Ransomware is a type of malware whereby a victim is tricked into downloading a malicious program on their Windows computer which encrypts most of their files - and then demands a ransom payment in order to get the key to unlock and restore the files. In the past two years, more than one million Windows computers were subjected to ransomware attacks, costing their victims more than ten billion dollars. These attacks have been mainly from the WannaCry and NotPetya ransomware. However, in the past year, ransomware has evolved into a new and much more powerful strain, called Ryuk. Ryuk not only encrypts or scrambles all of your important files, it silently spreads to all of the computers in your network and can spend up to a year stealing all of your passwords and infecting all of your backup files before locking up all of the computers in your network. Ryuk carefully chooses its victims based on their ability to pay. Ryuk prefers cities, colleges and school districts. Ryuk charged a city in Florida $600,000 to get their computers back. More recently a college in New York was asked to pay a ransom of $1.4 million to get their computers back. Local government agencies, schools and colleges have been forced to spend millions of additional dollars trying to rebuild their computer networks after being attacked by Ryuk. Worse of all, the advice being given to Ryuk victims thus far by so-called “computer security experts” has been completely wrong.
In this report, we will expose the hidden dangers of Ryuk ransomware. We begin by briefly reviewing the connection between these new forms of ransomware and NSA cyber weapons. We then outline the history of Ryuk and its companion cyber weapons called Emotet, Trickbot and Xbot which work together in a carefully planned attack. Then we discuss the new dangers of Mega Cortex and explain how to truly recover from and protect yourself from future attacks. Finally, we explain how schools and colleges that are victims of these ransomware attacks can fight back and help us move towards a world that eliminates these cyber weapons altogether. If you know someone who works for a school, college or local government that uses a Windows computer network, please share this important article with them.
This report is divided into the following 10 sections:
I. Introduction to Ryuk Ransomware
II. History of NSA Based Cyber Weapons
III. History of Emotet
IV. History of Trickbot
V. History of Xbot
VI. History of Ryuk
VII. How Emotet, Trickbot, Ryuk and Xbot Work
VIII. Mega Cortex… Ransomware with a Kill Switch
IX. How to Recover & Protect Yourself from Future Attacks
X. How Schools & Colleges Can Stop Future Cyber Attacks
Here is a diagram of how Ryuk Ransomware works
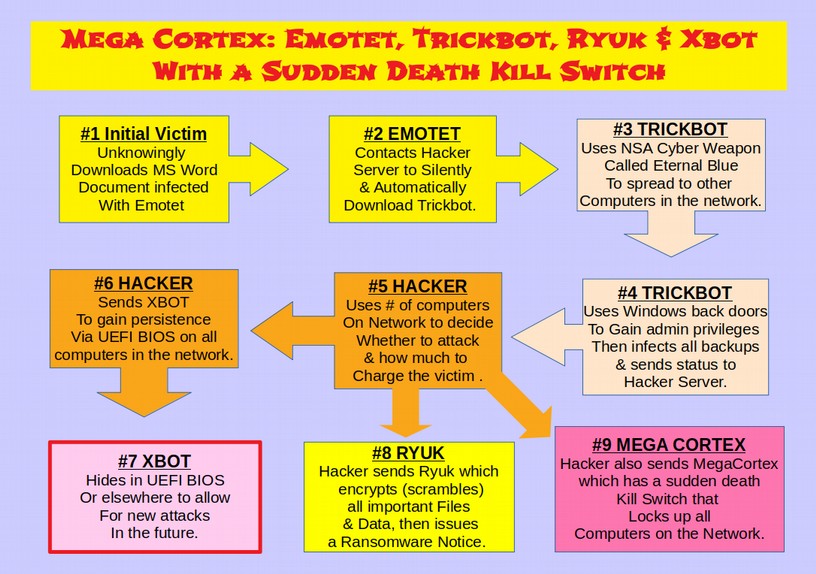
I. Introduction to Ryuk Ransomware
Here is what the Ryuk Ransomware Ransom Note looks like:
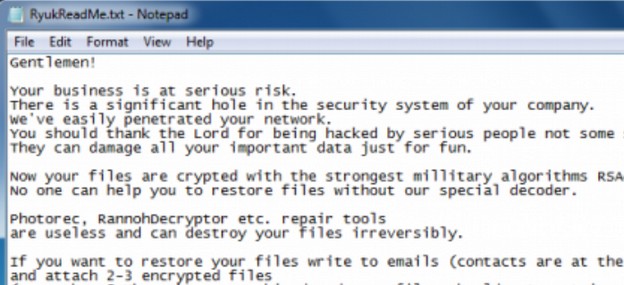
In 2018, there were at least 53 documented Ransomware attacks against local government computer networks. These include attacks against school districts and colleges. In March 2018, Atlanta, Georgia suffered a major ransomware attack. Several cities in Florida also suffered ransomware attacks – paying more than one million dollars to get their computers back. On July 24, 2018, a ransomware attack in Anchorage Alaska resulted in 120 servers and 500 work stations being infected. This included both Windows 7 and Windows 10 computers. Their email system was completely wiped out. The initial infection occurred on May 3, 2018 meaning that the ransomware was dormant for over two months.
In the first quarter of 2019, the frequency of these attacks increased to nearly double the rate in 2018. In March, Jackson County Georgia and Albany NY were victims of ransomware attacks. In April, Augusta Maine and the Cleveland International Airport suffered ransomware attacks. In May, Baltimore suffered a massive ransomware attack. 10,000 government computers were frozen and unusable.
According to a 2018 report, 20% of all K-12 public schools and 30% of all higher education institutions suffered a data breach loss or ransomware attack in the previous school year. Higher education institutions were the victims of 539 attacks that compromised 13 million student records.
https://media.erepublic.com/document/CDE18_Special_Report_K-20_Cyber_V.pdf
A May 2019 study found that more than 450,000 public facing servers in the US run by schools, colleges and local governments are at risk of a ransomware attack.
Sadly, if your organization has been hit by Ryuk Ransomware, it is likely that your troubles are just getting started. This is because Ryuk is not being distributed as an isolated ransomware. Instead, Ryuk is the visible face of a very ugly mega threat that also includes three very persistent programs called Emotet, Trickbot and Xbot. More recently, hackers evolved a new version of ransomware called Mega Cortex that includes not only Ryuk but also a sudden death Kill Switch. Mega Cortex charges victims millions of dollars to get their computers back and has the ability to permanently kill all computers on the network in less than one second if the victim fails to pay.
May 2019: Hackers unleash Mega Cortex – Ryuk Ransomware with a Kill Switch
These ransomware weapons evolved from several of the most harmful cyber weapons ever created by the NSA – including a hacking tool called Eternal Blue – that escaped into the wild in 2015.
This is the dirty secret our government and the main stream media do not want you to know about. Ryuk, Trickbot. Emotet, Xbot and Mega Cortex are not the creations of Russian hackers, Iranian hackers, North Korean hackers or Chinese hackers. Instead, they are the latest evolution of cyber weapons that were paid for with your hard earned tax payer dollars. They can be traced back to NSA cyber weapons created as far back as 2007. If you computers have been hacked by Ryuk ransomware, things are about to get much worse.
II. History of NSA Based Cyber Weapons
In the early 1990’s, I started one of the world’s first online stores in Bellevue Washington – one year before the start of Amazon. Since then, I have helped hundreds of business owners build secure business websites and overcome hacking attacks. This experience has made me acutely aware for the need to protect computer networks and websites from hackers.
About 10 years ago, I began researching a new wave of cyber weapons called Stuxnet and Flame that were causing severe harm to Windows computers. This new generation of cyber weapons, which we now know were created by the NSA beginning in 2007, were able to persist on Windows computers even after replacing the operating system and even after replacing the hard drive of the computer.
This research led to a book I published in September 2013 called Free Yourself from Microsoft and the NSA – based in part on the revelations of Edward Snowden about these NSA hacking tools – but based primarily on my own research regarding security vulnerabilities of the Windows operating system. You can download and read a free copy of this book at this website. https://freeyourselffrommicrosoftandthensa.org/
In that book, I predicted it was only a matter of time until hackers got copies of these NSA cyber weapons and used them to hack Windows computers all over the world. That day arrived on July 5, 2015 when a group called Hacking Team was exposed for selling NSA hacking tools to repressive governments around the world. Hacking Team itself was hacked and more than 400 GB of NSA based hacking tools was released over the Internet.
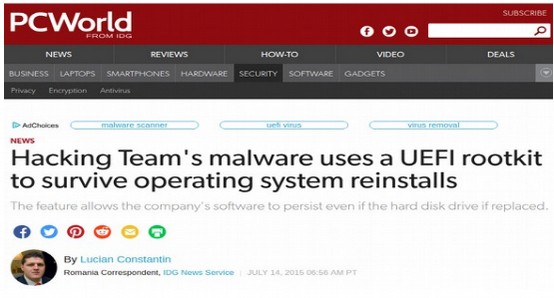
On August 13, 2016, a group called Shadow Brokers announced that they had hundreds of NSA hacking tools that they were selling on the Black Market to the highest bidder. On April 14, 2017, Shadow Brokers released almost all of these NSA hacking tools, including Eternal Blue, to the public.

The Shadow Brokers release was barely one month after another bombshell release of NSA cyber weapons by Wikileaks in a report called Vault 7 which was released to the public on March 7, 2017. The most shocking part of the Wikileaks report was an NSA tool called the Marble Framework which was a tool used to fool victims into thinking they had been attacked by Russian or Chinese hackers when in fact they had been hacked by NSA hackers.

On May 12, 2017, Wanna Cry Ransomware began attacking hundreds of thousands of Windows computer networks around the world causing about $6 billion in damage. Predictably, Wanna Cry used Eternal Blue and other NSA hacking tools to carry out its attack, spread rapidly from computer to computer and gain control over entire computer networks.
In June, 2017, a new version of NSA based ransomware called Not Petya began attacking computer networks. Not Petya caused more than $10 billion in damages. The attack spread in part using a remote controlled software update from an accounting program – indicating that the server issuing the update had been compromised. NotPetya used the same Eternal Blue and other NSA cyber weapons that had been used by Wanna Cry a month earlier. I wrote a 60 page report about these ransomware attacks and their relationship to NSA cyber weapons in April 2019. You can read this article online by going to the following link: https://learnlinuxandlibreoffice.org/news/the-fight-for-a-secure-linux-bios
You can also view a video presentation of this article at the following link: https://www.youtube.com/watch?v=mEPcRFvvekY
Both WannaCry and Not Petya Ransomware can best be thought of as early versions of Ryuk (aka Emotet - Trickbot – Ryuk & Xbot) and Mega Cortex (Ryuk with a Kill Switch) as all of these hacking tools use Eternal Blue and several other NSA cyber weapons.
The chief difference is that Ryuk and Mega Cortex also targets backup systems used to restore computers after they have been hacked. Both Ryuk and Mega Cortex also appear to have the ability to “persist” on infected networks even after the operating system and hard drive have been cleaned or replaced.
This makes it much more difficult to recover from these new attacks. We will therefore briefly outline the history of Emotet, Trick Bot, Ryuk & Xbot before reviewing how they work and the ongoing threat they pose to Windows computers.
III. History of Emotet
Emotet started out in 2014 as a simple email scamming and information-stealing tool that was initially used to gather sensitive financial information from infected Windows computers and forward this information to hackers who would then empty out the victim’s bank account. The first version of Emotet used malicious Javascript files attached to emails to infect Windows computers. Over time, the links and attachments became Word documents, Excel spreadsheets, PDF documents and even images – often supposedly from other people known by the victim (who had also been hacked without knowing it).
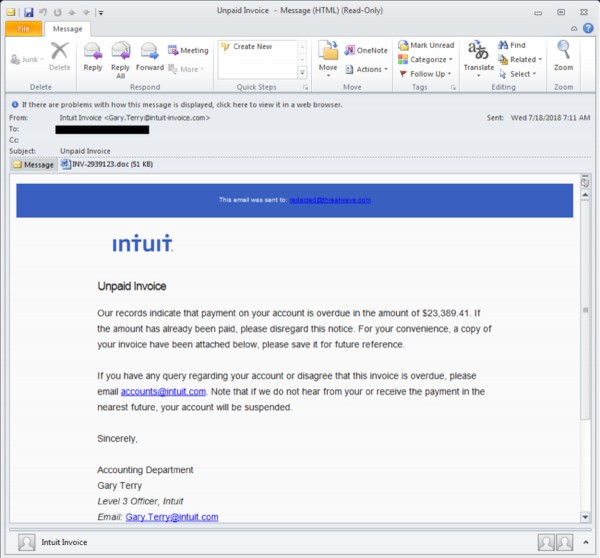
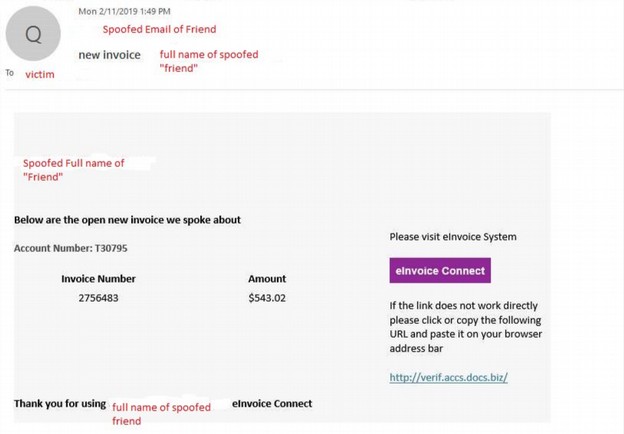
Here is an example of what appears to be an unpaid invoice, but it really a trick to convince the victim to download Emotet.
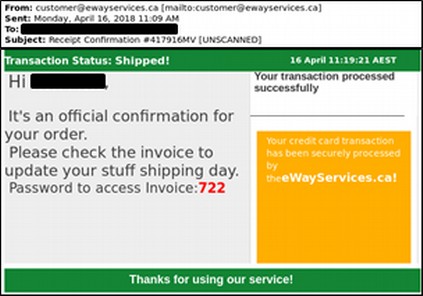
Here is another example of an Emotet spam email:
The link could have also been to someone’s resume or a link to a Youtube video or even a picture of a lost cat. Clicking on any of these links or downloading any of these documents or images from a Windows computer would lead to a download of Emotet.
One of the first goals of Emotet is to find the victim’s email address book. Emotet uses several programs to access your contacts. These programs include a tool called Outlook scrapper to gather all of the names and email addresses of everyone in your Microsoft Outlook email account. The second tool is a password recovery tool that captures all of the passwords you have stored in your browser history. This tool accesses several different browsers including Internet Explorer, Firefox, Google Chrome, Safari and Opera. Remember this the next time your browser asks you if you want it to remember your passwords. The correct answer should be no.
Once Emotet has all of your email contacts and passwords for your email accounts, it then start sending out similar scam emails to every contact in your email address book. The emails appear as though they’re coming from a known sender (you). Recipients of email from a known contact are more likely to open the attachment and become the next victim.
Newer versions of Emotet have evolved to evade most spam filters and use very realistic graphics to fool victims into thinking they are getting an email from a trusted friend or co-worker or major corporation such as Google or UPS or Amazon.
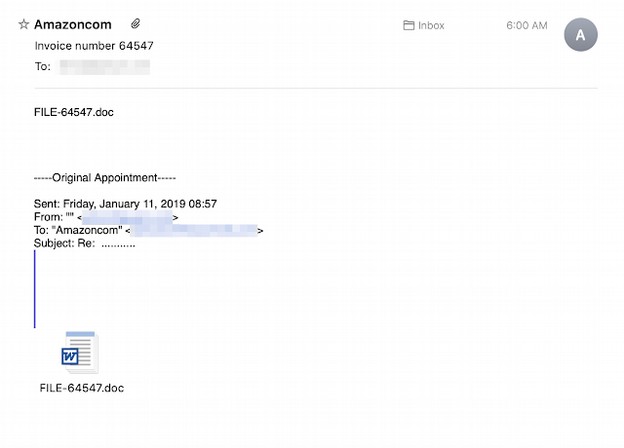
Here is another Emotet email. Does this look like spam to you?
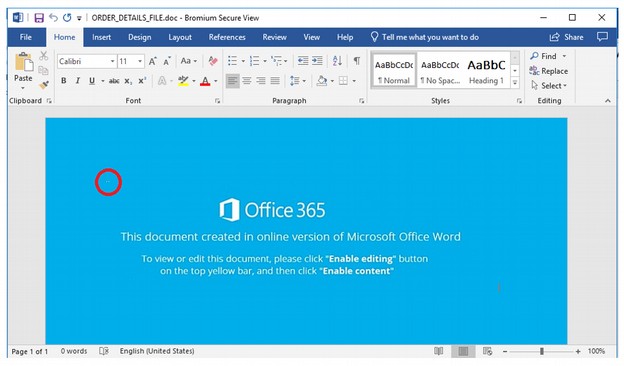
In the top left corner of the document is a tiny text box (Highlighted by a red circle in the image), so small it almost looks like a dead pixel on your screen. This edit box is where the changes for each malware infection are made. Can you see the small white dot? Neither can I.
Here is another Emotet example:
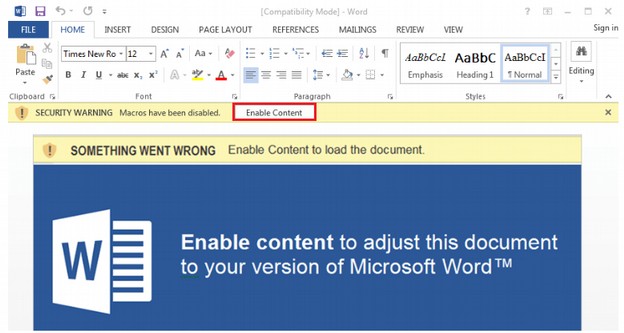
Emotet also uses URL spoofing to fool people to think they are linking to a major website rather than a fake website created to look like a major website.
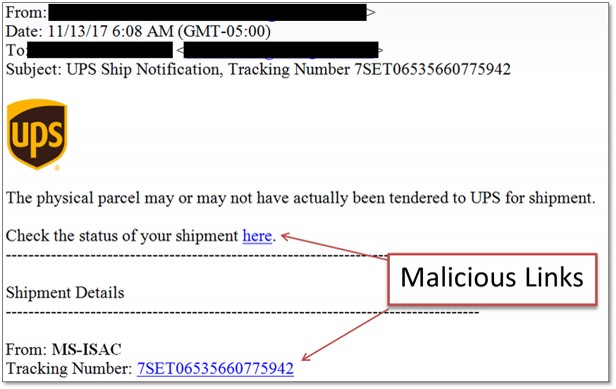
Here are examples of malicious links:
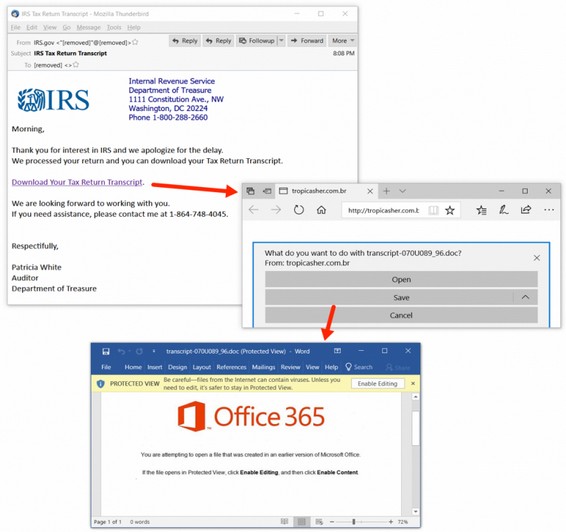
Another trick of Emotet is to claim they are the US Internal Revenue Service sending you a notice. Here are just some of their IRS notices:
From: Internal Revenue Service <[spoofed email address]>
-
From: Internal Revenue Service Online <[spoofed email address]>
-
From: IRS <
This email address is being protected from spambots. You need JavaScript enabled to view it. ; <[spoofed email address]>
-
Subject: IRS Tax Return Transcript
-
Subject: IRS Verification of Non-filing Letter
-
Subject: IRS Wage and Income Transcript
-
Subject: Payroll Tax Payment
Here is an example of an Emotet malicious email using an official IRS logo:
The Office 365 log in hack. Instead of logging into Office 365, your employees are logging into Emotet and Trickbot!
In an effort to increase their profits, a few years ago, Microsoft switched from a model where folks would pay a few hundred dollars to download a permanent copy of Office to a model where folks would rent an online copy of Office, called Office 365, which costs businesses $12.50 per month or $150 per year per user. So if a company has 100 employees, they could be paying $15,000 per year just to use Office 365.
Over time, Microsoft eliminated the ability of businesses to buy the stand alone version of MS Office. This forced the employees of all businesses to get used to logging into the online version of MS Office.
Paying thousands of dollars per year for Office 365 seems crazy when companies could be using a more secure open source tool called Libre Office to process all of their Microsoft documents for free. But the real danger in using Office 365 online is that employees get conditioned into logging into an Office 365 account in order to view and edit Microsoft documents. This makes them easy targets for Emotet email campaigns designed to trick them into clicking on a malicious link. Here is a quote from an article describing this problem.
“Office 365 phishing emails are one of the top threats attempting to be delivered to NJ State employee inboxes. These emails are often used to steal Office 365 user credentials by convincing a target to click on a link or open an attachment that directs them to a fraudulent Office 365 login page.
The “Update your Web Browser” Trick
Hackers have created sites that delivers an alert claiming the user’s browser – either Chrome or Firefox –needs to be updated. If the “Update” button is clicked, an executable will be downloaded that installs the Trickbot banking trojan. Trickbot is a sophisticated trojan with many capabilities that include stealing saved login credentials, browsing history, and form autofill data. Trickbot has been implicated in many recent cyber incidents, most notably infecting networks prior to the installation of the Ryuk ransomware.”
The latest campaign is targeting Windows 10 users and implementing a highly detailed and convincing, but fake nonetheless, Office 365 page to prompt for browser updates that install the Trojan itself.” Here is the Trickbot image warning you that your need to update Firefox:
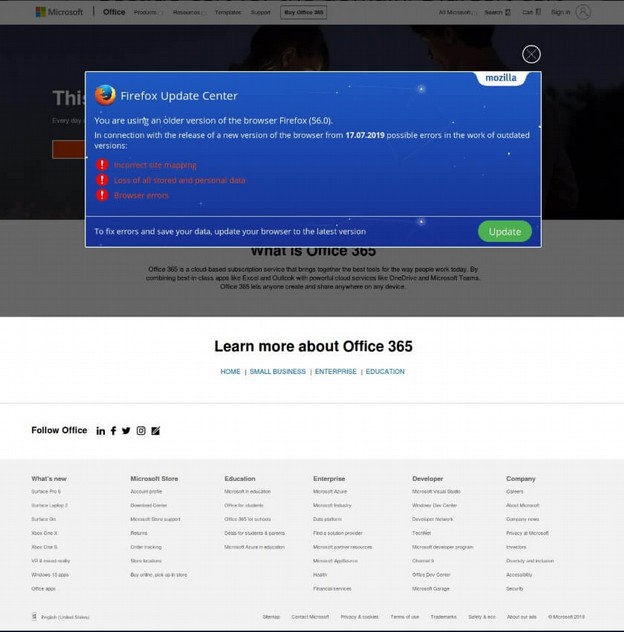
Clicking on some of the links takes you to a valid Microsoft 365 website. But clicking on the Firefox Update link installs the malware.
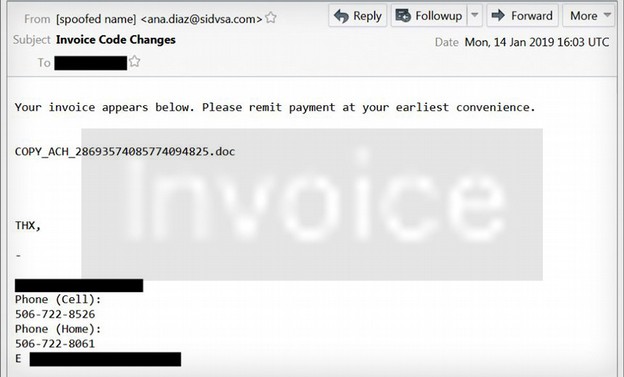
Here is another example of Emotet:
Here is another example of Emotet:
In February 2018, an Emotet attack on the city of Allentown PA cost more than one million dollars to clean up. Emotet had the email accounts and passwords of many city employees.
Employees were blamed for being “click happy,” But in fact, Emotet has evolved into a tool that can fool almost anyone. In this case, an employee received an email from someone claiming to be another employee.
According to one study, Emotet was downloaded by more than two million computers just in 2018.
A May 2019 report stated that Emotet
“accounts for almost two-thirds of all malware payloads delivered by email - with malicious URLs favored far more than weaponised attachments…the number of threats delivered my malicious URLs outnumbers those delivered by malicious attachments by five to one.”
Even clicking on a READ MORE link can cause an infection if you are using a Windows computer. Therefore clicking on any link or downloading any file from any Windows computer could cause you to become a victim of Emotet.
As for where these Emotet attacks are coming from, the overwhelming majority of attacks are coming from servers located in the US. And the overwhelming majority of victims are also in the US.
The real problem is not click happy employees. It is using Windows computers that are so insecure that all it takes is a single mistake by one employee to bring down a network of a thousand or more computers. If you use Windows computers, there is no “training” that can protect your employees or your organization from this scamming operation.
Emotet comes with Windows based Dynamically Linked Libraries – more commonly called DLL files - which it uses to contact Command and Control servers to let hackers know they have a new victim. With the latest version of Emotet, the hacker then sends an even more deadly cyber weapon called Trickbot which is used to spread the attack to other computers on the network. Now that you know more about how these attacks get started, let’s look closer at Trickbot which is the second wave of the attack.
IV. History of Trickbot
Trickbot is a persistent cyber weapon that uses a variety of holes in Windows programs such as Microsoft Office and Outlook to infiltrate Windows computer networks and spread malware from computer to computer. Trickbot these days is typically a secondary infection or second wave which comes after a computer has been infected with Emotet. In fact, these days, it can be hard to tell where Emotet stops and Trickbot starts as they both use very similar tools. The biggest difference between them is that Trickbot now comes with Eternal Blue and other NSA hacking tools to help it spread across a network from computer to computer. Once silently downloaded from the Command and Control server, Trickbot moves laterally through the Windows computer network, often using the Microsoft Outlook Email Manager to gain passwords and take control over the entire network. Due to the way Trickbot uses the NSA Eternal Blue vulnerability to spread through a company’s network, any infected machine on the network will re-infect machines that have been previously cleaned when they rejoin the network.
Trickbot was first noticed in October 2016. However, an earlier version of Trickbot, called Drye (also known as Dyreza), was in existence two year earlier, in June 2014. Drye in turn evolved from Zues which infected nearly 4 million computers in the US in 2009 – using many of the same fake email and download techniques used by Drye, Emotet and Trickbot.
Like many other NSA-based cyber weapons, Trickbot uses SSL to communicate with remote Command and Control servers allowing the hackers to load additional malware onto the Windows computer networks. My prior analysis of the IP addresses of these Command and Control servers confirmed that the vast majority of these servers are located in the United States. This indicates that the hackers are also located in the US.
Because Trickbot actively communicates with Command and Control servers over time, Trickbot is not an isolated weapon in a single attack. Rather, Trickbot is simply the second phase in a process of information gathering and password stealing that over a period of months allowed hackers to gain control over a victim’s computer network.
Because Trickbot is able to move laterally, it can quickly turn one infected computer into a thousand infected computers. https://www.forbes.com/sites/daveywinder/2019/07/31/windows-10-warning-250m-account-takeover-trojan-disables-windows-defender/#70de1e886fef
Trickbot is particularly fond of Windows 10 computers. Here is a quote from a July 31, 2019 Forbes article: “Trickbot is not a new threat, but it is an evolving one. The latest twist of the banking Trojan knife as far as Windows 10 users are concerned is the addition of new methods to not only evade but actually disable Windows Defender security protection…
A study on the relationship between Emotet and Trickbot found that it only took 20 minutes from the time Emotet inficted a computer to the time Trickbot was downloaded to the computer. https://unit42.paloaltonetworks.com/unit42-malware-team-malspam-pushing-emotet-trickbot/
We will review how Trickbot spreads from computer to computer in a later section of this report.
V. History of Xbot
If you do a Google search for the term Xbot, you will see these two definitions in the Urban Dictionary:
1. A creature that dwells in the depths of Microsoft, (so loyal to Microsoft that they) create flame wars with anyone that dares to insult Microsoft in anyway.
2. A person who is blindly, fanatically loyal to Microsoft.
While forks refusing to see the security flaws of the Windows operating system even when they are the victims of these flaws is a problem, in this article, I use the term Xbot not to refer to Microsoft Fan Boys but rather to refer to the evolution of a hacking tool created beginning in 2007 and continuing to the present day. The term botnet or bot in malware refers to
“a type of malware that secretly takes hold of a large network of machines and can be exploited to perform malicious tasks without the victim being aware.” As the UEFI hacking tool relies on the user lack of awareness, Xbot is the perfect name for it.
The first public reference to this NSA tool was in a Snowden document, published by Der Spiegel in 2015. The Der Spiegel articl included a copy of a Job Announcement issued on July 11, 2006 by the NSA “Persistence Division” looking for programmers to develop EFI firmware hacking tools beginning in January 2007. Here is a quote from this NSA job announcement:
“BERSERKR is a persistent backdoor that is implanted into the BIOS and runs from SMM… There is a prototype that Works on Windows 7 but this also needs to work on Windows 2008.”
Here is an image of the 2006 NSA job announcement:

The firmware implant (Berserkr) hides from the user on a hidden Partition that cannot be seen or accessed by the user but which can be activated by a secret “hook” or custom command. http://www.spiegel.de/media/media-35661.pdf
The following image is from a 2007 NSA Slideshow supplied by Snowden and made public by the Intercept on January 24 2019. The NSA and its Sub-contractors have at least 100,000 hackers.
https://theintercept.com/document/2019/01/24/tailored-access-operations-2007/
This is slide 7 which describes the mission of the NSA Persistence Division which is part of the NSA Access Tech Division. Note the emphasis on remote access to Firmware and working with their “community partners” aka Microsoft and Intel. Another January 2007 NSA document referred to Supply Chain attacks using “Sierra Mist” which is a hidden partition on nearly all hard drives used to compromise “Firmware BIOS”.

Note that the Sierra Mist Cyber Weapon is intended to be placed as a module inside of a EFI module. EFI refers to the Extensible Firmware Interface (which is now known as UEFI or the Unified Extensible Firmware Interface). What is extremely strange about creating a persistent cyber weapon to be placed inside of an EFI module is that not a single commercial computer in the world used EFI or UEFI in 2007.

In fact, UEFI was not introduced on Windows servers until 2009 and was not introduced on Windows computers until the introduction of Windows 8 in 2011. This is clear evidence that the NSA had a hand in the development of UEFI itself as a cyber weapon for the NSA. I first learned about UEFI from a speech given by Bill Gates on May 23, 2006. Here is a quote from Bill the day he announced UEFI to the world:

UEFI version 1.0 in 2006 was not that different from BIOS. In particular, it did not include secure boot. Neither did UEFI version 2.1 which was released on January 7, 2007. So what the heck was Bill Gates talking about in his 2006 speech when he referred to a “new capability”? Little did we know then that by “us” Bill was referring to his Prism Partners at the NSA and that by “new capability” Bill meant that the NSA would soon be able to hack into any computer on the planet by hacking into the new back doors they placed in the UEFI BIOS.
In my previous article, I detailed the entire history of how UEFI was started by the NSA in 2007 and evolved over several years into the cyber weapon it is today. I will not repeat all of that here. But if you still think that UEFI is some sort of friendly product created by a non-profit group then you need to read the following article. https://learnlinuxandlibreoffice.org/news/the-fight-for-a-secure-linux-bios
You can also view a video presentation of this article at the following link: https://www.youtube.com/watch?v=mEPcRFvvekY
The article and presentation provide dozens of links and a complete history of this hacking tool starting in 2007 and ending with the latest version in April 2019. This NSA UEFI hacking tool while well known in the hacker world, surprisingly has no official sounding name – despite being the most dangerous hacking tool in history. This is why I now refer to this UEFI hacking tool as Xbot – the bot with no name. What nearly all of these NSA-based cyber weapons have in common is that they were specifically designed for Windows computers running the UEFI BIOS program. The method they use to achieve real persistence is what the NSA originally called Berserkrk and later called Sierra Mist and I now call Xbot.
Xbot gives Trickbot and Ryuk cyber weapons what the NSA called “persistence.” Persistence means that NSA-based malware, including Trickbot and Ryuk can survive replacing the operating system and even replacing the hard drive. These extremely complex hacking tools can hide in several places including in the computer firmware, the computer RAM chips and even in the computer central processing units.
This included “persistent” control over not only the operating systems, databases, backups and other programs but also the hard drives, firmware and even the Central Processing Units. It is because of this persistent control that Ryuk Ransomware includes a message warning victims to not turn off their computers – because the malware buried in the UEFI BIOS of the firmware will then corrupt the data in the computer making it impossible to recover. You will not find any online links between Xbot, UEFI and Ryuk. But hackers who are capable of combining Trickbot with Ryuk are clearly capable of combining Xbot with Ryuk.
Here is an April 2017 Video on UEFI Ransomware
https://www.youtube.com/watch?v=xYrcaa1fSXA&t=130s
Here is what your screen looks like at the end of this 5 minute video:

At the Black Hat Asia 2017 security conference, researchers from Cylance disclosed two more vulnerabilities which allow an attacker to write malicious content to the UEFI firmware. They noted the same flaws can be used to plant rootkits that allow attackers to persist malware for years.
In this April 2018 video a 20 year old hacker explains how to hack UEFI in 13 minutes. “You do not need to know much “Because UEFI is badly written software. I call this the Lord of the Rings attack Others call it the SMM attack. SMM is controlling everything “ https://www.youtube.com/watch?v=lzZvL1wZ-WM

If a 20 year old kids knows how to implant Xbot, you can bet that professional hackers also know how to do the same.
VI. History of Ryuk
As noted earlier, some so-called security experts have claimed that Ryuk is a new kind of Ransomware that was first noticed in August 2018. These same experts claim that Ryuk was created by North Korean or Russian hackers. What these experts ignore is the capability of an NSA tool called Marble Framework to hide the real original source of malware. Thanks to the Wikileaks release of the NSA Marble Framework in March 2017, we know that for a long time prior to 2017, the NSA was producing cyber weapons using Russian, Chinese and several other languages to hide the fact that the tools were written by the NSA.
There are many indications that Ryuk does not come from some foreign country. One of the biggest is that Ryuk has a valid signed certificate of trust called a Thawte Certificate. These Signed Certificates are generally not issued to Russian or North Korean hackers. The certificate was issued to WMV CONSULTING LTD which is registered in the United Kingdom but appears to be a front for some other organization. Still, it is difficult to believe that either Russia or North Korea would register their hacking group in Great Britain. Instead, Ryuk seems to be mimicking NSA viruses like Stuxnet and Flame both of which used Microsoft signed certificates to evade detection. What was interesting about the Microsoft Certificates is that instead of being valid for the normal two years, the certificates Microsoft issued to the NSA for their Cyber Weapons was valid for six years. This is not only extremely unusual, it is one of several pieces of hard evidence indicating that Microsoft was cooperating directly and actively in assisting the NSA in the development of their cyber weapons.
To find the real source of cyber weapons, all one needs to do is follow the money. The NSA has a budget that is at least 100 times larger than all of the other hacking groups in the world combined. Thus, the odds of any malware or complex cyber weapon coming from the NSA rather than North Korea, Russia, China or Iran are on the order of 100 to 1.
In addition to following the money, we can follow the IP addresses of the hackers Command and Control servers. Hundreds of these IP addresses have been published by researchers analyzing Trickbot, Ryuk and other cyber weapons.
Most of these Command and Control servers are located here in the USA. The location of these IP addresses is significant because, thanks to the USA Patriot Act, all servers in the US are subject to search by the FBI. US servers would therefore be the last place that Russian, Chinese, Iranian or North Korean hackers would use for Command and Control servers. Remember this the next time someone tells you that the Russians and/or Koreans are the source of Ryuk Ransomware.
As just one example of how far the NSA is willing to go to maintain this deception about Korean hackers invading our computers, on June 8 2018, the NSA actually filed charges against a North Korean for being the mastermind behind the WannaCry Cyber attacks. The complaint filed in a federal court in Los Angeles CA was 176 pages long and includes lots the IP addresses of lots of servers used by the hacker. While some of these servers may in fact have been in North Korea, most of the IP addresses were in the United States. If you were a North Korean hacker would you really be using US servers?
In addition, the complaint claimed that this hacker was able to rob millions of dollars from several banks. Yet these same hackers were not able to hack the networks of local US movie theaters. To be clear, I am not claiming that North Koreans and Russians do not engage in hacking. What I am claiming is that neither of them would be using US servers. I am also certain that international banks have more secure computer networks than your local movie theater.
Finally, in recent months we have learned that Ryuk is typically downloaded AFTER the victim’s computer network has been infected by Trickbot. Trickbot in turn can take several months to take over a computer network. In fact, since Trickbot is also used to infect the backup files of a computer network, it is possible that the Ryuk attacks first seen in August 2018 actually began some time in 2017 shortly after the NSA hacking tools were released into the wild.
The NSA simply does not want the US public to know that they originally created nearly all cyber weapons being used in the world today. So they make up stories about North Korean, Russian, Chinese and Iranian hackers to mislead the public. This is also why they use the Marble Framework to include Russian language words in their malware. The NSA also releases stories about “new” types of ransomware with new names like Ryuk and Trickbot to make it seem like there are new cyber warfare threats each year. In fact, it would be more accurate to describe Ryuk, Trickbot, WannaCry and NotPetya ransomware as an evolution of the Stuxnet and Flame cyber weapons that were first unleashed by the NSA way back in 2007.
To make matters worse, reports indicate that Ryuk Ransomware has a low data recovery-success rate after a ransom payment is made. Relative to other types of ransomware, the decryption tool is very labor intensive and prone to failure.
VII. How Emotet, Trickbot, Ryuk and Xbot Work
Getting someone to download malware is the easiest part of hacking a network. The harder part is transferring the malware to other computers in the network. The key is to have a willing predictable and not-very-secure host computer. This is where Windows computers come in. They have very predictable holes that are easily exploited. Specifically, the Windows operating system is the only operating system in the world that allows the web browser inside of the core of the operating system. Neither Apple or Linux have this not-so-hidden back door. I have covered how NSA-based malware gains persistence in my previous article noted earlier.
Here we will review how Trickbot transfers Ryuk Ransomware from computer to computer within the network. Conveniently, all Windows computers have a network communication protocol called Server Message Block (aka SMB). The NSA cyber weapon, Eternal Blue uses SMB in combination with Microsoft Outlook to transfer malware from computer to computer – almost as if this was what SMB was designed to do. WannaCry, NotPetya and Trickbot all use Eternal Blue and SMB and Microsoft Outlook to transfer malware from computer to computer.
It is important to note that initially Ryuk Ransomware is not installed on the victim computer. Rather first Emotet is downloaded onto a single computer, then Trickbot is downloaded onto the victim computer. Then Trickbot infects the rest of the computers on the Windows network. Then Trickbot performs a series of steps before deciding whether or not to download Ryuk Ransomware. Among these steps are stealing administrator passwords and determining the number and models of computers on the network as well as infecting all of the backup databases and files.
This information is sent back via command and control servers to the hackers who then research their potential victims ability to pay. If the hackers want persistence even after the ransom is paid, it is a simple matter to place Xbot inside of the UEFI BIOS chip on all of the computers in the victims computer network. Ryuk ransomware is then sent to infect the currently active database.
Here is a diagram of this process:
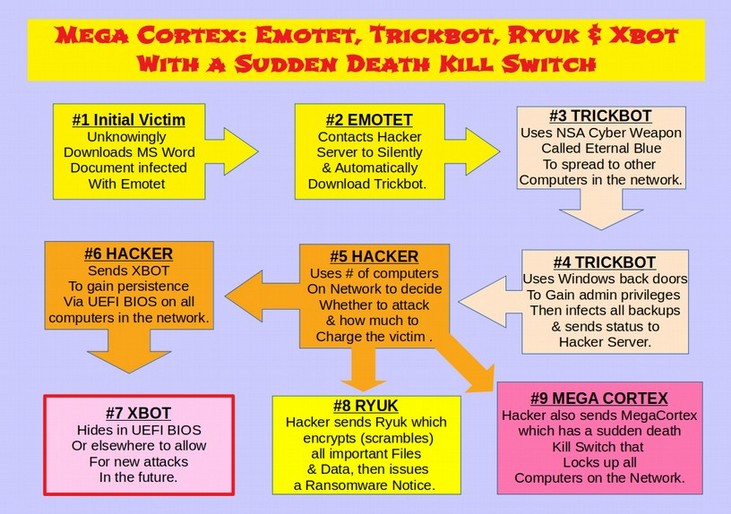
How Ryuk uses normal Windows Functions to Take Over and Encrypt the Network
According to a January 2019 Fire Eye Report, Ryuk Ransomware hackers have been active since at least December 2017. https://www.fireeye.com/blog/threat-research/2019/01/a-nasty-trick-from-credential-theft-malware-to-business-disruption.html
Curiously, the Fire Eye analysis found that the attackers performed host and network reconnaissance using normal built-in Windows commands such AdFind.exe. Here is a quote from their findings: “AdFind.exe was executed using a batch script, which was crafted to pass a series of commands that were used to collect information about Active Directory users, systems, OUs, subnets, groups, and trust objects… This process was performed twice on the same domain controller, 10 hours apart. Between executions of Adfind the attacker tested access to multiple domain controllers in the victim environment, including the one later used to deploy Ryuk… “
A Google search of the adfind.exe function reveals that it was originally developed prior to 2003 and originally developed for use on Microsoft Windows Exchange Servers. Adfind is still being actively developed with the latest version being written in Microsoft Visual Studio and released on October 31, 2017. Adfind still works on Windows Server 2019. In fact, Adfind is available for free download from this link: http://www.joeware.net/freetools/tools/adfind/
Adfind is free ware meaning there is no cost to download it. But it is not open source. This means that the source code is not available for public inspection. All of the Adfind commands can be found at this link: http://www.joeware.net/freetools/tools/adfind/usage.htm
Here is a link to Microsoft’s domain controller processes: https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-adts/8ebcf782-87fd-4dc3-8585-1301569dfe4f
Here is an article written in August 2006 explaining how to use Adfind. https://thescripter.wordpress.com/2006/08/10/using-the-excellent-and-free-adfind-utility-to-search-windows-active-directory/
The AD in Adfind stands for Active Directory. Here is a quote from the above article: “Running Adfind against your AD will provide you with a nice comma-separated dump of all your Contact object’s display names and primary e-mail addresses.”
Another article states: ‘Working with Adfind is not restricted by the local security measures.”
Another 2010 article states: “Adfind can be used to query the Active Directory for user accounts, groups, OUs, containers, Schema elements and other resources based on a variety of advanced search criteria. It is a command-line tool and once you have learned its command line options, it is rather easy to use.”
An April 2019 Fire Eye article stated that Adfind and other publicly available tools can be used to install “malicious Windows services to execute Power Shell commands on remote systems.” https://www.fireeye.com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
The hackers in question compromised one computer on the network (likely with Emotet). They then moved laterally through the system using the Windows Remote Desktop Protocol (RDP) likely with something similar to Trickbot and Eternal Blue. The hackers then used Adfind to get information from the Windows Active Directory. The information included Active Directory users, computers, organizational units, subnets, groups, and trusts. To ensure a high success rate, the attacker used compromised domain administrator credentials (which they obtained earlier through the use of Emotet and Trickbot). Domain administrators have complete control over Windows systems in an Active Directory environment. These ransomware attacks from just one hacker have cost victims tens of millions of dollars. The report then concludes with more than one dozen IP addresses used by the hackers. Most of the IP addresses were located here in the United States. But servers were also located in several other countries that are connect with the NSA Five Eyes system. Here are just a few of the IP addresses:
31.220.45[.]151 located in the Netherlands
46.166.173[.]109 located in Lithuania
62.210.136[.]65 located in France
103.73.65[.]116 located in Australia
185.202.174[.]31 located in the United States
185.202.174[.]80 located in the United States
185.202.174[.]84 located in the United States
185.202.174[.]91 located in the United States
185.222.211[.]98 located in the United States
Returning to the first Fire Eye article on Ryuk:“The attacker then logged into a domain controller and copied instances of PSExec.exe, a batch script used to kill processes and stop services, and an instance of Ryuk onto the system… Using PsExec the attacker copied the process/service killing batch script to the %TEMP% folder on hundreds of computers across the victim environment, from which it was then executed. The attacker then used PsExec to copy the Ryuk binary to the %SystemRoot% directories of these same computers. A new service configured to launch the Ryuk binary was then created and started. Ryuk execution proceeded as normal, encrypting files on impacted systems.”
In short, the Windows operating system normal functions were used to encrypt the files on the system. It is as if Windows is an accomplice in this crime.
My point in providing these links and quotes is to show that you do not have to be a Russian spy or North Korean hacker or computer genius to learn how Ryuk Ransomware works. The information is publicly available on the Internet and has been for over 10 years.
The Fire Eye report also noted that Ryuk has been found to lie dormant for up to a year before encrypting the files and sending the ransom note. There is not question that the reason it is lying dormant for so long is to make sure that all useful backup files have also been infected – rendering backups to be useless.
The goal of Ryuk in laying dormant for so long and corrupting the backup files is to leave victims with no other choice but to pay the ransom or lose all of their data. Therefore, by the time the victim receives the ransom note, which is often $100,000 or more, they have already been infected for months and it is likely than many if not all of their backup files have also been infected.
Paying the ransom is likely to only bring temporary relief as the hackers are still inside of the UEFI BIOS of all of the computers on the victim’s network. Also, hacking tools are evolving into ever more deadly strains over time. In the next section, we will cover the latest deadly strain of Ryuk Ransomware, called Mega Cortex, which is basically Ryuk Ransomware with a sudden death kill switch.
VIII. Mega Cortex… Ryuk Ransomware with a Kill Switch
Even if you do manage to protect yourself from Ryuk, hackers are constantly improving their ransomware. In fact, in early 2019 hackers introduced a new version of Ryuk called Locker Goga that is making Ryuk obsolete. Locker Goga uses multiple certificate authorities instead of just one.
Like Ryuk, Locker Goga uses Microsoft Server Message Block (SMB) protocol (aka Eternal Blue) and Windows Active Directory management services and MS Outlook to spread from computer to computer in infected networks. Locker Goga encrypts documents and PDFs, spreadsheets and PowerPoint files, database files, and videos, as well as JavaScript and Python files. Some hackers are downloading both Ryuk and Locker Goga onto the same infected systems.
What can be the purpose of using two separate encryption tools on the same system? Here is one clue. While there are ways to decrypt files that have been encrypted by Ryuk, (such as getting a key from the hackers after you have paid the ransom), there is currently no known way to unlock or decrypt systems and files that have been encrypted with Locker Goga. https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/what-you-need-to-know-about-the-lockergoga-ransomware/
In fact, Locker Goga makes it impossible to even boot up or log into your network after it becomes active because Locker Goga even encrypts your the Windows Boot Manager. And Locker Goga modifies the passwords of all users on the system. Trying to start your network simply displays the following screen:
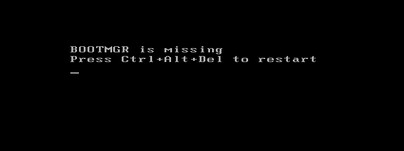
While many have pointed out that completely destroying your computer network is counter productive as it makes it harder or even impossible for you to pay the ransom, the threat of Locker Goga in fact makes it more likely that organizations will pay the Ryuk ransom rather than suffer the Locker Goga Sudden Death Kill Switch consequences.
Imagine using a backup to restore your files rather than paying the hackers. Now imagine the hackers still have access to your computer system by hiding in the UEFI BIOS. Now imagine they wait a few months and then hit you with Locker Goga. This is the predictable evolution of Windows based hacking tools. One Locker Goga attack cost its victim, a Norwegian Power System, more than $40 million.
Evidence to support my claim that victims of Emotet, Trickbot and Ryuk are more likely to become victims of even more advanced cyber weapons, an even newer type of ransomware called MegaCortex was reported in May 2019 which has similarities to Locker Goga. https://www.darkreading.com/perimeter/lockergoga-megacortex-ransomware-share-unlikely-traits/d/d-id/1334696
Here is a quote from this article:
“Researchers note this ransomware is mostly seen among businesses with existing Emotet infections, which can be used as launching points to distribute other malware… At least one of the C2 (command and control IP) addresses that MegaCortex contacts has also been used by Locker Goga.”
Like Locker Goga, MegaCortex uses a variety of signed and valid certificates to get past checking systems. At least one of the certificates was issued by an authority in London, UK. Some of the certificates were signed on March 14, 2019 and are valid until March 14, 2020.
Here is the MegaCortex Ransom Note:
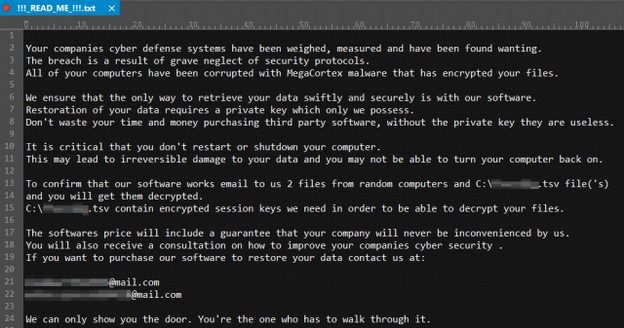
The IP address for this new attack was from a server in the Netherlands. Note that, in the ransom note, the ransomers themselves named their hacking tool MegaCortex. This is highly unusual. Normally hacking tools are named by the researchers who first report them.
A recent analysis of MegaCortex found that MegaCortex was revised on July 15, 2019 using a new and valid Thawte certificate issued to Abadan Pizza in London England. Here is a Google image of this location:

Then on August 6, 2019, a new version of MegaCortex, called version 2 was released. This new version is asking a ransom of $5.8 million to get your computers back. This is 10 times more than the highest ransom paid for Ryuk – making Ryuk seem like small potatoes. https://securityintelligence.com/news/megacortex-ransomware-v2-released-with-anti-analysis-features/

MegaCortex made it to the top of the Windows Ransomware Hit Parade with a successful July 16, 2019 attack against a noted cloud hosting provider called iNSYNQ – which is an authorized Microsoft and Intuit hosting provider for businesses using Intuit Quickbooks accounting software. iNSYNQ is located in Gig Harbor Washington.
iNSYNQ hosting includes automatic daily backups. However, it appears that backups of clients have also been compromised as clients have been warned to test their backups before using them. https://www.cyber.nj.gov/alerts-and-advisories/20190730/insynq-cloud-hosting-firm-confirms-megacortex-ransomware-attack
Nearly one month after the attack, the following notice still appears on their support page:

Here is a quote from a blog post the company issued about the attack:
“This continues to be difficult to navigate to say the least- malware attacks are an industry-wide phenomenon, that no one is 100% impervious to. Businesses large and small, individuals and even are own government have been blindsided by malicious actors in the recent months. We've received confirmation from security experts that we were hit with a sophisticated malware, relatively unknown to even experts in cyber security.”
What is amazing to me is that this company does not seem to be even remotely aware of the dangers of using Windows servers.
On August 5 2019, a security research group from IBM called X force issued a report on “destructive” ransomware such as Locker Gaga and Mega Cortex. The report stated:
“IBM X-Force Incident Response and Intelligence Services (IRIS) estimates that victimized organizations on average experience a total cost of over $200 million and have more than 12,000 devices destroyed in an attack. Recovery from destructive malware can also require hundreds of hours to remediate and rebuild environments that have been destroyed. The NotPetya malware that hit organizations across the globe is a stark example of the costly damage that destructive malware can leave in its wake. According to a White House assessment, NotPetya caused serious business disruption across geographies and resulted in more than $10 billion in total damages.”
“Since 2018, X-Force IRIS has been observing cyber criminals increasingly incorporate destructive components, such as wiper malware, into their attacks on commercial entities. This is especially true for cyber criminals who use ransomware like Locker Goga and MegaCortex to infect enterprise networks. Cyber criminals may be adopting these destructive elements to add pressure to their demands that victims pay the ransom—adding irreparable data destruction to encryption as a potential repercussion. In many destructive malware attacks, the number of workstations affected may be as high as three-quarters or more of the total network.”
“Ransomware attacks containing a destructive element have spiked in 2019, as new strains of ransomware such as Locker Goga and Mega Cortex entered the cyber crime arena. X-Force IRIS incident response data indicates that ransomware attack calls to our emergency response hot line have more than doubled over the past twelve months, with an increase of 116% from the second half of 2018 to the first half of 2019.”
“We’ve observed attackers reside in targeted environments for over four months prior to launching a destructive payload, giving them ample time for internal reconnaissance where they map out the infrastructure and find ways to achieve their objectives.”
“PowerShell, a Microsoft framework that is both a scripting language and a command line executor, first appeared in 2006 and has been a standard feature of the Windows operating system ever since. Power Shell scripting has been increasingly gaining popularity among adversarial actors since 2016 as one of the most frequently used lateral movement techniques observed by X-Force IRIS incident responders, and destructive malware attackers have followed this trend. Modern ransomware variants, such as MegaCortex, can use malicious PowerShell scripts to move between networked devices. PowerShell is native to the Windows operating environment, making it appear legitimate and thereby more difficult to identify as anomalous activity, which can further challenge detection and response.”
“As we move into the second half of 2019, additional cyber criminal groups—particularly those intent on conducting ransomware attacks— are recognizing the utility of having a wiping mechanism built into their tools. This type of mechanism can provide adversaries with additional options to pressure victims, while simultaneously increasing the risk of an attack that will require disaster recovery. This trend leads us to believe that more financially-motivated cyber criminal groups are likely to explore destructive malware as an option to incorporate into current attacks.”
https://www.ibm.com/downloads/cas/8ODXVKLJ
As further evidence that initial attacks can lead to further attacks, Louisville's federally funded Park DuValle Community Health Center paid a $70,000 ransom for an attack in April, 2019 only to be hit again in June 2019.
https://www.upi.com/Top_News/US/2019/08/07/Destructive-malware-attacks-have-surged-200-in-past-year-experts-say/1541565141297/
On August 16, 2019, at least 23 state agencies in Texas were hit by a “coordinated ransomware attack” just days after it was revealed that the city of Baltimore had to spend more than $20 million to recover from their ransomware attack. The majority of the 23 agencies were small local governments. All 23 attacks are believed to have the same source. The fact that this hacker hit all 23 state agencies at the same time is a strong indication that the system was compromised months ago and that hacker spent months planning this attack.
This is just the latest in an ongoing epidemic of data breaches and hacking incidents. The federal Department of Health and Human Services keeps a website listing all reported data breaches. In July 2019 alone, there were dozens of breaches affecting more than 30 million people. Many of these attacks are repeat attacks on the same servers.
https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
It is time to stop thinking of each of these hacking tools in isolation and start thinking of them as part of an evolution of NSA based Windows ransomware. Clearly, the Windows ransomware situation is rapidly evolving and becoming much worse over time.
In fact, as hackers get better at extracting money from their victims, Windows ransomware seems to be spiraling out of control. Therefore, the only way for victims of past ransomware attacks to really protect themselves from another Ryuk Ransomware attack (or an even more powerful ransomware attack) is to eliminate both the Windows OS that allows it and the presence of Xbot in your system BIOS. This means getting rid of Windows and its side kick UEFI BIOS.
IX. How to Recover & Protect Yourself from Future Attacks
Now that we have a better understanding of how Emotet, Trickbot, Xbot, Ryuk and Mega Cortex work, we can consider how to really recover from a Ryuk Ransomware attack and truly protect your computer network from future attacks. This sadly it an area where Ryuk victims have been given extremely bad advice. First, these victims are attacked by Ryuk and often wind up paying a huge ransom for temporary relief. Then these same victims fall pry to so-called “security experts” who give them very expensive advice that does not even remotely solve the long term problem of avoiding not only Ryuk but also avoiding future attacks by Emotet, Trickbot and Xbot. So before we consider how to really recover from a Ryuk attack, let’s look at some typical advice and why none of what Ryuk victims are currently being told solves the long term problems.
Stockholm Syndrome… Blaming the Victims
What is most distressing about the advice given to victims of ransomware attacks is that nearly all of this advice blames the victim for the attack. If only they had better backups. If only they had done more staff training. If only they had installed the latest Windows update or the latest anti-virus software. Stockholm Syndrome has been defined as “the psychological tendency to blame the victims of a crime for being partially or completely responsible for the crime that was committed against them.”

Let’s take a closer look at advice being given to victims to see why it will not actually solve the underlying causes of the ransomware problem:
#1 Why Backups are not an effective solution to the Ryuk Problem
Many so-called security experts falsely claim that all you need to do is keep offline backups of your network and use these backups to replace your encrypted data should your network become a victim. What these experts fail to understand is that Trickbot has tools to implant itself in the backups. Trickbot often spends months infecting these backups. So unless the backup is more than a year old, the backups could also be contaminated. The backup may appear to work for a while. But if it also is contaminated, another ransom demand is likely to be issued in the future.
To be clear, I am not saying to skip backups. You should have both externally stored backups and cloud based backups with syncing tools for both. These are useful for solving other problems. However, backups by themselves will not solve the Ryuk Ransomware problem.
#2 Staff Training to not click on links is not an effective solution
Another naive bit of advice is to better train staff how to recognize malicious email attachments – or even prevent staff from downloading attachments or clicking on links altogether. While staff training might reduce the chances of downloading Emotet and Trickbot in the first place, once Trickbot is downloaded, it goes about stealing passwords and credentials without any further need to be downloaded again. Moreover, staff should be expected to download files and click on links as an effective part of doing their research. The last thing staff should be told is to be afraid to click on a link. What if the link actually is about an important invoice or UPS shipment?
It it true that you can avoid security problems by never letting your staff go online. But this ignores the ultimate source of the problem. The problem is not your staff downloading attachments and clicking on links. The problem is that the Windows operating system is so insecure that hackers can use normal staff activities to infect the Windows operating system. Blaming your staff is like blaming the victim for being attacked.
The problem in its most simple terms is that Bill Gates made a mistake in 1998 when he placed the Internet Explorer Web Browser inside the core of the Windows operating system. The Windows operating system has been insecure ever since. There is no solution to this problem other than to replace the Windows operating system with a more secure operating system that does not have the web browser inside the core.
Even if no one on your network downloads any more infected Microsoft Office documents and even if your backup was not corrupted, as long as you are using the Windows operating system and UEFI BIOS, the malware can hide in several other parts of your computer network. Again, your network may appear to have recovered only to be subject to additional hacking attacks in the future.
Instead, if you switch to a more secure operating system, such as Linux, your staff can click on whatever links they want and download whatever attachments they want. Even if they download a malicious Word document, it will not be able to infect the Linux operating system or travel from computer to computer across the network because Linux has a much more secure file structure and permissions structure than Windows.
#3 Forcing Staff to use Longer or Two Factor Passwords is not a solution
While longer passwords and two factor authentication may help protect against brute force attacks, neither Ryuk or Mega Cortex are brute force attacks. Both use much more subtle methods to get inside your computer network. Once inside, it does not matter how long the passwords are or where they are stored. This is because Trickbot has tools to gather up all administrator passwords. So long passwords and two factor passwords are at best a distraction and at worst lead to a false sense of security.
#4 Antivirus Programs are not an effective long term solution
Third, many so-called experts sell Ryuk victims one or more commercial anti-virus solutions. However, none of these anti-virus programs can completely protect Windows computers because Windows computers suffer from several fundamental security flaws. Anti-virus program providers do not want you to be cured from this disease because they make money by providing monthly fixes for what is in fact an insecure Windows operating system. By contrast, ant-virus programs are not needed on Linux computers because there is no open back door into the core of the Linux operating system to begin with.
#5 Upgrading from Windows 7 to Windows 10 is not a solution
Neither is upgrading from Windows 7 to Windows 10 a solution to the Ryuk problem. In fact, Windows 10 is less secure than was Windows 7. Even its normal update process, Windows 10 has crashed millions of computers – without any malware attacks. This is because Windows 10 has three major problems that Windows 7 did not have.
The first problem is that Microsoft executives (against the advice of their own programmers) introduced a second control panel with Windows 8 and continued this second control panel with Windows 10. As only some of the functions were migrated to the second control panel, the first control panel is still on Windows 10. This creates huge stability problems which is why Windows 10 computers are so prone to crashing. It is like having two pilots trying to control and fly the same plane at the same time. The right hand never knows what the left hand is doing and the plane occasionally crashes into the ground.
The second problem is because each control panel needs a way to communicate with the Mother Ship (Microsoft), Windows 8 also introduced a second web browser into the core of their operating system. This second web browser is in fact a second back door into the Windows 8 and Windows 10 operating system.
Third and most important, Windows 8 and Windows 10 do not work with what is now called Legacy BIOS. Both only work with UEFI BIOS. As I explained earlier and wrote about extensively in my previous article, UEFI BIOS was developed by the NSA and is itself basically a cyber weapon. UEFI BIOS is what gives the NSA (and hackers who mimic the NSA) persistent access to your computer network even if you replace the Windows operating system and the hard drives.
#6 Updating Windows is not an effective long term solution
Finally, many so-called security experts claim that all you need to do is install the latest Windows operating system patches. These patches have a long history of not working and causing computer networks to crash even if they are not infected with Ryuk Ransomware. Microsoft issues updates on the second Tuesday of every month. This has become known as Patch Tuesday. The not so funny joke is that Patch Tuesday is followed by Crash Wednesday.
As examples of how futile Windows Updates are, just look at the past two Windows monthly updates. On August 13 2019, Microsoft released patches for 93 security flaws. The most dangerous of these flaws were four remote code execution (RCE) flaws that take advantage of holes in Windows Remote Desktop Service (RDS). The numbers for these flaws are CVE-2019-1181, CVE-2019-1182, CVE-2019-1222, and CVE-2019-1226. For those keeping score, this is the fourth time in 2019 Microsoft has had to fix critical security issues with its Remote Desktop service.
But the notice included a total of 29 remote execution flaws affecting nearly every type of Windows program from MS Word to MS Outlook. Hackers can exploit any of these 29 Remote Code Execution flaws to take over a computer and then spread malware to other computers on the same network without any user interaction.
The Security Update Guide for August 2019 explaining all of these flaws was over 100 pages long. This is based on the following Microsoft link which lists 20 flaws per page and has a total of 2355 items divided over 118 pages. But the Excel spreadsheet for all of the flaws actually listed 2,977 flaws being patched. The file size for just the August 2019 Update was 1038 Megabytes (over 1 Gigabyte).
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4512497
Nor was this unusual for Microsoft to have dozens of security flaws revealed in a single month. The July 2019 Windows Update attempted to fix almost 80 security holes in the Windows operating systems and related software. Among them were patches for two zero-day flaws that are actively being exploited in the wild. Every month, dozens of patches are issued for dozens of security holes. None of the patches actually fix the holes which is why a new round of additional patches are needed each month.
All the patches really do is create their own problems which every month cause millions of Windows computers to crash. Many computer network operators have attempted to avoid these problems by not updating to Windows 10. However, Microsoft has announced that in January 2020, they are ending support for both Windows 7 and Legacy BIOS. This is intended to force all users to adopt Windows 10 and UEFI BIOS regardless of how insecure those options are.
But the problem with forcing the entire world to use the same top down monopoly based operating system and BIOS system is that, while this makes it easier for Microsoft and the NSA to control our computers, it also makes it easier for hackers to hack our computers.
The Real Solution to Prevent Future Ryuk Attacks is to Switch to Linux OS and Linux BIOS
The only real solution to Ryuk, Trickbot, WannaCry, Not Petya and all other NSA based Windows based hacking tools is to move away from the poorly designed Windows operating system to the vastly more secure Linux Operating system. Linux does not keep the web browser inside of the core of the operating system. Thus, there are no easy back doors into the Linux operating system. This is why none of the current ransomware tools work on Linux computer networks. This is why large corporations like Google, Facebook and Amazon long ago moved their millions of servers to Linux. Google, Facebook and Amazon have also invested millions of dollars in non-UEFI based BIOS programs. These include Coreboot and Linux BIOS.
Sadly, not all current computers are compatible with Coreboot or Linux BIOS. Thankfully, all Google Chromebooks use Coreboot. I am writing this article on an Acer C910 laptop that came with Coreboot. I reflashed the Coreboot BIOS to run a full Linux operating system rather than the striped down and limited Chrome operating system that comes with Chromebook laptops. Purism is another maker of fulling functioning Linux computers that come with Coreboot. Several other computer manufacturers have announced plans to switch to Coreboot. Hopefully, they can make the switch before January 2020.
In 2014, even Microsoft began the switch from the Windows operating system to the Linux operating system.

Since 2014, Microsoft has migrated nearly one million servers on their server farm in Quincy Washington from Windows to Linux. Microsoft has also fired tens of thousands of Windows programmers and replaced them with tens of thousands of Linux programmers.
Most recently, IBM has paid $34 billion to purchase a Linux computer service company called Redhat. Nearly all mobile phones also run on Redhat. So the real question is given that Windows vulnerabilities have cost them billions of dollars in ransomware attacks, why have many businesses and colleges been so slow to make the transition from Windows to Linux?
The most common answer is that businesses, schools and colleges are “addicted” to using Windows programs like Microsoft Office (note that the word addicted is a word Bill Gates used to explain why people get hooked on using Windows programs).
Addressing Concerns about Switching from Windows to Linux
First there are typically good free secure open source alternatives to Windows programs. In particular, for years, we have been able to open, edit and save all Microsoft document formats using a free, open source and secure Word Processing program called Libre Office. There are entire websites devoted to doing nothing but providing lists of free open source Linux programs as alternatives to insecure Windows programs.
Second Windows programs can be run inside of the Linux operating system using Wine. Even if you come across a Windows program that does not have an equal or better Linux alternative, you can simply run normal Windows programs inside of Linux using a Linux program called WINE. Again, this function has been around for years.
Third, Windows programs can also be used inside of Windows using a Virtual machine. If you do not want to use Linux alternative programs and do not want to run Windows programs inside of WINE, you can also run Windows programs on the Windows operating system but place the Windows operating system inside of a virtual machine that is running inside of Linux. Virtual machines are much more difficult to hack and much more secure than using Windows as the base operating system.
So the real problem is simply that people are creatures of habit. They are afraid to try new things. But at some point, users are going to say enough it enough. Ryuk and Mega Cortex Ransomware may just be the tipping point into finally convincing corporations, schools and colleges that the time is long past due to move away from Windows to the much more secure Linux operating system.
Four Ways to Try Linux
Some folks think that it is very hard to learn Linux. While some versions of Linux are intended for computer programmers and therefore can be hard to learn, there is a very simple version of Linux called Linux Mint which looks and acts almost exactly like Windows 7. There are several ways to try Linux Mint before making the jump from Windows to Linux.
First, you can install a free program onto any Windows computer called Virtual Box and then load Linux Mint into Virtual Box. I have written instructions for how to do this are on this page: https://learnlinuxandlibreoffice.org/2-linux-to-the-rescue/2-2-take-linux-mint-for-a-test-drive
Second, you can create a create a Linux Mint Live Stick and install it on any old computer that no longer works with Windows 10. Windows 10 requires at least 4 GB of RAM while Linux Mint only requires 2 GB of RAM. If you have an old computer, instead of throwing it away, just replace Windows 7 or whatever else was on it with Linux Mint. It takes less than one hour and your old computer will run better and faster than the day it was new. I have written instructions on how to create a Linux Mint Live stick and install it on any computer on this page: https://learnlinuxandlibreoffice.org/3-create-your-own-linux-computer/3-4-install-linux-mint-on-an-acer-c910-chromebook
Third, if you do not have an old computer to convert and do not want to install Virtual Box on your current computer, you can also try Linux Mint without installing it by setting any computer to boot from a USB stick and then inserting a Linux Mint Live stick into a USB port and turning on the computer. You can practice using Linux without it affecting the hard drive in any way. The only problem with this method is that none of the documents you create will be saved when you turn off the computer.
Fourth, you can create a Linux Mint Persistent Stick, also called a computer on a stick. This is very similar to using a Live Stick to install Linux Mint to the main computer hard drive. Only instead of installing Linux Mint to the computer hard drive, you stick another USB stick in a second USB port and use the Mint Live Stick to install Linux onto the Linux Persistent Stick.

This method of creating a computer on a stick is ideal for teachers and students because it allows them to use a school’s computer lab without altering in any way any of the computers in the lab. Students can save their work and bring their Linux Mint Persistent sticks home and continue to practice using Linux on any computer they may have at their home. Students can even keep their Linux Mint live sticks to continue practicing with even after the course is over. All that is required is about $10 for a USB 3 drive that is 8 to 16 GB to create the Mint Live Stick and about $20 each for a USB 3 drive that is 64 GB to 128 GB to create the Mint Persistent stick. I have written instructions for how to do this at the following page: https://learnlinuxandlibreoffice.org/2-linux-to-the-rescue/2-3-create-a-usb-stick-with-persistent-storage
Switching your computer(s) from Windows to Linux is the best way to protect your computer network from Ryuk Ransomware. But given the harm this new malware is inflicting on computers around the world, what we really need is to train the next generation how to put an end to Ryuk and all other ransomware. That is the subject of the next section.
X. How Schools & Colleges Can Stop Future Cyber Attacks
EdTech Strategies runs the K-12 Cybersecurity Resource Center, which tracks the number of reported cyber attacks that US school districts have faced since 2016. According to their incident map, there have been 533 cyber incidents involving school districts since January 2016, with the majority of attacks concentrated in suburban and urban school districts.
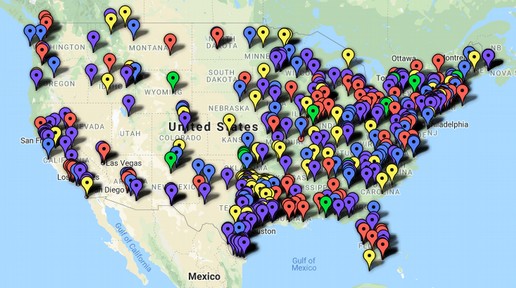
This map does not include all of the colleges and universities that have been hit with ransomware attacks. https://k12cybersecure.com/map/
In February 2018, one third of schools in North Dakota were hit with a malware attack. It took 45 days to clean up the state computer network of 250,000 computers. The North Dakota Department of Education now wants every student in every school learns about cyber security and computer science with new curriculum being developed and introduced in 2019.
In May 2018, the Leominster school district in Massachusetts was hit with a ransomware attack.
In January 2019, the Bridgeport Connecticut school district was hit with a ransomware attack. One teacher lost 18 years of teaching materials stored on the school district computers.
In February 2019, a ransomware attack hit Crosby Independent School District outside Houston. The attack reportedly involved a large bitcoin ransom and took down the district's IT network.
In June 2019, Louisiana, Governor Edwards declared a statewide emergency in response to ransomware attacks on three school districts.
Also in June 2019, a Ransomware attack struck the Syracuse NY school district locking them out of their computers for more than a week and charging the school district more than $100,000 to get their computers back.
In July 2019, in Oklahoma, Broken Arrow Public Schools were also targeted by a ransomware attack, in which an attacker encrypts the system and demands payment to unlock it. School districts in Alabama, Arizona, California, Nevada, New Mexico and New Hampshire were also hit with ransomware attacks in July 2019.
https://www.govtech.com/security/Why-School-Systems-The-Rise-of-Ransomware-in-Public-Schools.html
In every one of the above cases, the real source of the problem was that school districts were using Windows computers instead of Linux computers.
What we really need is more highly trained people that can help schools, colleges and government organizations make the transition from Windows to Linux as soon as possible. This requires not only more teachers trained in Linux but also more and better curriculum about how to switch from Windows to Linux. This was why I started College in the Clouds dot org several years ago and why I created a free online website that explains exactly why and how to switch from Windows to Linux. Here is the link:
https://learnlinuxandlibreoffice.org/
I realized that at some point, that schools and colleges using Windows computers were going to be hacked. My hope was and still is that more school administrators and college administrators would realize the need for more courses on how to use Linux and other free open source tools like Libre Office.
If you are a teacher or an administrator that has been the victim of a Windows ransomware attack, you should visit our website Learn Linux and LibreOffice dot org and learn how to make your own switch from Windows to Linux.
Once you have personally made the switch, you can then help others at your school district and college make the switch.
Most important, school districts and colleges need to offer courses in real computer security. This past year, I developed a course teaching Fifth graders how to use the Linux operating system. They had no problem learning Linux. If a 10 year old can learn Linux, so can you.
As always, I look forward to your questions and comments. Feel free to email me. David at College in the Clouds dot org.
Regards,
David Spring M. Ed.

