In this section we will cover what is perhaps the most frightening part of the Microsoft program to take control over our computers. It is a new program called UEFI. It can be more accurately thought of as the Microsoft Kill Switch. Microsoft has required that this sinister “feature” be added to all Windows 10 computers.
|
Quote
|
We call Windows 8 ‘Windows Prison Edition’ because it’s designed to require people to send data to Microsoft servers, and of course, Microsoft will hand over any of that data to the US government on request. It puts the users in prison. Richard Stallman July 2013 |
Microsoft creates obstacles to prevent you from adding Linux
Sadly, Microsoft does not want people to use Linux. Microsoft seems to be doing everything they can to keep their corporate monopoly. They want the money that will come from forcing XP users to pay $500 each to change from Windows XP to Windows 10. There are 600 million Windows XP users in the world today and Microsoft wants all 600 million XP users to spend $500 each to “upgrade” to Windows 10 and Office 365. Microsoft stands to lose $300 billion dollars if folks ever learn that they can easily switch to Linux and LibreOffice and get a much more stable and reliable word processing system for free.
The Windows operating system is the key to maintaining the Microsoft computer monopoly. So Microsoft has placed all kinds of malicious roadblocks, obstacles and traps to prevent people from using Linux. Up until 2007, Microsoft maintained control over their lucrative monopoly by using their Internet Explorer Open Back Door to crash pirate copies of Windows. However, with the introduction of Linux Ubuntu and Linux Mint in 2007, suddenly computer users had a much better and more user-friendly option. It was only a matter of time before folks realized there was something better and that would be the end of the Microsoft Monopoly.
Switching to Linux also meant that the NSA would no longer be able to remotely control our computers.

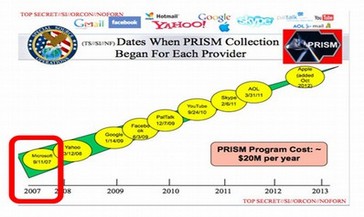
Something had to be done. Neither Microsoft nor the NSA want people to control their own computers by switching to Linux. A way was needed to control computers even if folks switched to Linux. The solution to this problem was to replace the former “BIOS” startup program to a secret UEFI startup program – a program that was 20 times bigger that BIOS and used encrypted coding to prevent users from knowing what was in it. As we detail below, this switch occurred in late 2007 – the same year Microsoft became an NSA “Prism” Partner.
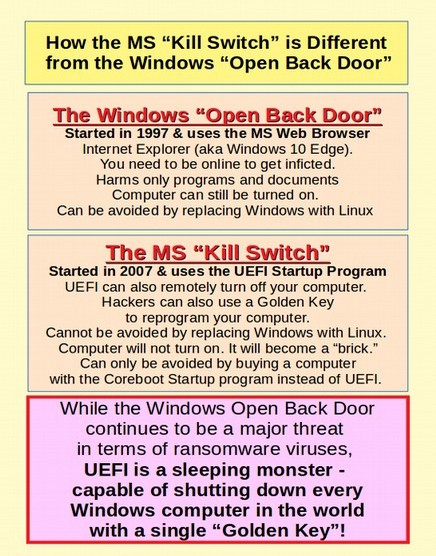
Because it is common for folks to confuse the Windows Open Back Door with the Microsoft Kill Switch, we have created this graphic that explains the difference:
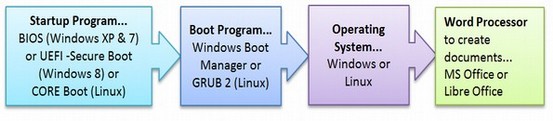
What is a Start Up Program?
To understand the problem with UEFI and Secure Boot, it is helpful to know a little about how computers start up. When you push the POWER ON button on your computer, this initiates a Start Up program. Historically, the universal startup program was called BIOS which stands for Basic Input Output System. This Start Up program is installed by the computer manufacturer. BIOS determines what program boots next and in what order.
Typically, the next program to boot is the Windows Boot Manager. This starts Windows which then can be used to start Windows based programs such as MS Office. There are free open source versions of all of these as shown below:
BIOS versus Core Boot
BIOS is a very old and stable system that allows you to have four or more operating systems installed into four or more “partitions” on your computer. Because BIOS is not a free open source program, and because it slowed down the performance of Linux, a group of Linux programmers spent several years developing an extremely fast, safe and free Startup program called Core Boot. While Core Boot is free and could easily be installed on all computers, manufacturers have continued to use BIOS until Windows 8 came out in 2012.
EFI turns into a monster called UEFI
While Core Boot was being developed, a commercial Start Up program called UEFI was being developed. UEFI stands for Unified Extensible Firmware Interface. UEFI is based on a program called EFI which was an attempted by Intel to update BIOS. EFI did not have the Secure Boot “feature” and neither did UEFI until late 2007. Like BIOS, UEFI requires two separate drivers – one for the firmware and one for the operating system. This makes UEFI slow and difficult to work with. But the biggest complaint about UEFI is that it placed control for programs in the hands of software companies such as Microsoft rather than in the hands of the computer owner (you).
|
Quote
|
UEFI stands for Unwarranted Elimination of your Freedom and Independence (or something like that). - Anonymous |
In fact, for computer users, Secure Boot is like putting on a pair of handcuffs.
This does not stop hackers from attacking your computer – because hackers are experts at removing handcuffs. But it does make it harder for you to work with your computer – because now you need to learn how to remove the Secure Boot handcuffs before you can install Linux.
One of the new “features” of Windows 10 is “Secure Boot.” While it does very little to protect your computer, it does make it much more difficult to add another operating system, such as Linux, to your computer. Beginning with UEFI version 2.2, UEFI added a new feature called Secure Boot. This uses a special key, which is nothing more than a digital image, to be activated before any operating system, or any other program can be loaded into the computer.
There are several absurd things about Secure Boot. First, Secure Boot is not a very secure system. This is because digital images are easily copied. Recall that fake digital images were used by Flame to attack Microsoft Security Updates. We are now all well aware that this digital signature system does not work. Second, generic keys are already in existence to bypass the system. It seems that everyone has been given a key to your computer except you! Third, Secure Boot adds huge costs to computers because manufacturers have to pay private companies to have Secure Boot and UEFI installed. For all of these reasons, Core Boot is a much less expensive and more effective security system. Core boot lets you control the final configuration. This is not only the most secure system – it is also the easiest system for the end user... which is you.
Despite these issues, Microsoft has required all computer manufacturers to use UEFI with Secure Boot on all of their Windows 8 and 10 computers. If Microsoft was really concerned about speed or security, they would have insisted on using Core Boot. So the insistence on UEFI with Secure Boot seems to have only one purpose – to make it difficult to impossible to install Linux on your computer – in order to maintain the Microsoft Windows monopoly (and/or to help the NSA).
To make matters worse, Microsoft has insisted that manufacturers use a special key controlled by Microsoft – rather than a key controlled by the manufacturer. This gives Microsoft total control over your computer – not just the backdoor and the front door – but also the Startup program.
One of the worst of these monopolistic predatory practices is forcing computer manufacturers to sign exclusive agreements to prevent manufacturers from loading a free Linux operating system into computers instead of the Windows operating system. Because many users find it difficult to add an operating system to their computer, a far better option would be to have it come pre-installed on all computers so that all users would have to do to activate it is to click on a button. The question is why computer manufacturers have not already added Linux to the computers they sell. After all, Linux is free and can easily be installed in computers by the manufacturer. They could then sell their computers for a hundred dollars cheaper with a fully functional operating system. This would also give their customers a choice. If they also want the Microsoft Windows operating system, they could pay an extra hundred dollars for it. But they would not have to buy Windows just to get the computer they want. Microsoft prevents this from happening by forcing manufacturers to sign restrictive licensing agreements.
Can’t we just turn off Secure Boot?
You can – sort of. You can switch from Secure Boot mode to legacy mode. But this is not the same as going back to the old BIOS Start Up program that starts all Windows XP and Windows 7 computers. You still have the UEFI program controlling whether your Windows 8 or 10 computer starts and the kill switch is still there. There are reports of folks switching to the UEFI Legacy mode only to have Microsoft switch the mode back to secure boot at the next Microsoft Update. And there is no way to close this backdoor to your computer because as we now know, Internet Explorer is tied into the Windows operating system. Finally, the UEFI code is ten times bigger than the BIOS code. What do you think that extra code is all about?
But isn’t UEFI a nice program created by a non-profit group?
Since UEFI with Secure Boot is capable of destroying the entire world economy, by giving Microsoft or hackers the ability to suddenly turn off all Windows computers, it is worth understanding how this nuclear weapon came into being. Microsoft claims to be an innocent bystander in the creation of Secure Boot.
But the facts tell otherwise. According to the UEFI official story, around the turn of the century, Intel wanted to update the BIOS Startup program to help their chips start up faster. So they used an “open source” operating system called BSD to create a new Startup program called EFI (Extensible Firmware Interface).
There are several things fishy about this official story. First, BSD stands for the Berkeley Software Distribution. It was created in the early 1990s at the University of California at Berkeley and is a free open source operating system. Fast forward to 2000. Intel wanted a better Startup program. Does it make any sense that a hardware company like Intel would try to write any software program – much less a program that controls the Startup of every computer? This is like Microsoft deciding that they were going to start making their own computer chips!
Besides, if Intel had really wanted a modern fast Startup program, they could have simply used the free open source Core Boot program that was being developed by the Linux community. In addition, EFI was not that fast or that smart. It was slower than Core Boot because it used the same complex driver process that BIOS used. At any rate, according to the official story, in 2005 Intel gave up on the EFI project and donated the EFI code to the UEFI Forum – a non-profit group that suddenly appeared like magic out of nowhere with the mission to create a modern Startup program. Naturally, Intel and Microsoft were on the Board of this new nonprofit organization.
|
Clue
|
The UEFI verification or signing mechanism is identical to the Microsoft Windows signing mechanism – a process that has already been attacked and compromised by the Flame virus. All the structure members of the UEFI signing mechanism start with the word WIN – wonder what WIN stands for??? |
In 2006, UEFI made version 1.0 which was not much different from EFI. But it was important enough for Bill Gates to give a Keynote Speech about UEFI:
|
Quote
|
“These are changes across the board, in terms of how hardware and software work together. If we think about boot, we're finally moving away from the old BIOS to this unified extensible firmware interface – UEFI - and that gives us new flexibility and capability.” |
UEFI version 1.0 in 2006 was not that different from BIOS. In particular, it did not include secure boot. Neither did UEFI version 2.1 which was released on January 7, 2007. So what the heck was Bill Gates talking about in his 2006 speech when he referred to a “new capability”? Could it be that Bill knew something completely different was in the works?
2008 UEFI Version 2.2 adds the Secure Boot Kill Switch
Beginning in 2008, just a few months after Microsoft joined the NSA PRISM program, strange things began to happen. The biggest change was with UEFI version 2.2. With UEFI version 2.2, the purpose began to change, the tools began to change and even the code began to change. Suddenly, instead of being merely an update to BIOS, UEFI became a nuclear weapon with the addition of Secure Boot. At the same time, the UEFI manual grew to be nearly 2,200 pages. Who could have done that? Pay no attention to that man behind the curtain (who also happens to be the richest man in the world).
Then UEFI version 2.3 was released in April 2011 – just 6 months before the “developer” release of Windows 8 at a Microsoft Developer conference in September 2011. The Secure Boot contracts and certificates were not released until 2012. This seemed to be an attempt to hide the real nature of Secure Boot until the release of Windows 8. In fact, it could have been that the chaos of the Windows 8 introduction was actually planned to hide the introduction of something much worse than Windows 8, namely the UEFI kill switch.
Evidence that Microsoft created UEFI and Secure Boot
Since its inception, Secure Boot has raised alarm bells among computer users because it gives Microsoft almost total control over our computers by preventing us from loading any program which is not approved by Microsoft. Members of the open source community have called this strange process “Restricted Boot”. Microsoft has denied having been involved in creating the UEFI and Secure Boot Twin monsters. However, there are four convincing facts which refute their claim.
First, UEFI file names use back slashes for separators.
Microsoft is the only company in the world which uses backslashes in their file names. All other programmers use forward slashes.
|
Example
|
Example of Unix Forward Slash File Naming: The same file with Microsoft Backward Slash File Naming: C:\Users\davidspring\Documents\file.txt |
The open source community uses forward slashes to define file names. This is because Linux and BSD are both based on Unix and Unix uses Forward slashes for file names and backward slashes for the “escape” function. But there is one company in the world that is arrogant enough to write their own computer languages which uses backward slashes for file names. The company who uses backward slashes for file names is Microsoft. And the UEFI file names? Well, they all now use backward slashes. This is very odd because the “official” story claims that UEFI was based on BSD and BSD uses forward slashes!
Security experts are mad at Microsoft for insisting on programming with backward slashes as it creates a huge security risk. This is because all URLs use forward slashes – including web pages which protect sensitive business data. One example of this danger occurred in 2004. Active Server Pages (ASP) is a Microsoft programming language. In 2004, it was discovered that ASP has a huge security flaw associated with back slashed file names.
|
Quote
|
By using a backslash instead of a forward slash you could access secure ASP.NET resources that normally required authentication. So, if accessing www.example.net/secure/private.aspx is supposed to be a protected web page requiring authentication, anyone who wants to could access the file by entering the URL as www.example.net/secure\private.aspx. Even if you set permissions to block anonymous users, ASP.NET still allowed access. |
It is clear that in writing UEFI with back slashed file names, Microsoft has not learned its lesson about what a dangerous practice this is. They have now tied insecure back slashed file names to the most dangerous computer weapon ever produced. This is why I maintain that UEFI and Secure Boot should be avoided at all costs. There is nothing safe about either of these “features.” Computer manufacturers should replace UEFI and Secure Boot with Core Boot – which of course uses the standard and secure forward slash file names. In any case, the fact that UEFI has been changed to back slashed file names is clear evidence that the two latest versions of UEFI were actually written by Microsoft programmers. It is also clear that Secure Boot was written by Microsoft and added to UEFI at the very last minute. It is also clear that Secure Boot was written specifically for Windows 8. Thus, Microsoft’s finger prints are all over the crime scene. And make no doubt about it – UEFI with Secure Boot is a crime against humanity. It doesn’t take Sherlock Holmes to figure out where UEFI really came from or what the real purpose of Windows 8 is.
Second, the UEFI security signing mechanism is identical to the Microsoft Windows security signing. I do not mean similar. I mean IDENTICAL. Many sections of UEFI code even begins with the word “win.”
Third, the versions of UEFI since Microsoft joined this project are completely different from the version of UEFI which existed before Microsoft joined the project. As just one example, the original versions of UEFI did not have secure boot and made no mention of anything like secure boot in their plans.
Fourth, before Microsoft joined the project, the source code for EFI was open and publicly available. After Microsoft joined, a cloak of secrecy covered the project. No one knows for sure exactly what is in the bloated UEFI code – which is ten times bigger than either the BIOS code or the Core Boot code.
The Secure Boot Kill Switch is different from the Windows “Apps” Kill Switch that has been discussed in the media. A Kill Switch is a program which can remotely delete software and edit code without the user’s permission. There are at least two known Kill Switches on the Windows operating system – these are the Secure Boot Kill Switch and the Apps Kill Switch. There has been some confusion in the media about which Microsoft Kill Switch is the most dangerous. I want to make it clear that I have no problem with the new Windows Apps Kill Switch which is capable of destroying any programs you purchase through the Microsoft Apps Store. Anyone who buys an app through the Microsoft Apps store deserves to have their programs nuked without warning.
The Apps Kill Switch does not kill your entire computer and does not prevent you from installing an alternate operating system. In fact, all it takes is a comparison of the silly programs at the Microsoft Apps store to the 40,000 free programs at the Linux store to get people rushing out to download Linux.
Microsoft claims that that Secure Boot is needed for safety reasons. However, if Microsoft was even remotely concerned about safety, they would not leave the back door open to all Microsoft operating systems. Microsoft had already created problems for “dual booting” a Linux operating system with Windows 7. We will discuss these problems further in the section on dual booting. But it is apparent that Microsoft is doing everything in its power to maintain its monopoly.
Microsoft Windows has since 1997 had known malicious features... features to spy on the user and restrict what the user can do, which are in fact digital handcuffs, and it has known back door security problems whereby Microsoft can change anything about your program remotely. However, these attempts at censorship may backfire for Microsoft. As users become more aware that Microsoft is trying to limit their ability to use open source operating systems this may actually increase the interest in using them. Users will realize that the way to take back control over their future is to first take back control of their computer.
Design Flaws of UEFI
First UEFI was and developed in secrecy. As security experts have often pointed out, secrecy means a lack of feedback and is therefore a model for failure. Incredibly, there is no way to know what is in the UEFI program or what kinds of bugs have been discovered because all members of the UEFI forum must sign an oath of secrecy. Even UEFI documentation is kept under secure files requiring UEFI passwords to access. This is the exact opposite of how the open source community works – where everyone knows about all bug reports and everyone works together and shares ideas and solutions to fix the bugs.
Second, UEFI is an enormous program with over 7000 files and more than 100 MB of code. There is safety in simplicity. More code simply leads to more ways to attack the system.
Third, UEFI has 'call home” feedback loops which were not present on BIOS and are not present on Core Boot. This is perhaps the worst shortcoming of UEFI. BIOS and Core Boot are almost completely separate from the operating system. Therefore attacks on the operating system rarely if ever affect the start up program. However, because secure boot will not work without a “call home” open back door, UEFI is the first start up program to ever have a call home feedback loop. This feedback loop would make it possible for an attacker who gains access to the Authorized Certificates to rewrite the code on the start up chip much more easily than could be done with either BIOS or Core Boot.
Fourth, the Secure Boot Certificate method has already been shown to be open to successful attack. This is how the Stuxnet and Flame viruses both attacked the Windows operating system.
Security expert, Bruce Schneier calls the certificate system “completely broken.”
|
Quote
|
The problem for all of us, naturally, is if the certificate system was hacked, allowing the bad guys to forge certificates. (This has, of course, happened before.) Are we finally ready to accept that the certificate system is completely broken?
|
Fifth, UEFI uses Microsoft programming languages which use backward slashes for file names. Backward slashes have previously led to easy attacks to the Windows operating system – this same attacks could go directly to the Start up chip due to the “call home” open back doors in UEFI.
Sixth: Secure boot is not secure
Secure boot uses a combination of keys to prevent you from downloading any program Microsoft feels they do not like. The problem is that some of the keys are public and the rest have been hacked in the past – and will be hacked again in the future. So the only one blocked from installing programs to your computer by secure boot is you. Microsoft has left the back door to your computer open since 1997. With Windows 8, they have now also left the front door to your computer open. Secure Boot opens up the Startup program to attack because it uses the same top down easily copied digital image system the Microsoft Windows uses to protect its open back door. The name Secure Boot lulls users into a false sense of security that their computer is secure when it is not.
Seventh: Secure Boot is very difficult for many users to disable
Supposedly we have the option of turning off secure boot. The problem is that there are four major “families” of secure boot and every manufacturer has a different implementation of secure boot. Without any consistency, this means that there are literally dozens of different kinds of secure boot systems.
Eighth: Even if you disable secure boot, UEFI still has huge problems
Secure boot is just the tip of the iceberg in terms of all the problems of UEFI. UEFI specifications are a secret. But what is known about them is that they are thousands of pages long. Subtracting the driver code, the size of UEFI is actually larger than the size of the entire Linux Kernel. What is in all of these thousands of files and lines of UEFI code? Many of the files in UEFI begin with a “win” prefix – meaning that they were written by Microsoft for Microsoft and Microsoft does not want to let us know what is in this code. UEFI is also written with Microsoft back slashes as path separators – just like Microsoft file paths– making it easier for hackers to attack it. Because UEFI is new it is certain to have many bugs and will have unpredictable reactions with many other programs. In particular, most of the new code affects boot loaders such as GRUB 2 and the Windows Boot Manager.
Ninth: There is a safer free option to UEFI called Core Boot
If either Microsoft or computer manufacturers really cared about safety, they would have installed the Core Boot Start up program. It is faster and safer than UEFI. By placing the passwords and control of the computer in the hands of the actual owner (you), there is no set of keys to be copied. A maker of processors, called AMD, now fully supports Core Boot. So manufacturers do have an easy option. Our hope is that if enough people return their Windows 8 computers and demand a computer with Core Boot, we will eventually be able to put this Windows 8/UEFI/Secure Boot Nightmare behind us.
Tenth: Claims that there are advantages to UEFI are false
We are currently being subjected to a wave of propaganda trying to convince us that UEFI has some kind of benefit. For example, they claim that UEFI can handle partitions bigger than 2 Terabytes. Well, so can Core Boot. Even the old BIOS can as long as they are divided between partitions. If you have more than two terabytes of data, you should not be putting so much data on a single hard drive anyway. You should use a second hard drive if only for safety reasons. You will also hear that UEFI allows you to have a much larger number of partitions. This is also not true. Core Boot has the same partitioning ability as UEFI and even the old BIOS system will let you have as many partitions as you want as long as you use the fourth partition to create an extended partition.
You will also be told that Secure Boot protects against Root Kit infections. It does not. Anyone capable of creating a root kit attack is also capable of creating fake keys similar to the process used by the Flame virus. So do not be fooled. The only purpose of UEFI is to maintain and expand the Microsoft monopoly. If you want your system to be safe and under your control, then install and use Linux. If you really want security, then you need to get a computer with Core Boot.
Eleventh: You Can Not Get Rid of UEFI
Unfortunately, it is quite difficult to get rid of UEFI – or replace UEFI with Core Boot because UEFI is not on your hard drive. The only way you can get rid of UEFI is to return the computer to the store where you bought it, demand a refund and demand the option to buy a computer with Core Boot on it. It is also not likely that Windows 8 will work on anything other than UEFI because UEFI and Windows 8 were basically made for each other.
UEFI was successfully attacked before it was even released to the public
In September 2012, security researchers discovered security shortcomings in Windows 8 (aka UEFI) that create a means to infect the upcoming operating system with rootkit malware. Italian security consultants ITSEC discovered the security hole following an analysis of the Unified Extensible Firmware Interface (UEFI).
|
Quote
|
Mark Giuliani, the Director of ITSEC told El Reg. “Writing a rootkit couldn't be an easier task for virus writers with the UEFI framework available, much easier than before with BIOS when they needed to code in pure assembly.
|
Linus Torvalds, the founder of the Linux project is also not impressed with UEFI.
|
Quote
|
“The real problem, I feel, is that clever hackers will bypass the whole (UEFI) key issue either by getting a key of their own (how many of those private keys have stayed really private again? Oh, that’s right, pretty much none of them) or they’ll just take advantage of security bugs in signed software to bypass it without a key at all.” |
Why UEFI is a Trojan Horse
One of the most common tricks used by hackers to gain access to your computer is what they call a Trojan Horse attack. The attack is based on fooling you to download a program which you really should not download. This is the equivalent of inviting thieves to enter your home. The thieves then change the locks on your doors while you are not looking and then come back later to steal all of your data. The first Trojan attack Microsoft initiated was by inserting Windows Internet Explorer and DLL files (Dynamically Linked Libraries) into the Windows operating system in 1998 with the introduction of Windows 98. We have all seen how many problems this open back door has created for our computers. But the UEFI scam is much worse – because it is taking a start program with no real security problems (BIOS) and replacing it with a start program which is literally loaded with security problems (UEFI) and then trying to convince us that UEFI will somehow improve the security on our computers.
Secure Boot adds a new verb to the English Language: Brick
Thanks to Secure Boot, a new verb has been added to the English Language. It is brick – as in “Secure Boot just bricked my computer.” The verb comes from the noun “brick” which is a heavy useless block. Sadly, if you try to do anything Secure Boot does not like, it might shut down your computer and prevent it from turning on again – turning your computer into a heavy useless block aka a brick. There are numerous reports of UEFI and Secure Boot bricking computers.
Personal Computer User Freedom Matrix
Richard Stallman has outlined four essential freedoms. The following table shows how each of the three Startup programs meet these four freedoms.
|
Four Software Freedoms |
CoreBoot |
UEFI |
BIOS |
|---|---|---|---|
|
The freedom to run the program for any purpose. |
Yes |
No |
Yes |
|
The freedom to study how the program works and change it so it does what you want. |
Yes |
No |
No |
|
The freedom to distribute copies. |
Yes |
No |
No |
|
The freedom to distribute copies of your modified version of the program to friends. |
Yes |
No |
No |
Microsoft's solution to the bricked computer problem is to buy a new official key from Microsoft.

There are many reports that some computer manufacturers simply turn off Linux operating systems. These include Lenovo, Toshiba and Samsung. But even turning off Secure Boot and Microsoft Update is just a temporary fix – since Microsoft still retains control over every computer with Windows/UEFI/Secure Boot installed on it. The only real solution is to not buy a computer with Windows 8 installed on it and demand that computer manufacturers use Core Boot instead of UEFI/Secure Boot. Even though Windows is the greatest attack on our freedom since the East India Corporation came up with the Stamp Act – a move that started the American Revolution – do not expect much help from our government.
The best thing you can do to take back control of your computer is finish reading this book and learn how to install and use Linux and Libre Office on your own computer. We will review the best available solutions to all of these Windows problems in later chapters.
The Secure Boot Trap is challenged in Court
On March 26, 2013, an 8,000 member group in Spain called Hispalinux filed a complaint against Microsoft protesting that the new “Secure Boot” feature in Windows 8 was simply another attempt to maintain the Microsoft Monopoly by making it more difficult for folks to add Linux to their computers.
|
Quote
|
“UEFI Secure Boot with Microsoft keys is “designed to block non-Microsoft software. This is not a side effect. It is its main purpose and is spelled out as such in Microsoft's own documentation... One of the options allowed by UEFI is the digital signature of drivers and applications, permitting complete control over the start-up system. Microsoft, as the sole owner of the private key, which matches up with the public key held in the memory of computers running Windows 8, is the only party that can authorize (sign) the software components in UEFI, the only party that can sign the boot of the operating system, and the only party that can sign the communications between the operating system and UEFI. To attain this goal, Microsoft has to use all its influence and power in the market to force computer and component manufacturers to accept its monopoly in the key generation system.” Hispalinux Lead Attorney Jose Lancho |
In June 2013, the American Civil Liberties Union filed a lawsuit against the NSA for violations of the 1st and 4th Amendments to the US Constitution. Hopefully, this book will help more people understand the connection between Microsoft and the NSA and help them take steps to free their computers from this attack on their privacy.
2016 Microsoft Hands Golden Key over to Hackers
As if the insanity of handing the keys to our computers over to Microsoft was not bad enough, in June 2016, two computer security researchers discovered that Microsoft was doing some rather reckless things with these Golden Keys. Microsoft developers wanted to make changes to certain devices without going through the hassle of getting authorized keys to Secure Boot. So they developed a secret “super policy” for bypassing Secure Boot completely. Had this Golden Key “super policy” been discovered by hackers it would have given them unlimited access to nearly every computer in the world. The only good news to this story is that this backdoor nuclear weapon was discovered by “Good Guy” researchers before it was discovered by Bad Guy hackers. https://www.infoworld.com/article/3106079/security/secure-boot-proves-insecurity-of-backdoors.html
After the researchers notified Microsoft of the issue, the company released a security patch MS16-094 in July 2016. This “golden key” super policy is now blocked from loading on computers with the July patch installed. However, the July patch is not a complete fix -- it's at most a small roadblock. The issue remains only partially addressed, and what's worse, it is believed that it is impossible for Microsoft to fully revoke the leaked Golden Key Super policy.

Because of the implications of this Golden Key Backdoor being released to the wild, the two researchers wrote a letter to the FBI explaining why the entire concept of having super keys to all computers was a bad idea:
“Microsoft implemented a 'secure golden key' system. And the golden keys got released by Microsoft's own stupidity. Now, what happens if you tell everyone to make a 'secure golden key' system? This is a perfect real-world example about why your idea of backdooring cryptosystems with a 'golden key' is very bad!”
The first lesson we should learn from the 2016 Golden Key incident is that keys and secrets will eventually get leaked or stolen. The second lesson is that a fix is not always possible.
Extreme Tech reviewed this incident and concluded: “One small leak is all it takes to let the cat out of the bag — and thanks to the Internet, there’s no way to prevent such information from spreading. Security that depend on human perfection to lock down content will always fail, because humans aren’t perfect. Episodes like this will never stop happening — which means we need to stop looking towards hypothetical golden keys as solutions to real-world problems.”
If we really want to protect our computers, we need to only use computers that do not use UEFI, Secure Boot and Golden Keys in the first place.
Lack of Choice is a Lack of Freedom
The worst part of the UEFI Kill Switch is that we are not even being given a choice of whether to accept UEFI or not. This is because nearly all computers are being switched over to the UEFI start program. As of today, the only computers that use Coreboot instead of UEFI are Google Chromebooks and the Librem 15 by Purism. Microsoft is once again using its monopoly power to force all other computer manufacturers to use UEFI. Even Apple computers only come with UEFI installed. So today, we are all being forced to pay for an extremely dangerous UEFI system.
If nearly all computers now have UEFI, what computer should I buy?
You currently have only five options:
Option #1: Keep your current computer.
Linux works really well as a direct replacement for Windows XP. You can even run Windows programs with Linux using a process we will describe in a later chapter.
Option #2: Repair any dead computers you have.
It is likely that the old computer in your closet still works or can be made to work like new just by replacing the hard drive chip. I have done this myself and it is not hard. But if you are not thrilled about opening your computer, then take it to a repair store. You can likely get a new hard drive installed for less than $200.
Option #3: Buy a used Windows Windows 7 computer???
Actually, this is no longer a real option. Effective with Windows 10, Microsoft has been forcing all Windows 7 computers to “upgrade” to Windows 10. They also seem to have a way to backport UEFI onto all Windows 7 computers. So do not waste your time or money on any Windows computer.
Option #4: If you want to buy a new computer, and you are on a limited budget, buy a Google Chrome Book
All Chromebooks comes with Coreboot and a stripped down Linux operating system called Chrome. It takes a couple hours to switch this to a full Linux Mint system – a process we describe in a later chapter.
Option #5: Buy a laptop with CoreBoot and Linux Preinstalled
There is only one laptop with a 15 ½ inch screen, Coreboot and a full Linux operating system pre-installed. It is the Purism Librem 15 which costs $1600 but is currently the best laptop on the market at any price. Here is the link:
https://puri.sm/products/librem-15/
|
Caution
|
There are several computer manufacturers, such as Dell and System 76 which install Linux on new computers. However, only Purism has seen the wisdom of installing Core Boot on computers. The rest use UEFI. Since UEFI is a much worse problem than Windows, you should avoid any computer that uses UEFI – even if it comes with Linux. It will not be secure! |
Everything to gain and nothing to lose
Even if you want to continue to use Windows, it is important to understand that you can use open source tools like Libre Office to work with, save and send Word documents. And you can use the Linux operating system to run Windows programs. In fact, nearly anything that you currently do using expensive Microsoft programs you can do better, easier and safer using free open source tools. We will show you how to safely install and use open source tools so you can test them side by side with whatever you are currently using -and decide for yourself whether you want to jump permanently to open source. Open source tools put you in control of your computer and your life. No more patches, no more upgrades, no more hassles!
In other words, you have nothing to lose and everything to gain by learning more about the many benefits of open source tools. Once you give it a try, you will probably wonder why you waited so long. That is how we all feel the first time we are exposed to open source programs. Many people and organizations have seen the writing on the wall and already made the move from Windows to Linux.

What’s Next?
Now that we have a better understanding of the dangers of the UEFI startup program, in the next chapter we will look at the many different flavors of Linux.



