VII. How Emotet, Trickbot, Ryuk and Xbot Work
Getting someone to download malware is the easiest part of hacking a network. The harder part is transferring the malware to other computers in the network. The key is to have a willing predictable and not-very-secure host computer. This is where Windows computers come in. They have very predictable holes that are easily exploited. Specifically, the Windows operating system is the only operating system in the world that allows the web browser inside of the core of the operating system. Neither Apple or Linux have this not-so-hidden back door. I have covered how NSA-based malware gains persistence in my previous article noted earlier.
Here we will review how Trickbot transfers Ryuk Ransomware from computer to computer within the network. Conveniently, all Windows computers have a network communication protocol called Server Message Block (aka SMB). The NSA cyber weapon, Eternal Blue uses SMB in combination with Microsoft Outlook to transfer malware from computer to computer – almost as if this was what SMB was designed to do. WannaCry, NotPetya and Trickbot all use Eternal Blue and SMB and Microsoft Outlook to transfer malware from computer to computer.
It is important to note that initially Ryuk Ransomware is not installed on the victim computer. Rather first Emotet is downloaded onto a single computer, then Trickbot is downloaded onto the victim computer. Then Trickbot infects the rest of the computers on the Windows network. Then Trickbot performs a series of steps before deciding whether or not to download Ryuk Ransomware. Among these steps are stealing administrator passwords and determining the number and models of computers on the network as well as infecting all of the backup databases and files.
This information is sent back via command and control servers to the hackers who then research their potential victims ability to pay. If the hackers want persistence even after the ransom is paid, it is a simple matter to place Xbot inside of the UEFI BIOS chip on all of the computers in the victims computer network. Ryuk ransomware is then sent to infect the currently active database.
Here is a diagram of this process:
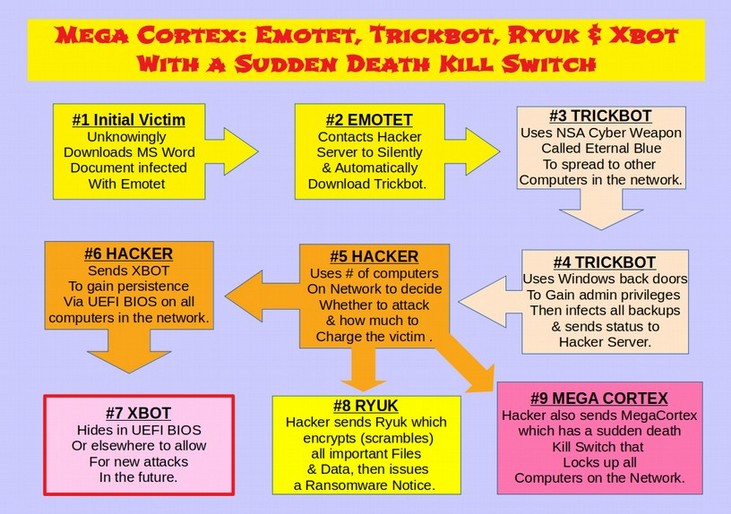
How Ryuk uses normal Windows Functions to Take Over and Encrypt the Network
According to a January 2019 Fire Eye Report, Ryuk Ransomware hackers have been active since at least December 2017. https://www.fireeye.com/blog/threat-research/2019/01/a-nasty-trick-from-credential-theft-malware-to-business-disruption.html
Curiously, the Fire Eye analysis found that the attackers performed host and network reconnaissance using normal built-in Windows commands such AdFind.exe. Here is a quote from their findings: “AdFind.exe was executed using a batch script, which was crafted to pass a series of commands that were used to collect information about Active Directory users, systems, OUs, subnets, groups, and trust objects… This process was performed twice on the same domain controller, 10 hours apart. Between executions of Adfind the attacker tested access to multiple domain controllers in the victim environment, including the one later used to deploy Ryuk… “
A Google search of the adfind.exe function reveals that it was originally developed prior to 2003 and originally developed for use on Microsoft Windows Exchange Servers. Adfind is still being actively developed with the latest version being written in Microsoft Visual Studio and released on October 31, 2017. Adfind still works on Windows Server 2019. In fact, Adfind is available for free download from this link: http://www.joeware.net/freetools/tools/adfind/
Adfind is free ware meaning there is no cost to download it. But it is not open source. This means that the source code is not available for public inspection. All of the Adfind commands can be found at this link: http://www.joeware.net/freetools/tools/adfind/usage.htm
Here is a link to Microsoft’s domain controller processes: https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-adts/8ebcf782-87fd-4dc3-8585-1301569dfe4f
Here is an article written in August 2006 explaining how to use Adfind. https://thescripter.wordpress.com/2006/08/10/using-the-excellent-and-free-adfind-utility-to-search-windows-active-directory/
The AD in Adfind stands for Active Directory. Here is a quote from the above article: “Running Adfind against your AD will provide you with a nice comma-separated dump of all your Contact object’s display names and primary e-mail addresses.”
Another article states: ‘Working with Adfind is not restricted by the local security measures.”
Another 2010 article states: “Adfind can be used to query the Active Directory for user accounts, groups, OUs, containers, Schema elements and other resources based on a variety of advanced search criteria. It is a command-line tool and once you have learned its command line options, it is rather easy to use.”
An April 2019 Fire Eye article stated that Adfind and other publicly available tools can be used to install “malicious Windows services to execute Power Shell commands on remote systems.” https://www.fireeye.com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
The hackers in question compromised one computer on the network (likely with Emotet). They then moved laterally through the system using the Windows Remote Desktop Protocol (RDP) likely with something similar to Trickbot and Eternal Blue. The hackers then used Adfind to get information from the Windows Active Directory. The information included Active Directory users, computers, organizational units, subnets, groups, and trusts. To ensure a high success rate, the attacker used compromised domain administrator credentials (which they obtained earlier through the use of Emotet and Trickbot). Domain administrators have complete control over Windows systems in an Active Directory environment. These ransomware attacks from just one hacker have cost victims tens of millions of dollars. The report then concludes with more than one dozen IP addresses used by the hackers. Most of the IP addresses were located here in the United States. But servers were also located in several other countries that are connect with the NSA Five Eyes system. Here are just a few of the IP addresses:
31.220.45[.]151 located in the Netherlands
46.166.173[.]109 located in Lithuania
62.210.136[.]65 located in France
103.73.65[.]116 located in Australia
185.202.174[.]31 located in the United States
185.202.174[.]80 located in the United States
185.202.174[.]84 located in the United States
185.202.174[.]91 located in the United States
185.222.211[.]98 located in the United States
Returning to the first Fire Eye article on Ryuk:“The attacker then logged into a domain controller and copied instances of PSExec.exe, a batch script used to kill processes and stop services, and an instance of Ryuk onto the system… Using PsExec the attacker copied the process/service killing batch script to the %TEMP% folder on hundreds of computers across the victim environment, from which it was then executed. The attacker then used PsExec to copy the Ryuk binary to the %SystemRoot% directories of these same computers. A new service configured to launch the Ryuk binary was then created and started. Ryuk execution proceeded as normal, encrypting files on impacted systems.”
In short, the Windows operating system normal functions were used to encrypt the files on the system. It is as if Windows is an accomplice in this crime.
My point in providing these links and quotes is to show that you do not have to be a Russian spy or North Korean hacker or computer genius to learn how Ryuk Ransomware works. The information is publicly available on the Internet and has been for over 10 years.
The Fire Eye report also noted that Ryuk has been found to lie dormant for up to a year before encrypting the files and sending the ransom note. There is not question that the reason it is lying dormant for so long is to make sure that all useful backup files have also been infected – rendering backups to be useless.
The goal of Ryuk in laying dormant for so long and corrupting the backup files is to leave victims with no other choice but to pay the ransom or lose all of their data. Therefore, by the time the victim receives the ransom note, which is often $100,000 or more, they have already been infected for months and it is likely than many if not all of their backup files have also been infected.
Paying the ransom is likely to only bring temporary relief as the hackers are still inside of the UEFI BIOS of all of the computers on the victim’s network. Also, hacking tools are evolving into ever more deadly strains over time. In the next section, we will cover the latest deadly strain of Ryuk Ransomware, called Mega Cortex, which is basically Ryuk Ransomware with a sudden death kill switch.

