III. History of Emotet
Emotet started out in 2014 as a simple email scamming and information-stealing tool that was initially used to gather sensitive financial information from infected Windows computers and forward this information to hackers who would then empty out the victim’s bank account. The first version of Emotet used malicious Javascript files attached to emails to infect Windows computers. Over time, the links and attachments became Word documents, Excel spreadsheets, PDF documents and even images – often supposedly from other people known by the victim (who had also been hacked without knowing it).
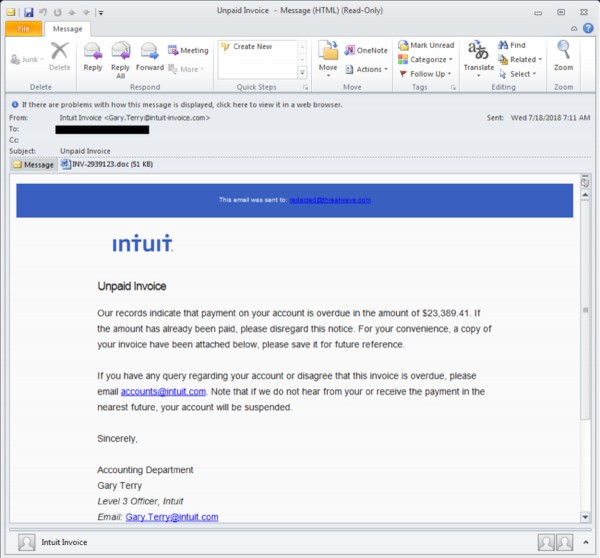
Here is an example of what appears to be an unpaid invoice, but it really a trick to convince the victim to download Emotet.
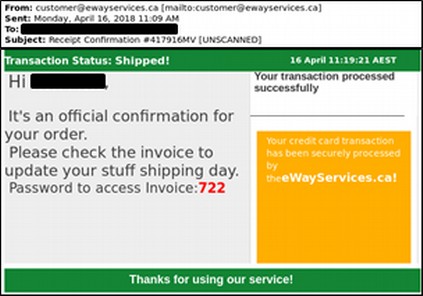
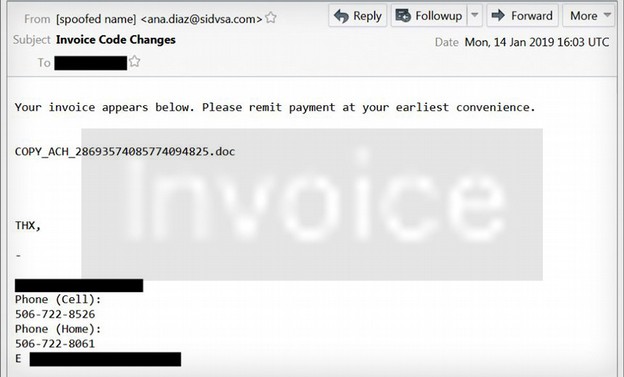
Here is another example of an Emotet spam email:
The link could have also been to someone’s resume or a link to a Youtube video or even a picture of a lost cat. Clicking on any of these links or downloading any of these documents or images from a Windows computer would lead to a download of Emotet.
One of the first goals of Emotet is to find the victim’s email address book. Emotet uses several programs to access your contacts. These programs include a tool called Outlook scrapper to gather all of the names and email addresses of everyone in your Microsoft Outlook email account. The second tool is a password recovery tool that captures all of the passwords you have stored in your browser history. This tool accesses several different browsers including Internet Explorer, Firefox, Google Chrome, Safari and Opera. Remember this the next time your browser asks you if you want it to remember your passwords. The correct answer should be no.
Once Emotet has all of your email contacts and passwords for your email accounts, it then start sending out similar scam emails to every contact in your email address book. The emails appear as though they’re coming from a known sender (you). Recipients of email from a known contact are more likely to open the attachment and become the next victim.
Newer versions of Emotet have evolved to evade most spam filters and use very realistic graphics to fool victims into thinking they are getting an email from a trusted friend or co-worker or major corporation such as Google or UPS or Amazon.
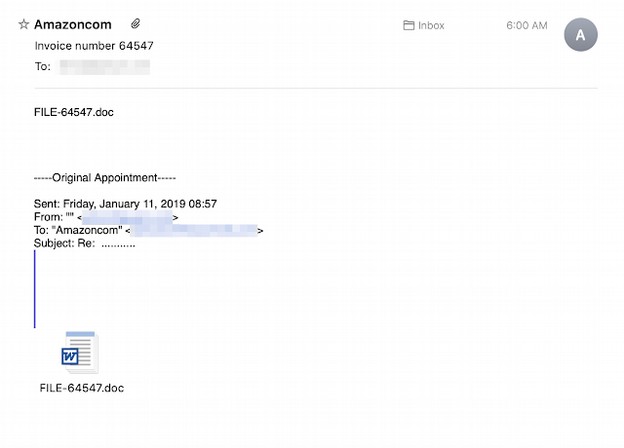
Here is another Emotet email. Does this look like spam to you?
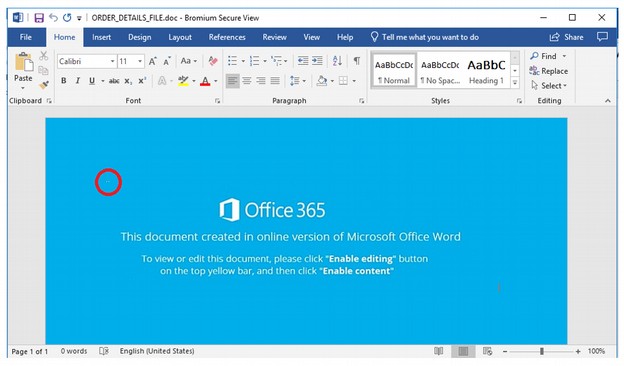
In the top left corner of the document is a tiny text box (Highlighted by a red circle in the image), so small it almost looks like a dead pixel on your screen. This edit box is where the changes for each malware infection are made. Can you see the small white dot? Neither can I.
Here is another Emotet example:
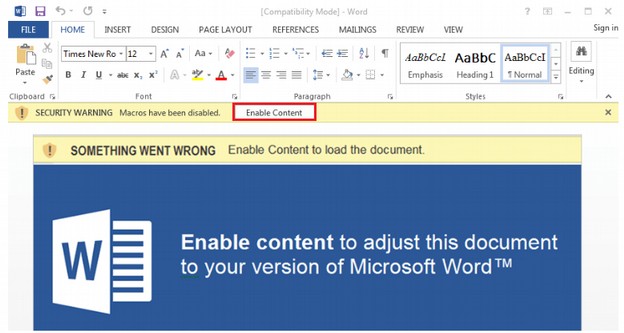
Emotet also uses URL spoofing to fool people to think they are linking to a major website rather than a fake website created to look like a major website.
Here are examples of malicious links:
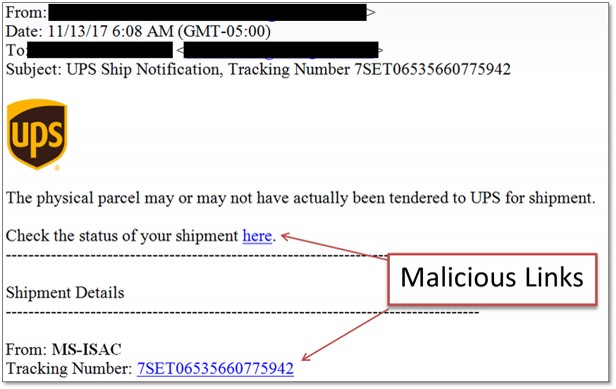
Another trick of Emotet is to claim they are the US Internal Revenue Service sending you a notice. Here are just some of their IRS notices:
From: Internal Revenue Service <[spoofed email address]>
-
From: Internal Revenue Service Online <[spoofed email address]>
-
From: IRS <
This email address is being protected from spambots. You need JavaScript enabled to view it. ; <[spoofed email address]>
-
Subject: IRS Tax Return Transcript
-
Subject: IRS Verification of Non-filing Letter
-
Subject: IRS Wage and Income Transcript
-
Subject: Payroll Tax Payment
Here is an example of an Emotet malicious email using an official IRS logo:
The Office 365 log in hack. Instead of logging into Office 365, your employees are logging into Emotet and Trickbot!
In an effort to increase their profits, a few years ago, Microsoft switched from a model where folks would pay a few hundred dollars to download a permanent copy of Office to a model where folks would rent an online copy of Office, called Office 365, which costs businesses $12.50 per month or $150 per year per user. So if a company has 100 employees, they could be paying $15,000 per year just to use Office 365.
Over time, Microsoft eliminated the ability of businesses to buy the stand alone version of MS Office. This forced the employees of all businesses to get used to logging into the online version of MS Office.
Paying thousands of dollars per year for Office 365 seems crazy when companies could be using a more secure open source tool called Libre Office to process all of their Microsoft documents for free. But the real danger in using Office 365 online is that employees get conditioned into logging into an Office 365 account in order to view and edit Microsoft documents. This makes them easy targets for Emotet email campaigns designed to trick them into clicking on a malicious link. Here is a quote from an article describing this problem.
“Office 365 phishing emails are one of the top threats attempting to be delivered to NJ State employee inboxes. These emails are often used to steal Office 365 user credentials by convincing a target to click on a link or open an attachment that directs them to a fraudulent Office 365 login page.
The “Update your Web Browser” Trick
Hackers have created sites that delivers an alert claiming the user’s browser – either Chrome or Firefox –needs to be updated. If the “Update” button is clicked, an executable will be downloaded that installs the Trickbot banking trojan. Trickbot is a sophisticated trojan with many capabilities that include stealing saved login credentials, browsing history, and form autofill data. Trickbot has been implicated in many recent cyber incidents, most notably infecting networks prior to the installation of the Ryuk ransomware.”
The latest campaign is targeting Windows 10 users and implementing a highly detailed and convincing, but fake nonetheless, Office 365 page to prompt for browser updates that install the Trojan itself.” Here is the Trickbot image warning you that your need to update Firefox:
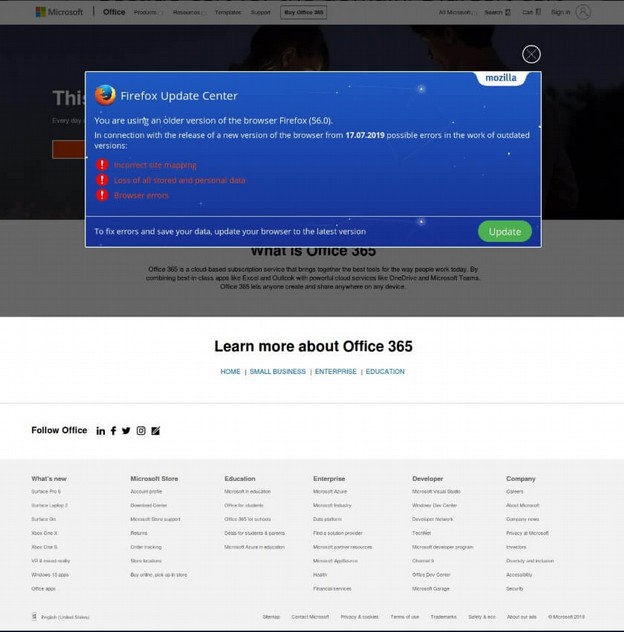
Clicking on some of the links takes you to a valid Microsoft 365 website. But clicking on the Firefox Update link installs the malware.
Here is another example of Emotet:
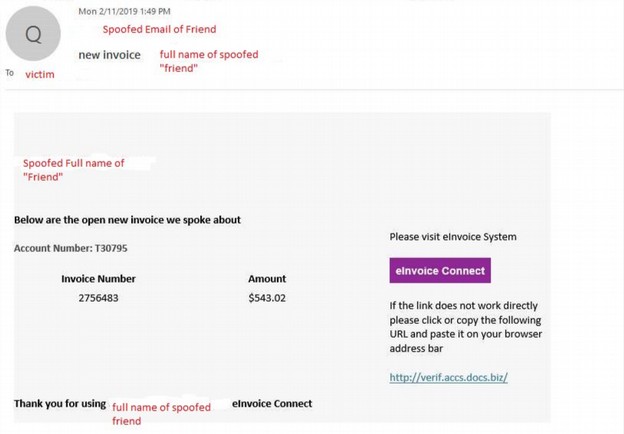
Here is another example of Emotet:
In February 2018, an Emotet attack on the city of Allentown PA cost more than one million dollars to clean up. Emotet had the email accounts and passwords of many city employees.
Employees were blamed for being “click happy,” But in fact, Emotet has evolved into a tool that can fool almost anyone. In this case, an employee received an email from someone claiming to be another employee.
According to one study, Emotet was downloaded by more than two million computers just in 2018.
A May 2019 report stated that Emotet
“accounts for almost two-thirds of all malware payloads delivered by email - with malicious URLs favored far more than weaponised attachments…the number of threats delivered my malicious URLs outnumbers those delivered by malicious attachments by five to one.”
Even clicking on a READ MORE link can cause an infection if you are using a Windows computer. Therefore clicking on any link or downloading any file from any Windows computer could cause you to become a victim of Emotet.
As for where these Emotet attacks are coming from, the overwhelming majority of attacks are coming from servers located in the US. And the overwhelming majority of victims are also in the US.
The real problem is not click happy employees. It is using Windows computers that are so insecure that all it takes is a single mistake by one employee to bring down a network of a thousand or more computers. If you use Windows computers, there is no “training” that can protect your employees or your organization from this scamming operation.
Emotet comes with Windows based Dynamically Linked Libraries – more commonly called DLL files - which it uses to contact Command and Control servers to let hackers know they have a new victim. With the latest version of Emotet, the hacker then sends an even more deadly cyber weapon called Trickbot which is used to spread the attack to other computers on the network. Now that you know more about how these attacks get started, let’s look closer at Trickbot which is the second wave of the attack.

