VIII. Mega Cortex… Ryuk Ransomware with a Kill Switch
Even if you do manage to protect yourself from Ryuk, hackers are constantly improving their ransomware. In fact, in early 2019 hackers introduced a new version of Ryuk called Locker Goga that is making Ryuk obsolete. Locker Goga uses multiple certificate authorities instead of just one.
Like Ryuk, Locker Goga uses Microsoft Server Message Block (SMB) protocol (aka Eternal Blue) and Windows Active Directory management services and MS Outlook to spread from computer to computer in infected networks. Locker Goga encrypts documents and PDFs, spreadsheets and PowerPoint files, database files, and videos, as well as JavaScript and Python files. Some hackers are downloading both Ryuk and Locker Goga onto the same infected systems.
What can be the purpose of using two separate encryption tools on the same system? Here is one clue. While there are ways to decrypt files that have been encrypted by Ryuk, (such as getting a key from the hackers after you have paid the ransom), there is currently no known way to unlock or decrypt systems and files that have been encrypted with Locker Goga. https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/what-you-need-to-know-about-the-lockergoga-ransomware/
In fact, Locker Goga makes it impossible to even boot up or log into your network after it becomes active because Locker Goga even encrypts your the Windows Boot Manager. And Locker Goga modifies the passwords of all users on the system. Trying to start your network simply displays the following screen:
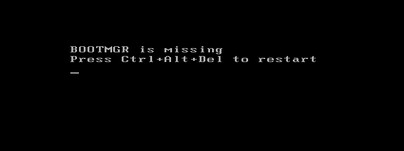
While many have pointed out that completely destroying your computer network is counter productive as it makes it harder or even impossible for you to pay the ransom, the threat of Locker Goga in fact makes it more likely that organizations will pay the Ryuk ransom rather than suffer the Locker Goga Sudden Death Kill Switch consequences.
Imagine using a backup to restore your files rather than paying the hackers. Now imagine the hackers still have access to your computer system by hiding in the UEFI BIOS. Now imagine they wait a few months and then hit you with Locker Goga. This is the predictable evolution of Windows based hacking tools. One Locker Goga attack cost its victim, a Norwegian Power System, more than $40 million.
Evidence to support my claim that victims of Emotet, Trickbot and Ryuk are more likely to become victims of even more advanced cyber weapons, an even newer type of ransomware called MegaCortex was reported in May 2019 which has similarities to Locker Goga. https://www.darkreading.com/perimeter/lockergoga-megacortex-ransomware-share-unlikely-traits/d/d-id/1334696
Here is a quote from this article:
“Researchers note this ransomware is mostly seen among businesses with existing Emotet infections, which can be used as launching points to distribute other malware… At least one of the C2 (command and control IP) addresses that MegaCortex contacts has also been used by Locker Goga.”
Like Locker Goga, MegaCortex uses a variety of signed and valid certificates to get past checking systems. At least one of the certificates was issued by an authority in London, UK. Some of the certificates were signed on March 14, 2019 and are valid until March 14, 2020.
Here is the MegaCortex Ransom Note:
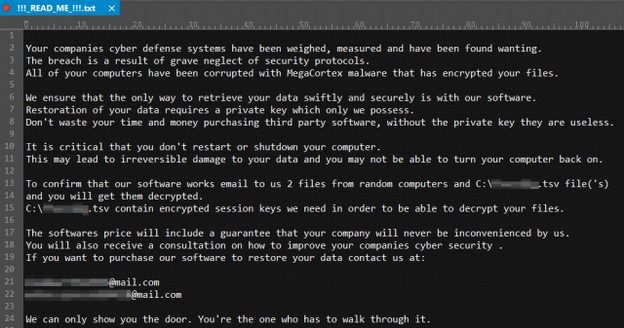
The IP address for this new attack was from a server in the Netherlands. Note that, in the ransom note, the ransomers themselves named their hacking tool MegaCortex. This is highly unusual. Normally hacking tools are named by the researchers who first report them.
A recent analysis of MegaCortex found that MegaCortex was revised on July 15, 2019 using a new and valid Thawte certificate issued to Abadan Pizza in London England. Here is a Google image of this location:

Then on August 6, 2019, a new version of MegaCortex, called version 2 was released. This new version is asking a ransom of $5.8 million to get your computers back. This is 10 times more than the highest ransom paid for Ryuk – making Ryuk seem like small potatoes. https://securityintelligence.com/news/megacortex-ransomware-v2-released-with-anti-analysis-features/

MegaCortex made it to the top of the Windows Ransomware Hit Parade with a successful July 16, 2019 attack against a noted cloud hosting provider called iNSYNQ – which is an authorized Microsoft and Intuit hosting provider for businesses using Intuit Quickbooks accounting software. iNSYNQ is located in Gig Harbor Washington.
iNSYNQ hosting includes automatic daily backups. However, it appears that backups of clients have also been compromised as clients have been warned to test their backups before using them. https://www.cyber.nj.gov/alerts-and-advisories/20190730/insynq-cloud-hosting-firm-confirms-megacortex-ransomware-attack
Nearly one month after the attack, the following notice still appears on their support page:

Here is a quote from a blog post the company issued about the attack:
“This continues to be difficult to navigate to say the least- malware attacks are an industry-wide phenomenon, that no one is 100% impervious to. Businesses large and small, individuals and even are own government have been blindsided by malicious actors in the recent months. We've received confirmation from security experts that we were hit with a sophisticated malware, relatively unknown to even experts in cyber security.”
What is amazing to me is that this company does not seem to be even remotely aware of the dangers of using Windows servers.
On August 5 2019, a security research group from IBM called X force issued a report on “destructive” ransomware such as Locker Gaga and Mega Cortex. The report stated:
“IBM X-Force Incident Response and Intelligence Services (IRIS) estimates that victimized organizations on average experience a total cost of over $200 million and have more than 12,000 devices destroyed in an attack. Recovery from destructive malware can also require hundreds of hours to remediate and rebuild environments that have been destroyed. The NotPetya malware that hit organizations across the globe is a stark example of the costly damage that destructive malware can leave in its wake. According to a White House assessment, NotPetya caused serious business disruption across geographies and resulted in more than $10 billion in total damages.”
“Since 2018, X-Force IRIS has been observing cyber criminals increasingly incorporate destructive components, such as wiper malware, into their attacks on commercial entities. This is especially true for cyber criminals who use ransomware like Locker Goga and MegaCortex to infect enterprise networks. Cyber criminals may be adopting these destructive elements to add pressure to their demands that victims pay the ransom—adding irreparable data destruction to encryption as a potential repercussion. In many destructive malware attacks, the number of workstations affected may be as high as three-quarters or more of the total network.”
“Ransomware attacks containing a destructive element have spiked in 2019, as new strains of ransomware such as Locker Goga and Mega Cortex entered the cyber crime arena. X-Force IRIS incident response data indicates that ransomware attack calls to our emergency response hot line have more than doubled over the past twelve months, with an increase of 116% from the second half of 2018 to the first half of 2019.”
“We’ve observed attackers reside in targeted environments for over four months prior to launching a destructive payload, giving them ample time for internal reconnaissance where they map out the infrastructure and find ways to achieve their objectives.”
“PowerShell, a Microsoft framework that is both a scripting language and a command line executor, first appeared in 2006 and has been a standard feature of the Windows operating system ever since. Power Shell scripting has been increasingly gaining popularity among adversarial actors since 2016 as one of the most frequently used lateral movement techniques observed by X-Force IRIS incident responders, and destructive malware attackers have followed this trend. Modern ransomware variants, such as MegaCortex, can use malicious PowerShell scripts to move between networked devices. PowerShell is native to the Windows operating environment, making it appear legitimate and thereby more difficult to identify as anomalous activity, which can further challenge detection and response.”
“As we move into the second half of 2019, additional cyber criminal groups—particularly those intent on conducting ransomware attacks— are recognizing the utility of having a wiping mechanism built into their tools. This type of mechanism can provide adversaries with additional options to pressure victims, while simultaneously increasing the risk of an attack that will require disaster recovery. This trend leads us to believe that more financially-motivated cyber criminal groups are likely to explore destructive malware as an option to incorporate into current attacks.”
https://www.ibm.com/downloads/cas/8ODXVKLJ
As further evidence that initial attacks can lead to further attacks, Louisville's federally funded Park DuValle Community Health Center paid a $70,000 ransom for an attack in April, 2019 only to be hit again in June 2019.
https://www.upi.com/Top_News/US/2019/08/07/Destructive-malware-attacks-have-surged-200-in-past-year-experts-say/1541565141297/
On August 16, 2019, at least 23 state agencies in Texas were hit by a “coordinated ransomware attack” just days after it was revealed that the city of Baltimore had to spend more than $20 million to recover from their ransomware attack. The majority of the 23 agencies were small local governments. All 23 attacks are believed to have the same source. The fact that this hacker hit all 23 state agencies at the same time is a strong indication that the system was compromised months ago and that hacker spent months planning this attack.
This is just the latest in an ongoing epidemic of data breaches and hacking incidents. The federal Department of Health and Human Services keeps a website listing all reported data breaches. In July 2019 alone, there were dozens of breaches affecting more than 30 million people. Many of these attacks are repeat attacks on the same servers.
https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
It is time to stop thinking of each of these hacking tools in isolation and start thinking of them as part of an evolution of NSA based Windows ransomware. Clearly, the Windows ransomware situation is rapidly evolving and becoming much worse over time.
In fact, as hackers get better at extracting money from their victims, Windows ransomware seems to be spiraling out of control. Therefore, the only way for victims of past ransomware attacks to really protect themselves from another Ryuk Ransomware attack (or an even more powerful ransomware attack) is to eliminate both the Windows OS that allows it and the presence of Xbot in your system BIOS. This means getting rid of Windows and its side kick UEFI BIOS.

