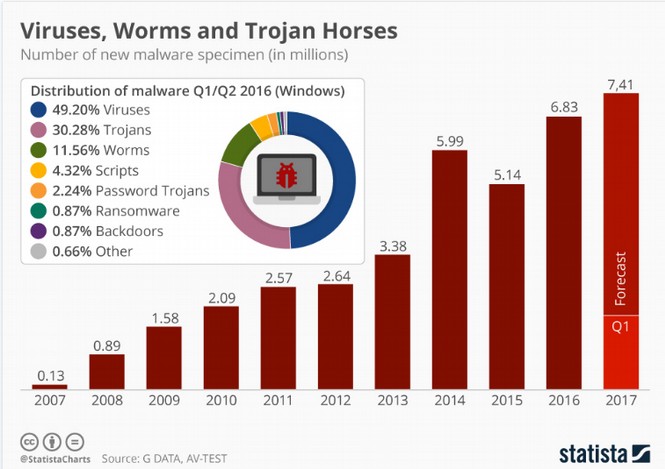
https://www.statista.com/chart/10045/new-malware-specimen-and-share-of-windows-based-malware/
“Under the 1994 law, the Communications Assistance for Law Enforcement Act (CALEA), any company considered a “communications provider” has to allow government agencies access when a valid court order is served… the FISA Court issues more than a thousand classified warrants a year for Americans' data. One former NSA analyst likened it to a “kangaroo court with a rubber stamp,” as it keeps very few records, of which many are kept in the utmost secrecy and away from public scrutiny…
FISA warrants issued by the FISA court each year. Nearly every request for data has been granted. The owner of an ISP has disclosed how the FISA order process works: “They wanted to come in and put in equipment on my network to monitor a single customer. The customer they were monitoring was a particular website that was very benign. It seems ridiculous to me. It was beyond absurd. It wasn’t like a guns and ammo website...We had to facilitate them to set up a duplicate port to tap in to monitor that customer’s traffic. It was a 2U (two-unit) PC that we ran a mirrored Ethernet port to. [What we ended up with was] a little box in our systems room that was capturing all the traffic to this customer. Everything they were sending and receiving. I called six months into it and said, “How long is this going to go on?” and they said, “I don’t know.” I went on for nine months. There have been no [related] arrests that I have heard of. We run a Tor node, in some ways as an affirmation of our belief that there are legitimate reasons for being anonymous on the Internet. Some illegal traffic comes in through Tor node and we get a federal request through the FBI or DOJ (Department of Justice). I respond to them and say that this is a Tor node [and therefore inaccessible, even to the ISP]; that is usually the end of it. They realize what that is, and it is a dead end.”
In the summer of 2016, Shadow Brokers dumped some of the stolen NSA tools on the open Internet for all hackers to use. On the same day Guccifer 2.0 -- a character that US intelligence agencies think was created by Russian military intelligence to serve as a conduit for the data stolen from the Democratic National Committee in the run up to the US presidential election, also broke 'his' silence. “The US. intelligence agencies have published several reports claiming I have ties with Russia. I'd like to make it clear enough that these accusations are unfounded. I have no relation to the Russian government. I was acting in accordance with my personal political views and beliefs,” he said.
It is not just Guccifer and Shadow Brokers we have to worry about. Every year, our own government trains thousands of people how to conduct offensive cyber warfare attacks. As just one example, look at the annual NATO cyber warfare game, Locked Shields. Here is a picture of Berylia and Crimsonia fighting each other in the Lock Shields Cyber Warfare game.
“The red team can pretend to be various hacker groups—from stealthy 'advanced persistent threat' actors to noisier less skilled hacktivists—or perhaps both at the same time, depending on the scenario. The attackers will attempt to do things like steal documents which are then leaked to the in-game media.”
In 2014, at a global security conference, Mikko Hypponen, chief research officer at security company F-Secure, said “If someone would have told me ten years ago that by 2014 it would be commonplace for democratic western governments to develop and deploy malware against other democratic western governments, that would have sounded like science fiction. It would have sounded like a movie plot, but that's where we are today.” http://www.techrepublic.com/article/inside-the-secret-digital-arms-race/
If you would like to see cyber warfare and hacking attacks in real time, then visit the following website: https://threatmap.checkpoint.com/ThreatPortal/livemap.html
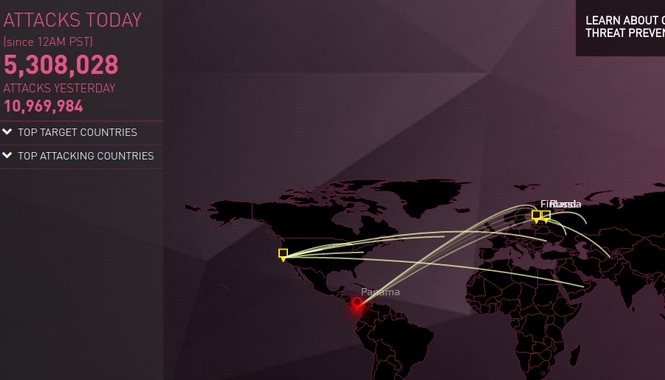
Note that there are now about 10 million cyber attacks every day. If you want to learn how to protect yourself or your online business from cyber warfare, there are several free courses and free attack analysis tools on the Internet. Here is a link to an article I have written about cyber security for website owners. https://createyourowninteractivewebsite.com/3-security
Sounding the Alarm
We have written numerous articles over the years warning that US spy agencies, including the NSA and CIA, are completely out of control. It is not merely that the NSA and CIA waste billions of tax payer dollars. The cyber weapons they create are so dangerous that they are capable of bringing down the entire US and world economy. Imagine the banking system, transportation and energy computer networks all crashing at the same time.
|
Caution
|
Imagine a 14-year-old kid being able to download everything needed to create the cyber version of a nuclear bomb and getting it all for free in a matter of minutes. This is the kind of danger the NSA has inflicted on all of us by creating these out of control cyber weapons. |
Here is a diagram from an article I wrote based on the Wikileaks releases and the earlier Snowden documents. According to various Wikileaks CIA documents, here is what the CIA and NSA are doing:
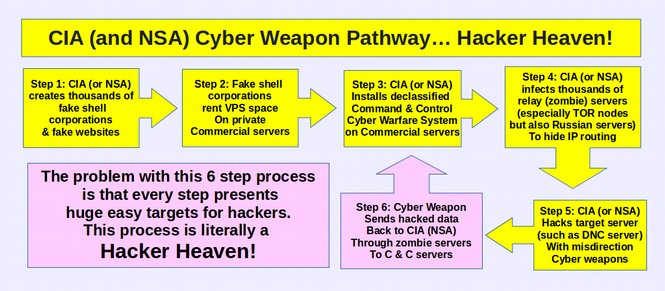
In short, thanks to the NSA’s arrogant mis-use of billions of dollars of US tax payer funds, this latest cyber attack is just the beginning of a more long term assault on Windows computers. Over the coming days, weeks and months, we can expect hackers to create more powerful viruses all thanks to the NSA and the Windows open back door.
As computer expert Jacob Applebaum once said, the NSA spying program is “worse than your worst nightmare.” Instead of wasting our time worrying about Russian hackers, we should have been worried about our own NSA – which is after all more than ten times larger than the Russian hacking team.
Five years ago, we wrote a book called Free Yourself from Microsoft and the NSA, in which we described this Windows open back door and NSA cyber weapons. I predicted that this lethal combination would eventually lead to mass attacks by computer hackers. https://freeyourselffrommicrosoftandthensa.org/
Others including William Binney and Edward Snowden (both formerly with the NSA) have also warned against the danger of allowing the NSA to access all Windows computers via the Windows back door. The problem is that any backdoor that can be used by the NSA can also be used by hackers once they gain possession of the NSA cyber weapons.
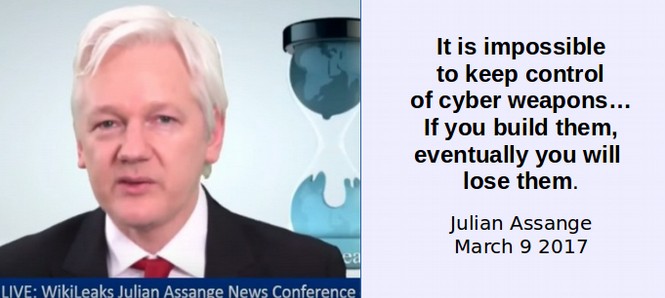
Assange noted during his March 9, 2017, press conference that eventually consumers around the world will no longer trust US technology manufacturers – which will also cost US corporations billions of dollars. The mere fact that US corporations like Microsoft and Apple have already been confirmed to be Prism Partners of the NSA should cause folks even in the US to not trust US technology firms. The new Wikileaks revelation that the CIA has compromised 22,000 servers in the US should make it clear that we cannot trust US web servers and web hosts – a fact that I wrote about in a book over a year ago. https://createyourowninteractivewebsite.com/1-start-here/1-3-how-to-protect-your-website
Clearly the NSA and CIA are trying very hard to break into the Linux operating system. But so far, their only success has been by compromising the UEFI startup program. This is why I recommend that even if you are using a Linux computer, you should not use the UEFI startup program and instead to use the COREBOOT startup program. Meanwhile the Apple and Windows pages in the Wikileaks documents are filled with dozens of attacking methods.
Conclusion… It is time for Real Computer Security
These are important security issues that affect every computer user in the entire world. It is time not only to end the NSA and CIA but it also time for every computer user who cares about the future of our economy to move away from unsafe and badly designed operating systems such as Microsoft and Apple and replace them with the free, secure Linux Operating system.
What’s Next?
Now that we have a better idea of the pervasive nature of computer hacking, and that there are some powerful agencies trying to control our computers, let’s look at some free tools for protecting our Linux computers.




